Consider that any of the carrier-provided family monitoring tools can be effectively used as spyware applications when utilized beyond their intended purposes. These services are activated by an authorized individual on the mobile account and are designed to work with the phones they’re being used to monitor. Like many other spyware applications, carrier monitoring tools generally consist of an application installed on the phone in conjunction with an internet-based portal login. In some cases, the phone may come from the carrier with the monitoring software installed, but it is not activated until the service is activated by the carrier. With the proper legal process served to the provider, information can be obtained about whether family monitoring plans are actively being used.
All U.S. mobile carriers have parental controls that are almost identical. Each offers the capability to:
• Block picture messaging
• Block unknown phone numbers
• Limit what time your kids can text or call
• Filter web browsing
• Use GPS tracking to monitor physical location
Some of these features can also be used similarly to spyware.
The debate over what counts as monitoring a loved one versus spying on them is one that is ongoing. For a discussion on the pros and cons of parents monitoring cell phone use, see https://for585.com/3ozrk.1
As previously stated, there are a large number and variety of apps (many of them free) on the Play Store and third-party app stores that are designed to be used as spyware applications for monitoring phone usage, location, and communications.
It is not possible to describe all the artifacts that could be present from these applications, and they may not show as icons on the phone on which they are installed. It is necessary to carefully examine the file system of a device suspected to be compromised by spyware applications to locate any apps that might be monitoring phone activities in a clandestine manner. Additional .ipa and .apk files are available for practice within your course media files.
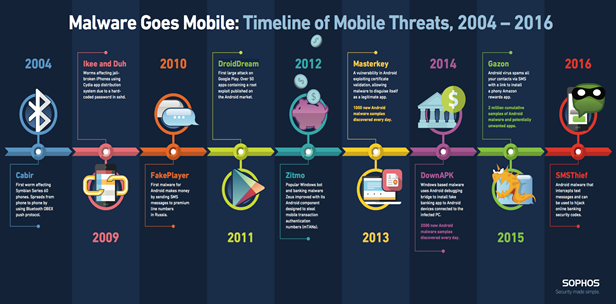
It’s been more than a decade since the first detection of malware threats to mobile devices, and the threat has changed significantly in the intervening years. As mobile technology gets more sophisticated and users depend on their mobile devices for functionality, the threats have become more technically sophisticated. We can expect to see additional changes as technology moves forward and changes; therefore, learning the skills it takes to address mobile malware threats is important.2
References:
[1] https://for585.com/3ozrk
[2] https://for585.com/n4slp (Sophos mobile malware timeline)