GrayKey came out early in 2018, introduced by Atlanta, Georgia-based Grayshift as a law enforcement–only tool. The device can be connected to two iPhones at the same time. The devices are connected for about two minutes, after which they are disconnected from the device, still in a locked state. At some later point in time, the phones will display a black screen showing the passcode and additional information. The device is also supposed to be able to break passwords. Depending on the length of the passcode, it can take up to three days or longer for six-digit passcodes, and the time needed for longer passphrases is unknown.1 Law enforcement officials can request more information at https://graykey.grayshift.com. Cellebrite Premium2 is the box designed to unlock and provide Full file system access to both iOS and Android devices.
References:
[1] https://for585.com/m5e9q (Grayshift GrayKey write-up by Malwarebytes)
[2] https://for585.com/premium (Cellebrite Premium)
There were several methods and services for attempting to gain access to a locked iOS device that are available to everyone. Beginning in November 2014, a “black box”1, 2 came out in the phone unlocking/hacking community called the iP-BOX. This device (and its successors the iP-BOX 2 and iP-BOX 3) can be used to defeat four- and six-digit passcodes on some iOS devices through the iPhone 7, running some versions of iOS up to iOS 10. For some devices (running iOS 6), a process must be followed in order to set the device into “an infinite unlock condition” to run the iP-BOX, but other versions of iOS require no further exploit.
For iOS 6 devices, to access the infinite unlock condition, follow these steps:2
1. Access the Emergency Dialing interface and dial 112.
2. Press home key to get back to interface “Slide to Unlock.”
3. Press the bottom of the keyboard.
4. Slide the screen up to get to the calculator.
5. There appears a green stripe on top of the screen, which shows “the line is busy now.”
6. Press the green stripe indicator to get back to the calling interface. In the middle of the screen, there is the address book.
7. Press the home key and address book simultaneously to access the infinite unlock condition.
8. Connect iP-BOX to the phone, move the sensor to the screen, and press the black key of the equipment to unlock.
This process requires that the phone is out of Airplane mode and that a call to the 911 Emergency center might be completed. Obviously, this is not an ideal situation because you will be adding to the call history on the phone, are connected to the network, and are directly interacting with the phone. This is a deviation from a normal forensic process, but in the event that it is the only option, such deviation may be necessary to defeat the device lock. If you need to perform these steps, be sure to document your actions carefully!
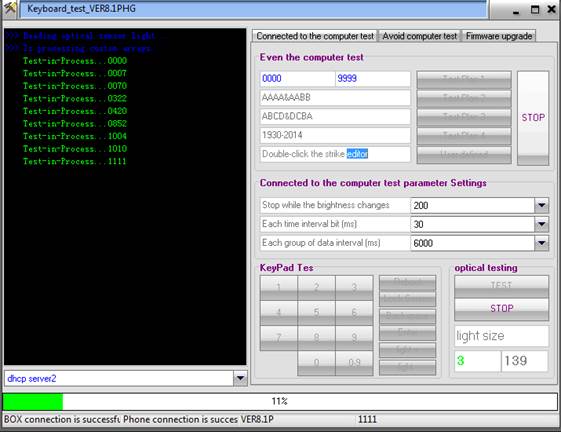
IP-BOX devices of all versions consist of the box itself, old and new iPhone cables, an optical sensor, and the associated software. The device can be operated either in a standalone fashion after being set up via the software, or it can be connected to a computer during operation.3
The iP-BOX software is used to configure passcode test patterns. The user can choose from several free patterns, such as a birthday attack (which contains patterns that match DDMM/MMDD) or all numbers between 0000 and 9999 or can create a custom number-based dictionary attack. Each attempt takes approximately 6 seconds to perform, and so the dictionary containing all numbers between 0000 and 9999 would take between 6 seconds and approximately 17 hours to complete. Custom dictionaries can cut down on the amount of total time used to attack the passcode and may be used before a full attack if desired. Six-digit brute force attacks using newer versions of iP-BOX can take far longer.
The optical sensor is the tool’s trigger to signal success because when a correct code is encountered, the screen changes and the background light output changes. The box signals success by beeping and flashing. If the optical sensor is placed in the wrong place or the screen is touched and changed by the user during the attack process, the box may stop and provide a false success signal. To restart the attack, simply press the button twice to restart the attack at the next sequential number.
The software is then used to interface with the box and load the chosen test patterns for an offline attack of the device, or the attack can be run directly using the software through the box to the phone. The screenshot on the previous page shows an attack in process using the software through the box to the device. A custom passcode list is being used in that example.
If the attack is allowed to run completely and fails, try slowing down the interval between attacks and restarting the attack. Also, if you used the software through the device for the original attack, try rerunning the attack with the box only, or vice versa.
References:
[1] https://for585.com/hack
[2] https://for585.com/teelbox
[3] https://for585.com/pef
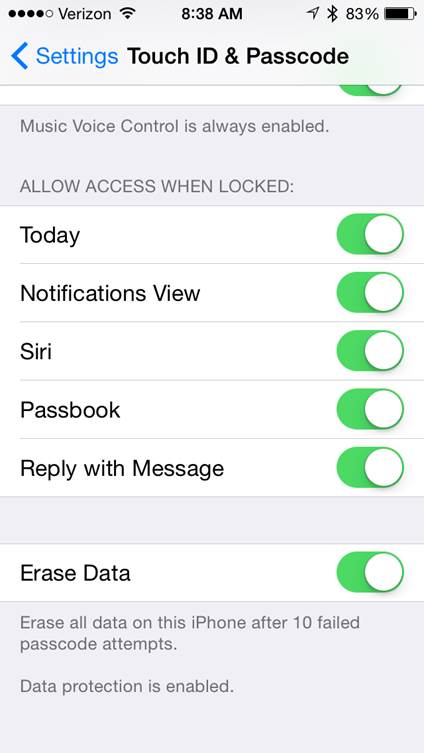
The fear of wiping a device after guessing too many times is a valid concern. Here is what that setting looks like.