Our suspect seems very careful with leaving traces behind, especially when it comes to tracking him down and identifying locations visited. In this lab, we will use the evidence found on his USB, which we found recently in one of the motels he was staying in. We will focus this time on extracting and analyzing EXIF data instead of file headers like we did in previous labs. We will also see how useful EXIF data is when analyzing files and especially photos. Analyzing EXIF data is extremely important especially in our case since we want to track down our suspect. EXIF data analysis is not useful just for tracking, but if you have a child abuse/pornography case or any other case that involves digital photos.
Extract and analyze EXIF data from files of interest
Extract and analyze EXIF data from photos
Identify GPS coordinates using EXIF data
How to use different tools to analyze EXIF data
How to identify location and time when a photo was taken
Generate a report of your findings
In this part of the lab we are only required to extract the file type from the files we have on the suspect's USB [you can find the suspect's files at C:\DFP\Labs\Module3\Lab4]. I will be using Windows but you can use Linux to solve it easily too.
Let's now leverage exiftool's -filetype flag to extract the file type from the suspect's files. Simply open a cmd.exe terminal and execute the below, against each file in the Lab4 folder.
# cd C:\DFP\Tools\Metadata
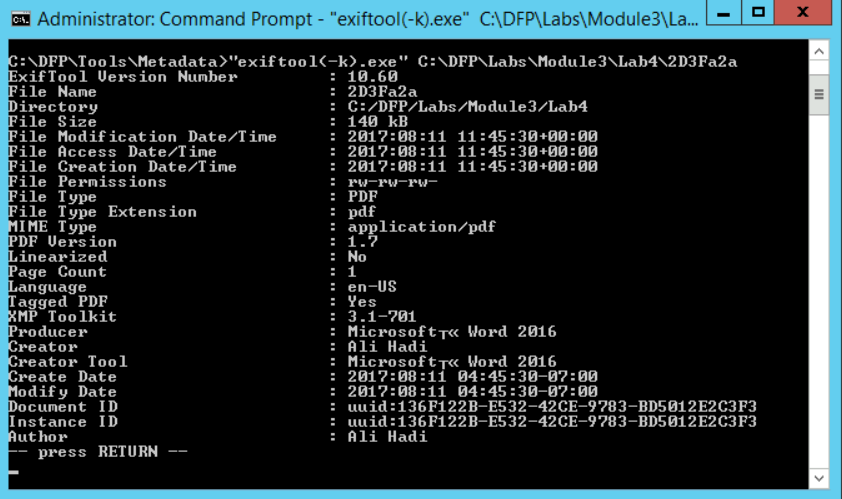
# "exiftool(-k).exe" -filetype C:\DFP\Labs\Module3\Lab4\2D3Fa2aNote: the output has been modified to fit this report without affecting the final understanding required.
2D3Fa2a File Type : PDF
AW3DXW File Type : JPEG
Mx#234 File Type : PPT
XFaWxVa File Type : PDF
ZC2f2d2 File Type : XLSX
Alternatively, on Linux, you could do the following, to speed things up:
# find -type f -print -exec exiftool -filetype {} \;The command above searches for all files within the current working directory and prints the name of the file that was filtered based on the results of the exiftool utility (those results contain the file type). If you noticed, we asked exiftool to specifically print the File Type and not all of the EXIF information. So, as you can see, by now we have two basic ways of identifying a file; one using the Linux "file" command and the other using the "exiftool" utility.
In this part, we were asked to extract the Tool Version, File Size, File Creation Date, File Type, Producer, Creator and Author, and finally the Product information out of the files we found. For understanding purposes, we will focus on the five different files below:
The basic way of using the exiftool utility on Windows, is similar to the command used below:
# "exiftool(-k).exe" C:\DFP\Labs\Module3\Lab4\2D3Fa2aAs we saw in the previous part of the lab, this was a PDF file, and we found the following interesting information:

From the snapshot, we can gather the following useful information:
Now, let us move on to checking the rest of the files and see what we found in each:
# "exiftool(-k).exe" C:\DFP\Labs\Module3\Lab4\AW3DXWIt was found that this is a JPEG image file with lots of useful information. Let us write down the basics:
Those were only the basics, but we found other useful information such as the following:
Let us move on to our third file.
# "exiftool(-k).exe" C:\DFP\Labs\Module3\Lab4\Mx#234The results could be seen in the snapshot below.
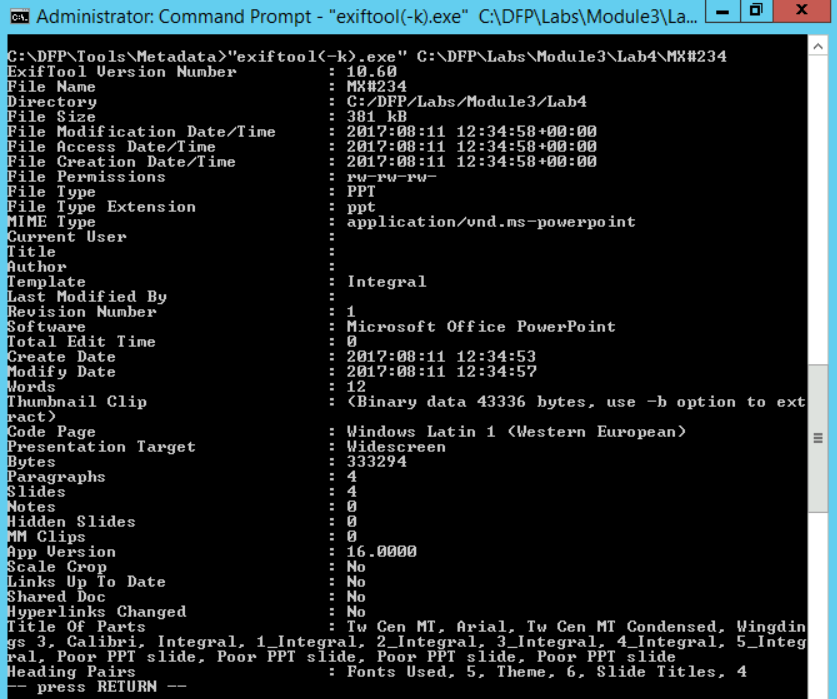
Here we have the following useful information:
First, the "Title" tag shows "PowerPoint Presentation," maybe not very useful, but it is good to check too. The "Software" used to create it was "Microsoft Office PowerPoint," has no hidden slides and the "Presentation Target" is a "Widescreen." Another important detail here is that we could also see the file was last modified by the author himself. So, the "Last Modified By" tag could come handy in other investigations, keep that in mind.
Let us check the fourth file:
# "exiftool(-k).exe" C:\DFP\Labs\Module3\Lab4\XFaWxVaHere we have the following useful information:
Now, a 1-page document might not always be malicious, but for example if the pdf document was supposed to be a proposal, then a one-page document is truly "suspicious".
Our final file is:
# "exiftool(-k).exe" C:\DFP\Labs\Module3\Lab4\ZC2f2d2Here we have the following useful information:
For this task, I won't be using the "exiftool" utility to solve the task, but another tool named "ExifReader" [located at C:\DFP\Tools\Metadata\exifr300_e]. I'm going to do that for two reasons; the first is that there always will be different ways and tools to solve a problem, and second, is to introduce you to ExifReader.
In this task, we have a couple of photos [located at C:\DFP\Labs\Module3\Lab4\pics] and we want to get an idea of the following:
So, let us get started. We discovered six photos, let us check each one of them and see. Using ExifReader is very simple, all you need to do is either use the "open" button and navigate to the location where the photo of interest is found and select it, or just drag-and-drop the photo on top of the application and it will open it for you.
[IMPORTANT NOTE:]
The photos used in this task are only used to help understand the importance of EXIF information found in photos. The photos and people names used do not derive from a real crime or investigation. No harm is meant, this is for educational purposes only.
Opening the first photo "DSCN0025.jpg":
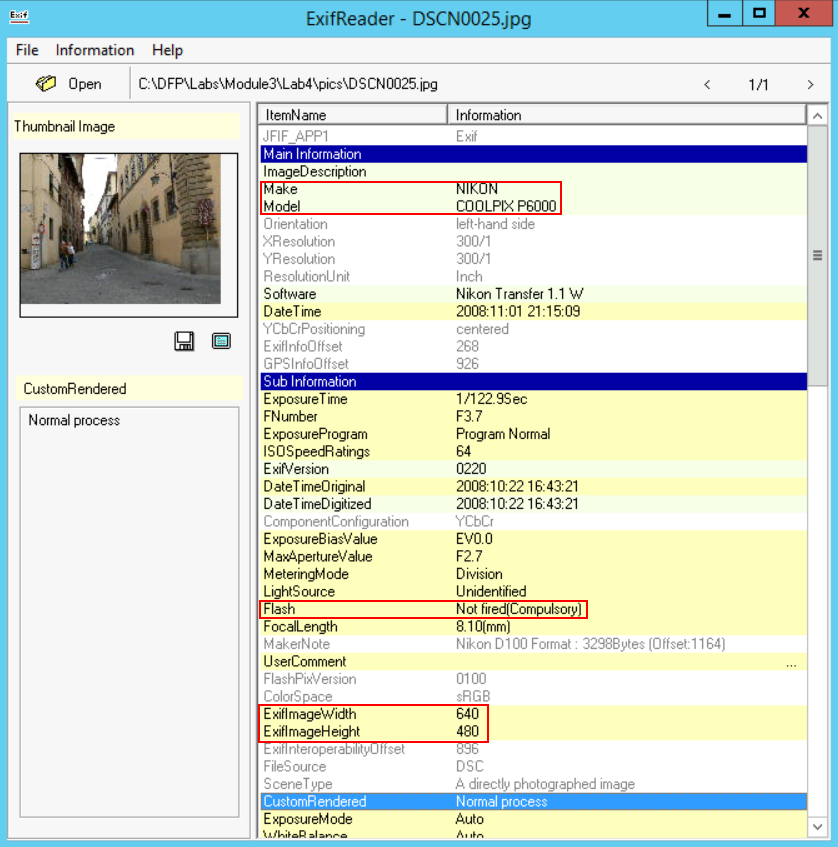
From the snapshots above, we can clearly answer the questions required:
From the "Make" tag, we can identify the camera manufacturer: Nikon
From the "Model" tag, we can identify the camera model: COOLPIX P6000
The "Flash" tag gives us an idea whether the flash was used or not, here it wasn't
It doesn't seem that this is a camera of a cellular phone
Now regarding GPS information, let us check that part:
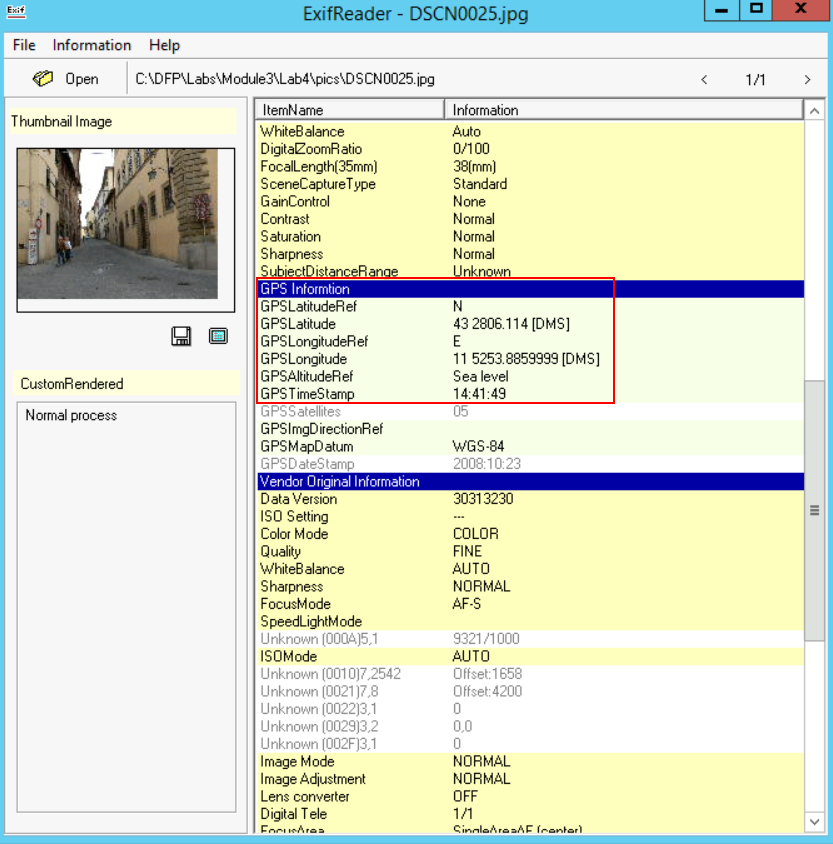
Based on the "GPS Latitude" tag, we found: "43 deg 2806.114'" North
Based on the "GPS Longitude" tag, we found "11 deg 5253.8859999'" East
The photo was taken at "2008:10:23 14:41:49" and yes there was a thumbnail embedded within this photo.
The width and height of the photo are "640x480"
If you take these GPS coordinates and use Google Maps, you could identify the location where the photo was taken. This is extremely helpful in crime scenes or in cases where photos could be used to locate the suspect.
Now, if you noticed when checking the results, there are tags or item names that are unknown. This I believe is due to the fact that the tool has not been updated for a very long time. Now if we go back to exiftool and run it against our photo, we shall get more clear details and results.
You can save all the information you extracted to a Text or CSV file as seen in the snapshot below:
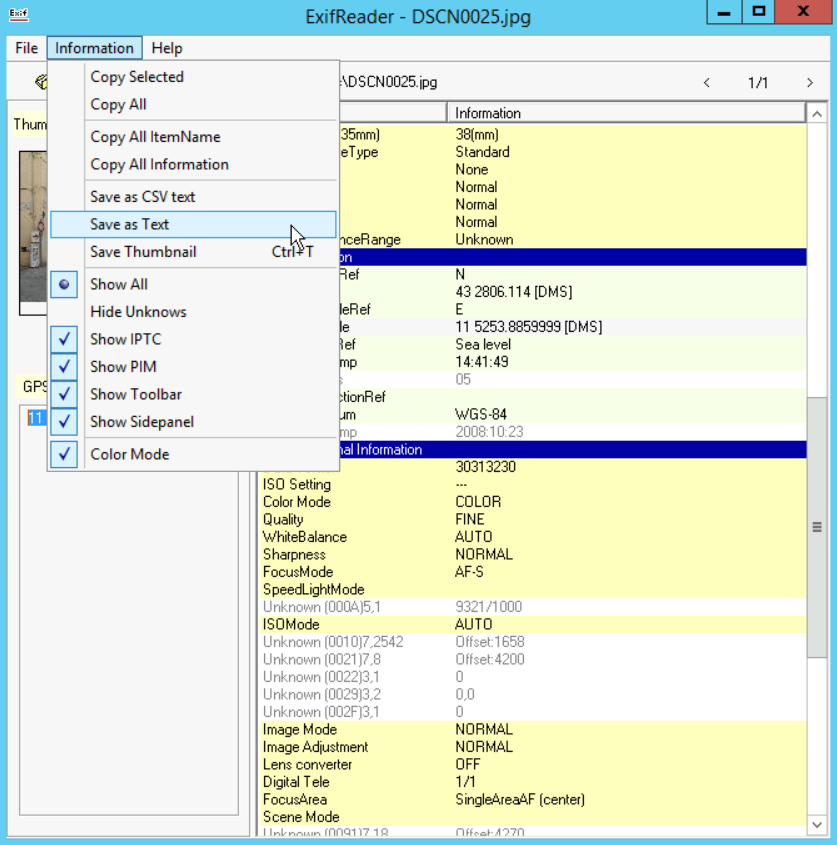
Let us move on to another sample.
Let us open another sample and check it out. This time I am going to open the photo "iphone_hdr_NO.jpg":
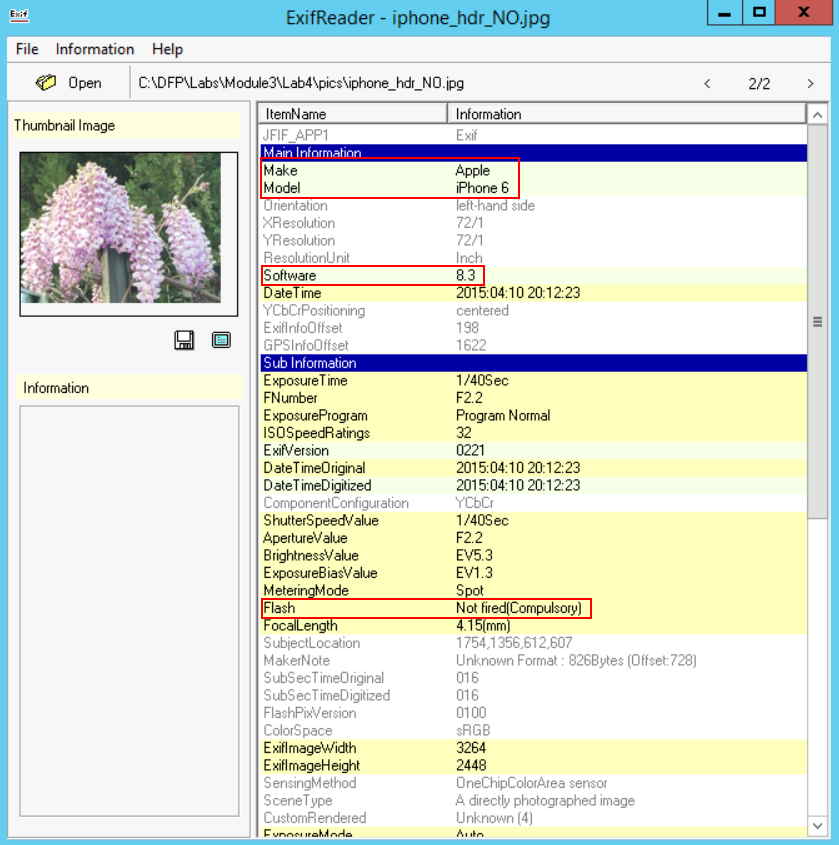
From the photos, we can see the following:
Image ImageWidth and ImageHeight are 3264 and 2448 respectively.
The camera manufacturer is Apple, and its Model is iPhone 6.
The Software used is 8.3.
The photo was created on 2015:04:10 20:12:23, based on the DateTimeOriginal tag.
The flash was not used here too.
Now let us check the GPS and additional information from the second snapshot:
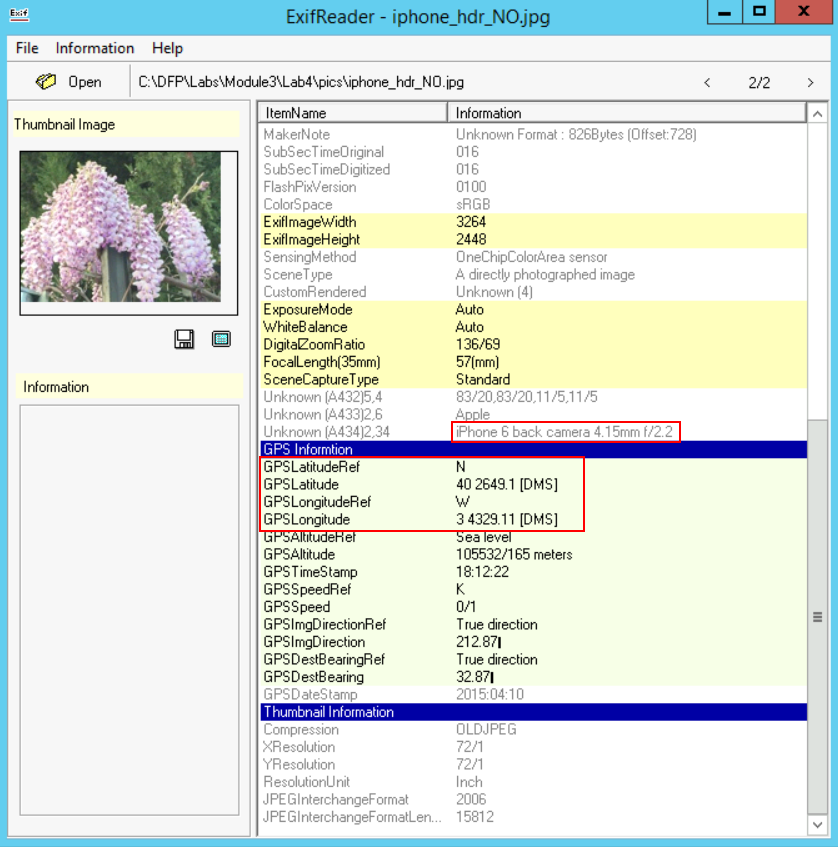
The GPS coordinates seem to be Latitude "40 deg 2649.1'" North, and Longitude "3 deg 4329.11'" West.
We can see that this photo was taken from a back camera.
Before I move to solving Task #4, I want to show you what I found when opening the image02206.jpg using ExifReader:
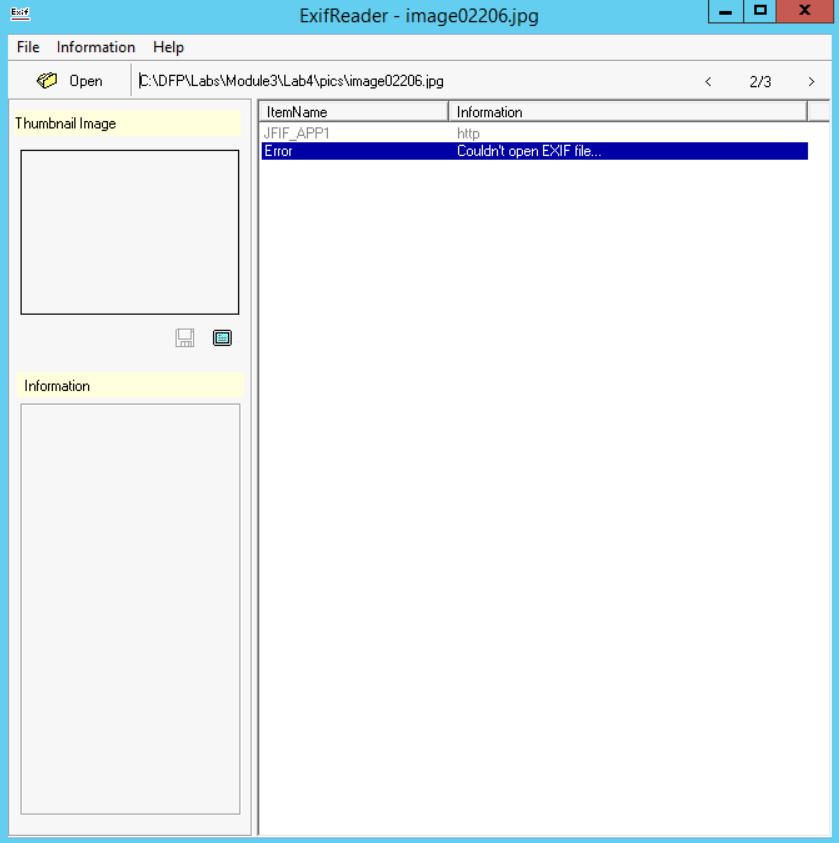
Yes, as you noticed, I was not able to extract anything useful from the photo and if I didn't check another tool, I would have been fooled that this photo does not contain any EXIF data, while in reality it does. This is another example of why you should not rely on a single tool and it is far better to verify your work using another approach or tool.
Run exiftool against image02206.jpg and see for yourself...
We have finished analyzing the evidence and let's say we want to generate a report with all the EXIF data we found within each file. We can do this using a lots of ways, and I already mentioned one in task #3 while using the ExifReader application. This time we will be generating reports using the exiftool utility.
The first approach is to generate a single report for each photo we have. This could be done using the following command (from within the photo's directory):
# "C:\DFP\Tools\Metadata\exiftool(-k).exe" -a -u -g1 -w %f.txt *.jpgThis will produce the following output:
6 image files read
6 output files createdAnd if you check the files, you will find that a .txt file has been created having the same file name as the one of each photo.
Finally, let us generate a single report with all the information within it, specifically let us make it a Comma-Separated Value (CSV) file. We could easily do that with the exiftool utility like this:
# "C:\DFP\Tools\Metadata\exiftool(-k).exe" *.jpg -csv > report.csvThis will produce a single file called "report.csv" that holds all the EXIF data found in each photo. You can use your favorite reader (ex: Microsoft Excel) to open and analyze the contents.
Code Page, https://en.wikipedia.org/wiki/Code_page