The first step in searching for traces of Siri use should be to validate if the user was using Siri. To do this, simply search for “Siri” in the tool or navigate to Library/Preferences/com.apple.SiriViewService.plist, as shown in this slide, and verify that Siri is active. Once validated, you must think of ways Siri is used. For example, if she is used to set a reminder, that data should be stored in the same location as tasks or calendar items. If she is used to get directions, the information is stored with the maps or within the app she used to get the directions. Thus, it’s a needle-in-the-haystack search!
Consider some aspects of the “Hey Siri” feature. Even on a locked device (if Siri is enabled this way), you can ask Siri to send a text, update your Facebook status, call someone, and even request addresses. Although this isn’t a forensic solution per se, it is a method to access data on a locked iOS device that is otherwise useless for your investigation.
/Library/Preferences/com.apple.assistant* is another file that may be useful here.
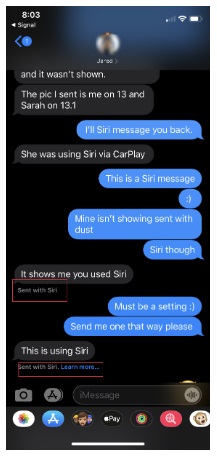
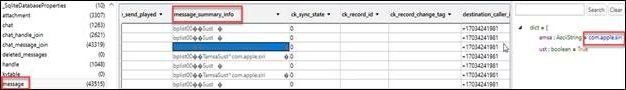
If the user leverages Siri to send an SMS message in iOS 13, there will be a BLOB in the column “message_summary_info” that contains “com.apple.siri” which means Siri was leveraged to send the message as shown in fine print on your iPhone message screen.