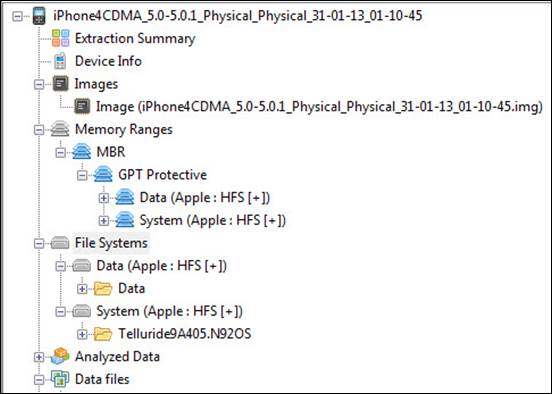
Chances are you may never see this type of acquisition unless a company or service provides you access, such as CAS. Chances are better if you are willing and able to jailbreak the device! Physical acquisition captures the raw file image, listed under Images in Physical Analyzer, as shown in this slide. This provides the examiner access to the entire raw Hex dump of the data pulled from the iOS device. NOTE: The only areas of unallocated space provided are the areas that can be decrypted by the forensic tool. Starting with iOS 4, encryption was enabled on the device. Older versions of iOS devices allow the full forensic capture of unallocated space for analysis and data carving.
The best and most comprehensive search should be conducted within the raw image file. The Memory Ranges are comprised of the Data and System partitions in their raw form, while the File System shows a normalized version of both the Data and the System partition, including a folder structure for each. The File System area of the data shown in Physical Analyzer is the reconstructed file system, as interpreted by the tool. Data is stored natively within the partitions and can be manually examined and decoded for relevance, which is discussed later in this section.
The Analyzed Data section in Physical Analyzer shows all data that Physical Analyzer knows how to parse. Again, use caution here and verify their findings rather than just trusting the tool. More details on how to verify your results and manually decode data are covered in the analytical portion of this section. The Analyzed Data section does not parse all forms of data available on the iOS device. The examiner must dig deeper to recover the overlooked data.
If the iOS device is locked with a simple four-digit passcode, iOS Physical Mode recovers the passcode for you on iOS devices released prior to 2011 (refer to the iOS Forensic Acquisition Support chart). If the iOS device is locked with a complex passcode, you can manually try as many passcodes as you like using Physical Analyzer or continue the extraction without being able to decrypt some of the saved passwords and email. Handling locked devices is covered in the next section. If the device isn't locked with a passcode, all data is extractable for iOS devices not using the A5+ chip.