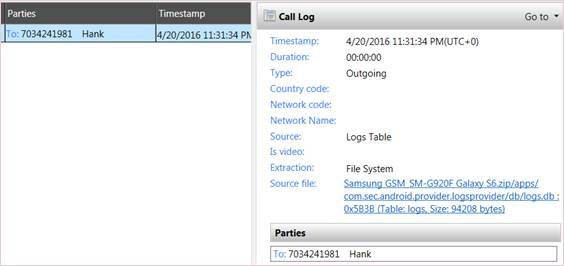
Samsung devices may store the call logs in the USERDATA/data/com.sec.android.provider.logsprovider/databases/logs.db. This database may not be parsed by your tool, which omits call logs from your report. The examiner must look for the call logs and may have to manually examine the data to recover all potential evidence. This database contains other information that may be relevant to the investigation and is not strictly reserved for call logs, so develop a query that works for you. Make sure you look for contacts2.db, calllog.db, and logs.db on all Samsung devices running Android v7 or later. NOTE that this file has not been located on Android 10, Android 11 or Android 12 devices.
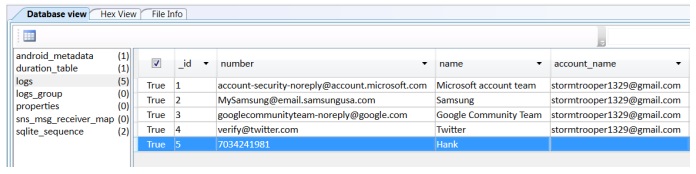
The USERDATA/data/com.sec.android.provider.logsprovider/databases/logs.db file should be manually examined on all Samsung devices where it exists. This file contains more than just call logs. It contains accounts used to verify third-party applications. It can track email accounts, phone numbers from calls, and more. Drafting a query for this database is at the examiner’s discretion, as it contains many tables, columns, and rows of interest. For calls, make sure to examine the logs table and ensure that all necessary columns are parsed. An example of a query for this table would include:
To pull call logs from logs.db, the following columns are of interest:
• The Number
• The Name
• Timestamp
• Duration of Call
• Type of Call
A simple SQLite Query for Logs.db would be:
SELECT
name,
DateTime(date/1000, 'UNIXEPOCH') AS "Timestamp",
Duration AS “Call Duration in Seconds”,
type AS "1=Incoming Call, 2=Outgoing Call"
From logs
This query is simply an example and will exclude all other activity outside of call logs. Simply start here and build onto your query to make sure you get all the data relevant to your investigation.
Reference:
Andrew Hoog, Android Forensics: Investigation, Analysis and Mobile Security for Google Android (Waltham, MA: Elsevier, 2011).