The option to conduct an Advanced Logical/File System dump was introduced by Cellebrite. Other tools now offer similar access to the device. This type of acquisition requires that the device be unlocked. When conducting an extraction, encrypting the extraction will capture more data and is recommended. A comparison is shown in the next slide.
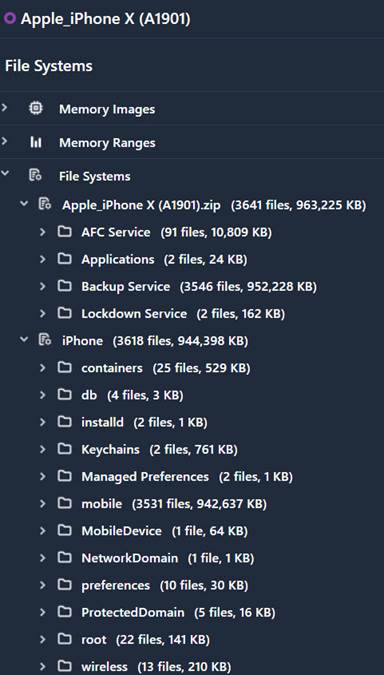
As shown in the screenshot, a normal (non-jailbroken) File System acquisition captures and provides access to the following data, all stored in one .zip file:1
• Apple File Conduit or Apple File Connection (AFC): The AFC is a service that runs on iOS devices and is used by iTunes to exchange files. The AFC is an option during a File System acquisition on the UFED Touch but is automatically captured during an Advanced Logical acquisition using Physical Analyzer.
• Apple File Conduit or Apple File Connection 2 (AFC2): The AFC2 provides access to the entire file system and the lockdown service. This is commonly captured on jailbroken devices, but the lockdown service file is captured during all Advanced Logical/File System acquisitions.
• Backup Services: Backup Services are essentially a backup created by iTunes that Physical Analyzer normalized for your ease of analysis. The data contained here include databases, plists, and other backup file data that can be manually examined and carved for data not shown in the Analyzed Data section of Physical Analyzer.
Essentially, a File System acquisition is a backup of all the data on the iOS device, including the raw files, but not the unallocated space.
As shown in the slide, a multitude of data can be captured using Logical or backup file acquisition. The Analyzed Data portion of Physical Analyzer is shown and reveals the data captured during a Logical acquisition of an iPhone 6s that was unlocked. In this example, email was captured. It all depends on the device! Email can be acquired and parsed on jailbroken devices during Logical and backup acquisitions. Again, deleted data may not be parsed, but it can be accessed if a backup file is created and the database files containing the raw data are accessible for carving.
Backup file forensics on iOS devices are covered in Section 4.
Reference:
[1] https://for585.com/iwiki