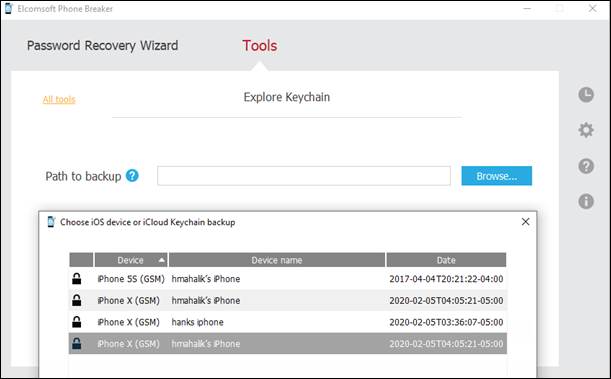
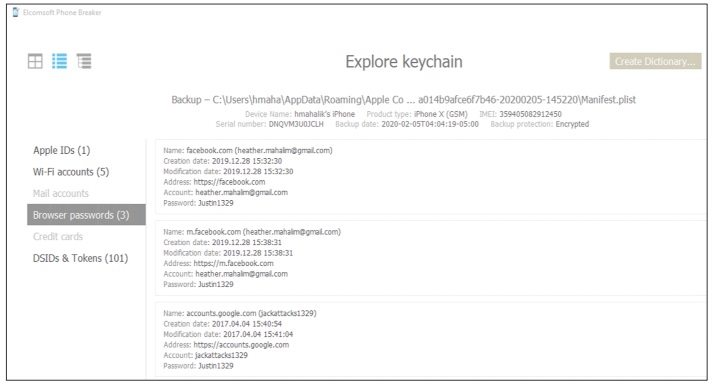
There are additional features built into the cloud extraction tools that may assist in your investigation. Keep in mind, you need authority to access these features. The example above is the Explore Keychain feature from Elcomsoft Phone Breaker. Here, we are loading a backup of interest. If the backup is encrypted (which is required for the keychain to be present in the backup), the backup password must be entered. Once entered, the keychain is decoded and displayed, as shown on the right.