Google provides 15 GB of free storage space to users. Keep in mind this is available to even non-Android device users. Thus, Google cloud artifacts are likely to be relevant to most mobile investigations. Make sure you have proper authorization to access cloud data. If you overstep boundaries, you risk having your case thrown out and even ruining your reputation or your career. In order to use these tools, you must have the user’s Gmail address and password.
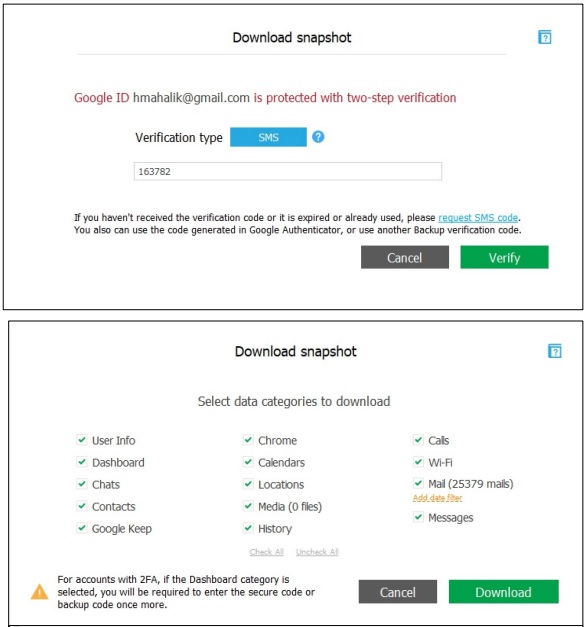
There are several tools available to pull cloud data. We are going to highlight Elcomsoft Cloud eXplorer in the next few slides. You have been provided a license for accessing cloud data. Try it on your own data or try it in a lab this week, assuming you have permission to do so. Keep in mind the user will be alerted if 2FA (two factor authentication) or two-step verification is set. If you are conducting covert operations, do not attempt to do this if you cannot risk the user being alerted!
Once you enter the proper credentials, you will be provided with a screen of what is available for extraction. NOTE, you may have to enter another secure code depending on how the device is set up. We recommend grabbing everything at this point if you are allowed to do so. The amount of information stored here is incredible! Just wait until you pull your first extraction. Locations are incredible if they are accurate. This is something you need to carefully examine for relevance to your investigation. We may have to get crafty to put the user at a location, which we have seen earlier in this section. For example, Wi-Fi artifacts—if the user cleared their network settings on the device, this may enable you to place the device at a location when “something” occurred.