The first step in manually analyzing a database is to locate the file of interest.
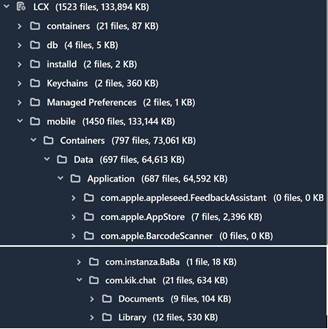
The example above depicts locating the database file that contains all of the message data for the Kik application installed on an iOS device. Data can be contained in one or more databases and other associated files: plists (iOS), xml (Android), and others.
The database (on the sample iOS device) was located by examining the contents of the file system in two main areas where application data is expected. This may look different depending on which forensic tool you are utilizing to display the file system.
Cellebrite: This is the true path to where the data resides
locally on a physical or jailbroken (FFS) iOS device:
private/var/mobile/Containers/Data/Application/<GUID>/
– Where GUID is represented by the application directory (Ex: com.kik.chat)
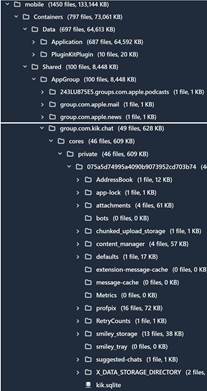
private/var/mobile/Containers/Shared/AppGroup/<GUID>/ – Where GUID is represented by the shared directory (Ex: group.com.kik.chat)
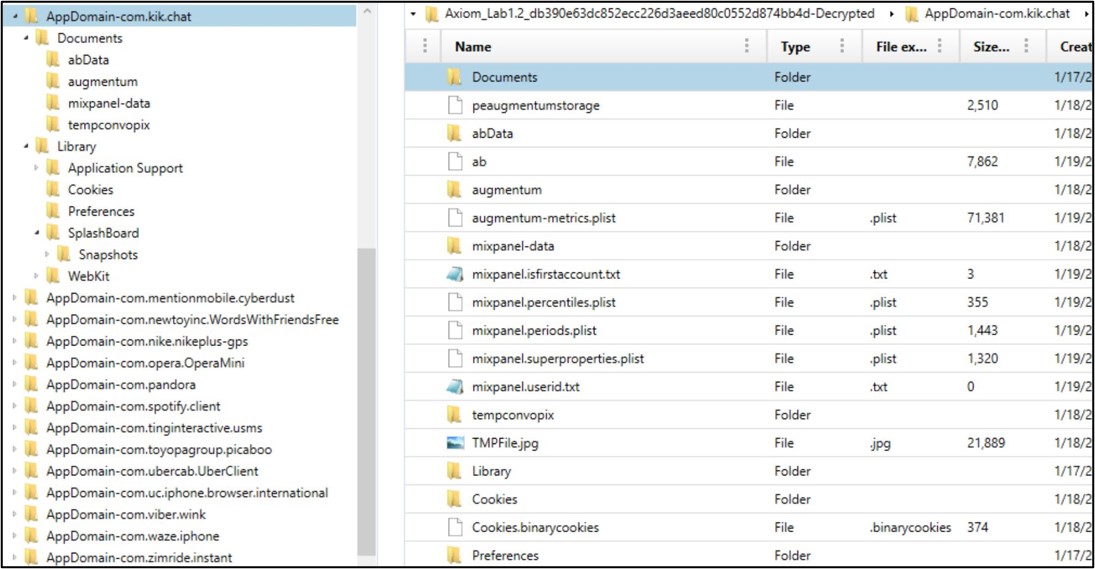
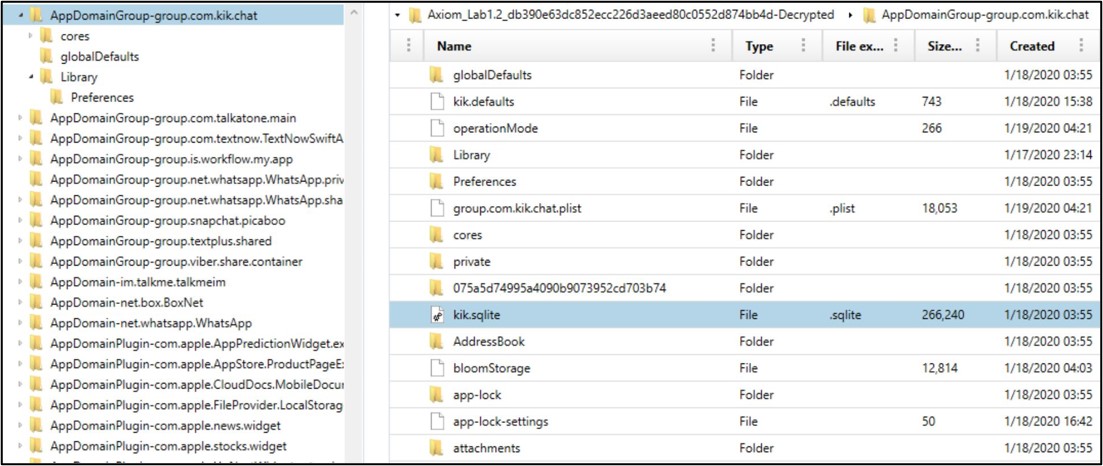
Axiom: Loading the same dataset into Axiom, you will notice that
the paths differ slightly as each artifact is referenced by its particular
“Domain”
AppDomain-com.kik.chat/
AppDomainGroup-group.com.kik.chat/
Neglecting to review the Shared (Group) directories would have meant overlooking the database that holds all of the important information.
Use this same approach to locate database files on the iPhone located in the mobile/Library, such as call history, address books, SMS, etc.
Cellebrite