The reality of today’s mobile investigations is that it is getting increasingly difficult to find traces of user data on devices, as more applications are storing the bulk of their data in the cloud. You may still find databases of interest and configuration files that can provide evidence that file sharing was in use.
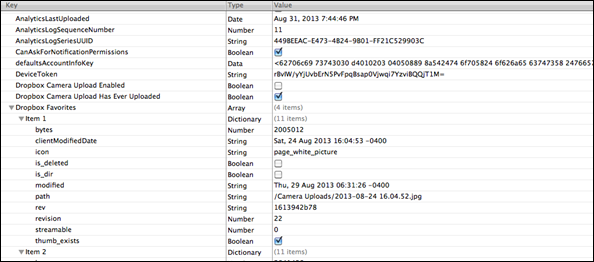
The screenshot above is a relevant database from a non-jailbroken iOS device. Even from an iTunes backup, we can tell that Dropbox was utilized. From just this database alone, we can gather several pertinent artifacts:
• The account ID of the user who was uploading data to Dropbox
• Filenames
• Folder structure of the user’s Dropbox cloud
• Timestamp associated with the action
• The source of the file
Dropbox is actually storing much more data to the device memory. In fact, the spotlight.db file is just a glimpse of the data available on a user’s Dropbox page when they accessed it. There are several other databases that are utilized to store the bulk of data to include items deleted from Dropbox, but without a jailbreak or root-level access, you may have to use what you have as a starting point.
In older devices, plist and XML files which would typically contain configuration and user/application preferences, was also utilized to store artifacts associated with file uploads as shown in the below iOS example.