Cell towers and Wi-Fi provide solid location information for mobile devices. Apple is a bit more organized with how Wi-Fi is stored, and this information can be found in either /preferences.com.apple.wifi.known-networks.plist (iOS14 and iOS 15) and /preferences/SystemConfiguration/com.apple.wifi.plist for older iOS versions. When examining, make sure you look for key artifacts like SSID, BSSID, timestamps, password requirements, etc. The “HwMacAddressMacRandomisation” value is device's actual hardware Wi-Fi MAC address, not randomized. If device is being used as a mobile hotspot, connected devices can be identified here. Device's connecting to the mobile hotspot can be located within the nested keys of "InterfaceDataUsageV1“. These findings may help you place a suspect in a location at a specific time. A good reference is here https://ciofecaforensics.com/2020/10/24/apple-private-addresses/.
The file /root/Library/Preferences/com.apple.preferences.network.plist - Contains one boolean value for AirplaneModeEnabled (0 = No, 1 = Yes). In theory, this file can be checked to make sure the examiner had the device in Airplane Mode at the time of extraction. If value is ever 1, this may open the line of questioning about data integrity for not using Airplane Mode (unless other mitigations are employed).
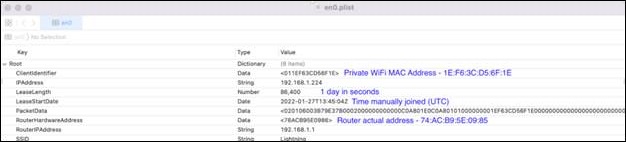
/private/var/db/dhcpclient/leases/en0.plist - The screenshot below is data from iOS 14.5.1. This is the Wi-Fi network connected to when data was extracted or the most recent Wi-Fi connection. Private MAC is close but has a leading '01' and the Router Hardware Address is correct except the first byte of 76 is actually 74 on the hardware, in this example. Last byte of address is explained by channel. Bottom line, the router information may be a bit off.
/private/var/root/Library/ApplicationSupport/com.apple.wifianalyticsd/DeviceAnalyticsModel.sqlite -
Contains a lot of information related to Wi-Fi including join and leave times, last seen time, geo-coordinates, signal strength, and more. Needs additional testing to validate the behavior of the join / leave times.
select
ZGEOTAG.Z_PK,
ZGEOTAG.Z_ENT,
datetime(zgeotag.zdate + 978307200,'unixepoch') as "Date",
datetime(zbss.ZLASTSEEN + 978307200,'unixepoch') as "Last Seen",
ZGEOTAG.ZLATITUDE as "Latitude",
ZGEOTAG.ZLONGITUDE as "Longitude",
zbss.ZBSSID as "BSSID",
ZNETWORK.ZSSID
from ZGEOTAG
left join zbss on zbss.Z_PK=ZGEOTAG.ZBSS
left join znetwork on znetwork.Z_PK=zbss.ZNETWORK
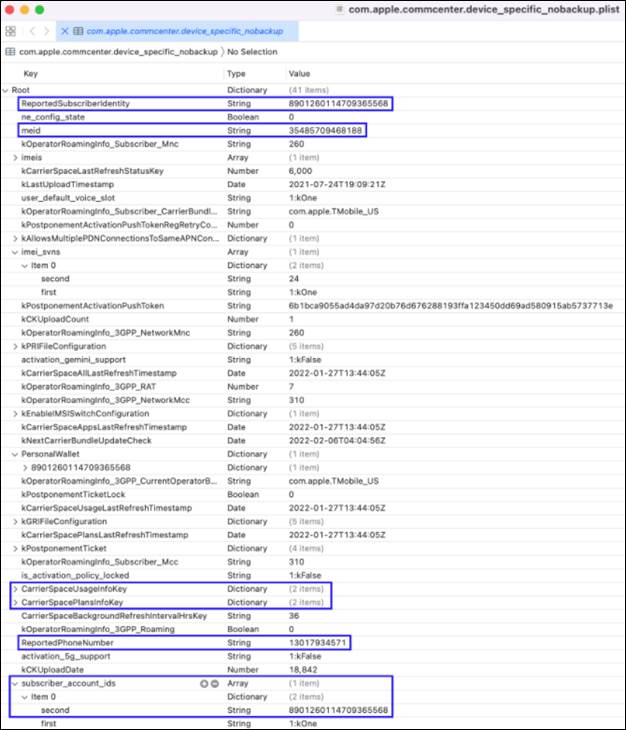
/private/var/wireless/Library/Preferences/com.apple.commcenter.device_specific_nobackup.plist -
Contains phone number, ICCID, MNC, MCC, and potentially information about the specific cellular plan subscribed to.
Another file of interest is /Library/Application Support/WiFiNetworkStoreModel.sqlite. The query below will parse this information for you.
select
ZGEOTAG.z_pk,
datetime(zgeotag.zdate+978307200,'unixepoch') as "Date Joined",
ZGEOTAG.ZLATITUDE as "Latitude",
ZGEOTAG.ZLONGITUDE as "Longitude",
ZGEOTAG.zbssid as "BSSID",
ZGEOTAG.ZHIGHERBANDNETWORK as "Higher Band Network",
ZGEOTAG.ZLOWERBANDNETWORK as "Lower Band Network"
from ZGEOTAG