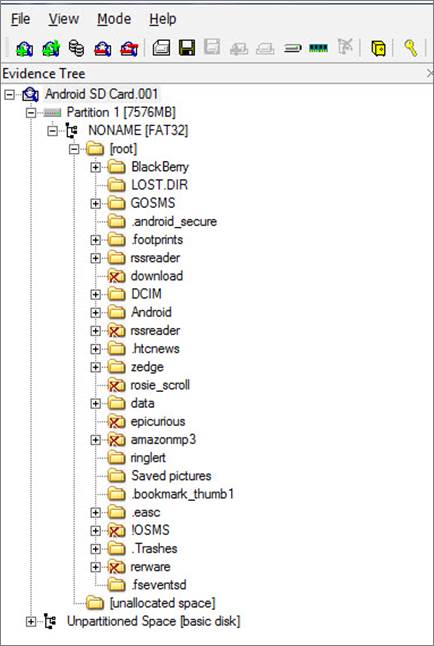
SD cards can store data in any format. Examiners must take this into consideration when conducting a forensic examination of an SD card. Smartphones, however, use the SD cards to store application data, user-created files, backup files, and possibly encrypted volumes. Depending on the smartphone, the data stored and acquired from the SD card may vary.
A full file system examination of the SD card should be conducted in your forensic tool of choice. XWAYS, Autopsy, Inspector, EnCase, or FTK provide access to all the files (deleted and active) on the media to include encrypted volumes. Mobile device forensic tools may be required for parsing third-party applications and phone backup files. Andrew Hoog, from viaForensics, references the use of SD cards in Android devices in his book Android Forensics: Investigation, Analysis and Mobile Security for Google Android.
The examiner should use tools that allow him/her to search by file extension, keyword search, mount files, and carve data that may reside on the media, but isn't being interpreted. Analysis for the Android portion of this SD card are covered in the corresponding sections of this course.
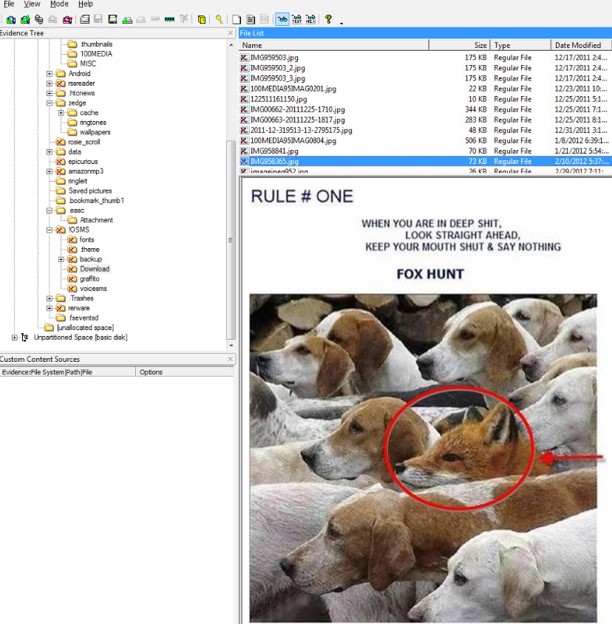
Deleted images may be recovered from the SD card. Depending on the SD card and the process for deleting the image, EXIF data may be recoverable. FTK Imager shows the deleted images from the SD card but may not display the EXIF data. Should you not find any EXIF data, it is best to export the image and attempt to recover the data using another tool or a hex editor.
Many smartphones contain microSD data storage expansion cards that are used for increased storage and functionality. These storage cards can contain data that has great evidentiary value.
Most MicroSD data storage cards are generally formatted with FAT file system; however, some are formatted NTFS, and some contain proprietary formatting. Many phones allow the user to encrypt data stored on the microSD card, and some of these cards are locked to the device they are installed in and are not readable outside the device. You may find that a microSD card has been used in several smartphones or other devices.
If possible, microSD expansion cards should be processed as you would traditional media, including the use of write protection devices. Processing data expansion cards while installed in a device may result in changes to the date and timestamps on the card, and so the cards should first be processed outside the phone, and then with the phone if you choose to see the data in its native context. Some expandable storage cards are locked to the device and are not readable outside the device and, therefore, need to be processed while installed in the device.
Some Android devices allow for external and additional internal storage. The standard SD cards range in size and can be added and removed from the device by the user. Once inserted, the SD card must be mounted for the Android to access the media. The Android YAFFS2 file system relies on external SD cards for additional storage. eMMC (embedded multimedia cards) were introduced with the EXT file system. The reasoning was to allow more internal storage that didn't rely on or use up the NAND flash memory. Keep in mind that the trend is no longer to use an SD card that can be removed from the device. ISP supports many eMMC devices. An alternative to ISP is to acquire the device as a USB mass storage device, similar to what your instructor will demo in the next few slides using FTK Imager.
Android devices may have removable batteries, but this is no longer the standard. Removable SD cards make the Android and iOS devices very different smartphones. This used to be one of the biggest differences in the two smartphones. However, Android phones don’t always allow for SD cards to be inserted as they have in the past. SD cards can either be physical (removable) or emulated, which makes forensic acquisition and analysis more challenging for examiners when trying to put together the puzzle pieces. Third-party applications can store unique data on the SD card and, if separated, the application cannot be fully parsed, depending on how the data is stored by the application. Acquiring Android devices with SD cards is a lengthy process. When time allows, we recommended the following steps:
If the phone is powered off, acquire the SD card first, using methods we will demo in the next few slides or by referring to the bonus material included within the media files provided with the course.
1. If the phone is powered on, acquire the phone with the SD card in it, even if the SD card is not mounted by the Android file system. You do not want to power off the device to remove external media if you made the choice to keep the device powered (i.e., preventing the device from locking or avoiding encryption).
2. Ensure that you have acquired the SD card separate from the phone as well as inside the phone, where time allows.
Make sure to document all steps to ensure that nothing is overlooked, and your methods are as forensically sound as possible. (For example, if the device was rooted during acquisition, this should be noted.) Keep in mind that a phone can only pull data from an SD card that the phone “understands.” This means if the user has tax documents or encrypted containers stored on the SD card prior to using it with an Android, this data could be overlooked during acquisition because the phone doesn’t understand that type of data. You, the examiner, need to make sure you make every effort to capture all data from the smartphone media. This means you should acquire the SD card as traditional digital media, in a write-protected manner, and not just through the smartphone.