Magnet Forensics did a great job discussing Direct Boot, file-based, and full disk encryption in this blogpost: https://www.magnetforensics.com/resources/android-nougat-forensic-analysis/. Full disk encryption is secure, but it’s bulky and may slow down the functionality on some Android devices. Essentially, devices with full disk encryption require the user to enter the passcode to initiate decryption, which can take time.
File-based encryption, similar to iOS, means that every file may be encrypted with a unique key. Thus, there isn’t a brute force, backdoor method to bypass the acquisition. This is bad because it often keeps us from a physical image. One of the more interesting parts of file-based encryption is the additional data storage locations. Two additional locations are created on the devices using file-based encryption:
• CE: Credential Encrypted
• DE: Device Encrypted
Credential Encrypted (CE) storage includes a System directory created under the Userdata partition on the device. This data is only accessible after the user enters the proper credentials to unlock their device.1 This makes the device more secure and enables multiple users to have accounts that are protected on the device.
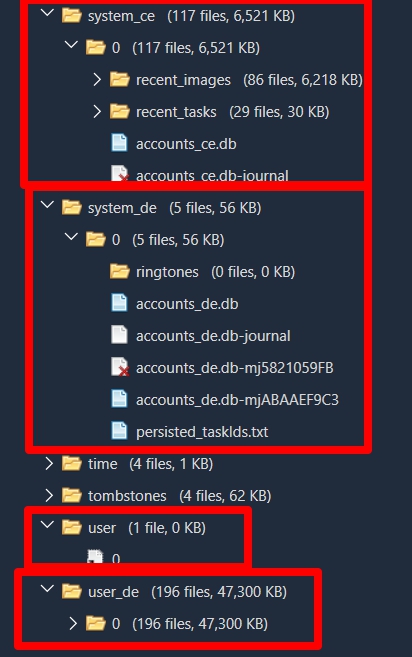
Device Encrypted (DE) storage includes both a system and user partition (system_de and user_de) that includes data available during Direct Boot. This location will store data accessible after the device is unlocked as well, which is expected. The application data stored in the DE directory can only access the CE data when unlocked and decrypted. Should you stumble upon a device not using file-based encryption, the CE and DE directories will always be accessible. To determine which applications are accessible during Direct Boot, examine the APK. If “android:directBootAware=true”, then the application will be “somewhat” active prior to the device passcode being entered.1
Extraction options include a Full file-system (CE and DE extraction) or Partial file-system/BFU (DE only). BFU stands for “Before First Unlock” and essentially means the passcode for the device is not stashed in memory or anywhere on the device. At this phase, biometric unlocks should not work.
Direct boot, however, enables the device to boot right to the lock screen and will even allow notifications to come through to the device prior to unlocking the phone. This is much more efficient, and most users seem to
prefer this method. Even though notifications from some applications are coming through to the device prior to the application data being decrypted, it is limited and depends on the application and the user-defined preferences/settings. The full passcode, PIN, or pattern must be entered before the user has access to all files on the device. Even on rooted devices, the file-based encryption stands, files are decrypted on the fly, and superuser access is granted as needed.
The screenshot below shows one of our test devices that has file-based encryption in use. For more detailed information on Android Encryption, check out the webinar provided by Heather Mahalik and Shahar Tal at https://for585.com/fde19.
Reference:
[1] https://for585.com/fbe (Encryption Explained)