Researching mobile banking applications that receive heavy usage on a personal device confirmed that they were storing very little PII to the device itself. In fact, throughout the years, applications seem to be storing even less data than ever before in these applications. This includes not only what we can see from a filesystem or logical acquisition, but it includes the rooted and jailbroken filesystem representations as well. This is the type of security protections in place that we should be happy to see from a user stand-point.
In almost all cases tested, any data that would have been captured by an operating system-type snapshot as well has also been obfuscated, something that you can test from a user-perspective on your own device by navigating but not closing out of the application and then going back to it. A splash screen or logo is often in place of the content that you had been viewing, but once the application has moved back to the foreground, you seemingly pick up where you left off in that session if it’s still active.
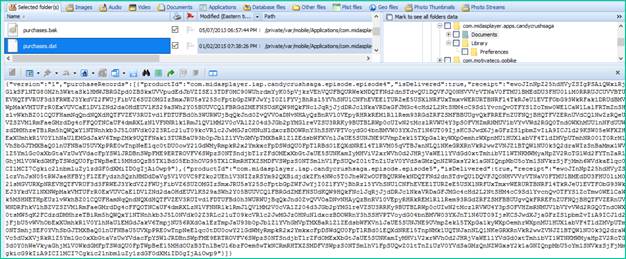
In-app purchases allow for a “store” to be embedded within the application so that add-ons, updates, and new features can be delivered almost seamlessly to a user by having them simply authenticate the purchase by entering their credentials. This in-app profile is commonly used for gaming and music applications. In the slide’s example, the in-app data for the game Candy Crush is stored in its encrypted format in the file purchases.bak.
Output from the spreadsheet below has been redacted to protect the user’s location information.