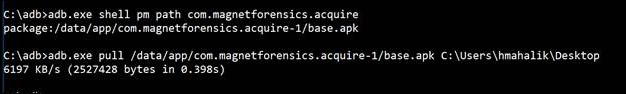
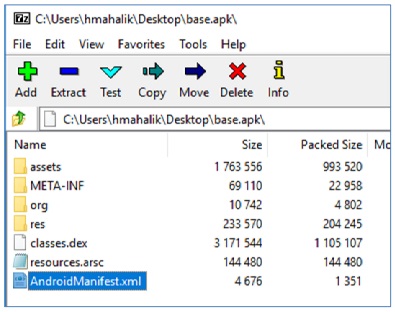
In this example, I went back to ADB and ran adb.exe shell pm path com.magnetforensics.acquire and received a response with the package information. From here, I was able to do an adb pull to extract that apk. Make sure you state where you want the apk to be saved. From here, I can dive into this application. If you havenít done this in the past, do not worry. This will be covered more in Section 4 where we discuss mobile malware. At this point, we are simply looking for the AndroidManifest.xml file. This file stores the permissions associated to the application. If we examine this file for applications that are installed on the device in order to acquire data, it will make our investigations easier. Why? Because we can testify (if required) to why the app was installed and what it was doing on the device. While this method of extraction doesnít contain the databases full of user artifacts, it provides a glimpse of capabilities, permissions, and more.
In order to know what the package is named, I followed the steps below:
1. adb devices †(makes sure your Android is connected and that you see the device and the serial number)
2. adb.exe shell pm list packages
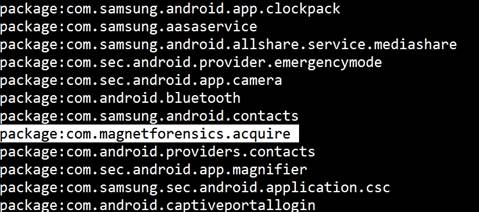
3. adb.exe shell pm path com.magnetforensics.acquire
4. adb.exe pull /data/app/com.magnetforensics.acquire-1/base.apk <output path>