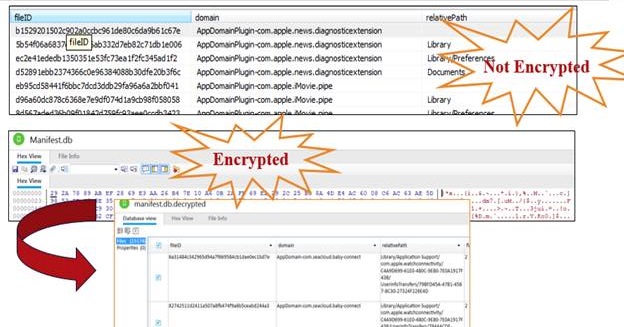
iOS 10 introduced a new format for the Manifest as well as encrypting the database if the user selected to encrypt the backup. In the top screenshot, we simply opened the Manifest.db and found that the data was not encrypted. The data within this file is the same as it was with older iOS versions contained in backups. The second screenshot is an encrypted backup, which contains an encrypted Manifest.db. This file can be decrypted with the proper password or with your forensic tools. Physical Analyzer automatically decrypted this database when the password for the backup was entered during the ingestion phase. For more information on what has changed in iOS 10 – iOS 15 backup files and the support provided by your commercial tools, refer to Heather Mahalik’s blog at https://smarterforensics.com/blog/.
Pre- iOS 10 backup Manifest.mbdb structure is shown below.
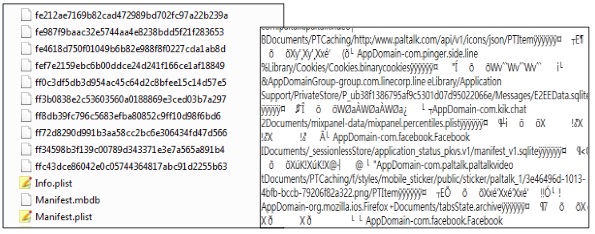
iOS backup files created prior to iOS 10 are shown in the screenshot on the left. These backups are comprised of files named for their name, path, and domain, as well as .plist files and the Manifest.mbdb.1 The Manifest.mbdb contains a list of files included in the backup. This file is not encrypted when the backup file is encrypted by the user. Thus, you can always examine this file for forensic artifacts relevant to your case. It may be a simple file listing, but it could point out an artifact you were looking for. In the example on the right, Hal Pomeranz’s script was used to parse the Manifest.mbdb. Let’s say this backup was encrypted and we could not access any data because the password couldn’t be cracked. When we parse this backup, we learn a few things about the device. We can see that apps are used on the device, such as Facebook, PalTalk, Firefox, and more. More importantly, if we kept reading the Manifest.mbdb results, we would be able to see that Cydia is set to push to the device. This device is jailbroken! Use the UDID of the backup folder along with the Info.plist file to see if you can locate the device and obtain a file system or full physical image of the device, regardless of the passcode.
Reference:
[1] https://for585.com/iback (iTunes Backup description on the iPhone Wiki).