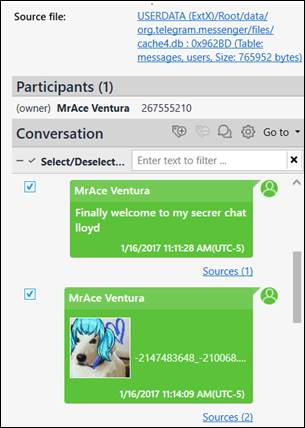
The example above depicts a rooted Android device. With root access, the messaging database is available in unencrypted form. Like many other secure messaging and ephemeral applications, Telegram, similar to FB Messenger, uses BLOBs to store message data. Both regular and secret chats can be retrieved from the database if the message is still active at the time of the acquisition. This is very common for ephemeral messaging applications.
Active images that have not been set to self-destruct are often stored in appropriately named sub-directories like the following for Android:
• USERDATA/Root/media/0/Telegram/
• Telegram Audio
• Telegram Documents
• Telegram Images
• Telegram VideoT
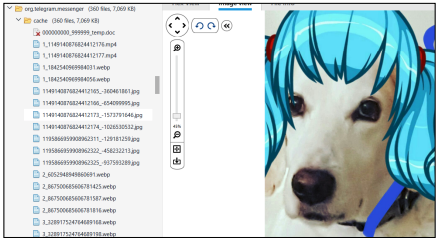
The self-destructing images are often stored in the cache directory and may be available even if your device is not rooted (or jailbroken as we saw previously with iOS).
The path USERDATA/Root/media/0/Android/data/org.telegram.messenger/cache contains media files, including those that have already been viewed or have been set to self-destruct.
Commercial forensic tools handle Telegram well, but there are many scripts that will parse out relevant information as well like https://github.com/RealityNet/teleparser and the python scripts made available on your FOR585 VM in the Scripts for Class folder on your desktop.