You were asked to investigate a hard disk drive of an employee named John Doe, that is suspected of hiding some tools and files on his computer somehow. The IT team at the company has already checked his disk but found nothing, but they are sure he is hiding his data somehow on the disk.
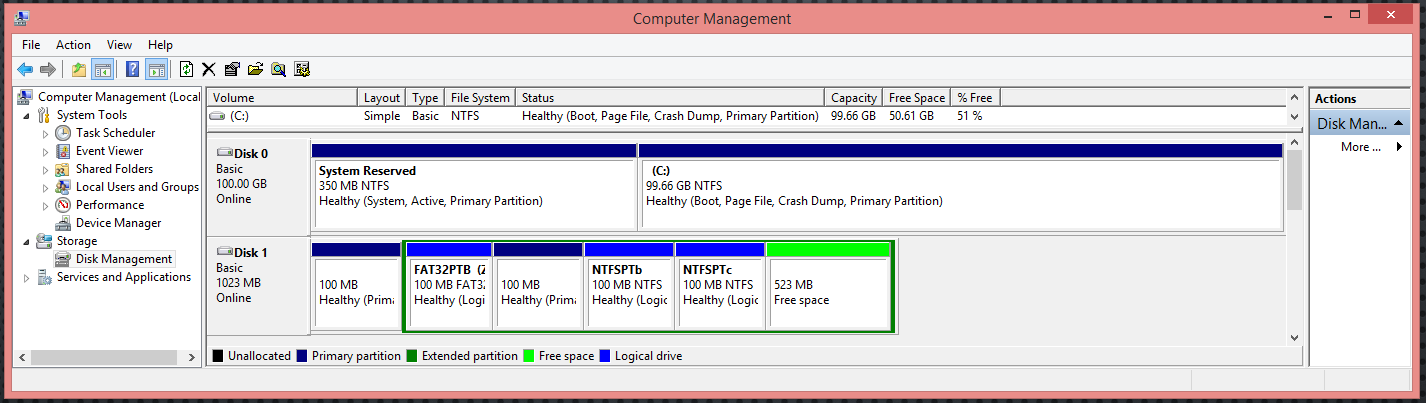
You went there and took a forensic image of his hard disks as seen in the figure below:

Examine the evidence file named "[Lab9.001]" [located at C:\DFP\Labs\Module04\Lab9\Lab9.001] using the forensic tool of your choice (Autopsy or MMLS.exe is recommended), which would lead us to the following Please note: - I have colored each partition entry in the MBR disk structure - You will need to locate and extract TheSluethkit from the C:\DFP\Tools\Windows\sleuthkit-4.12.0-win32.zip
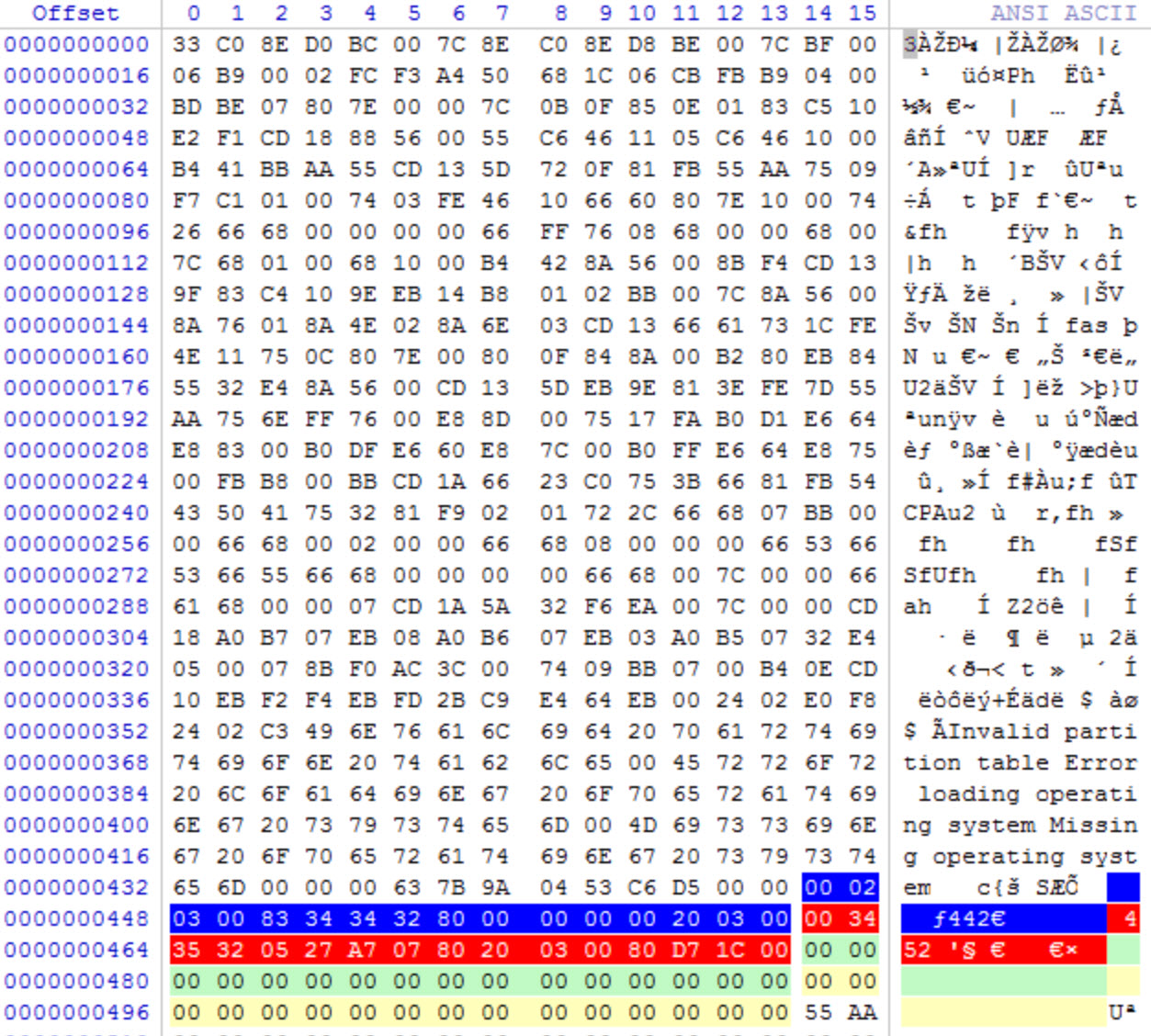
View the partition in the tool of your choice
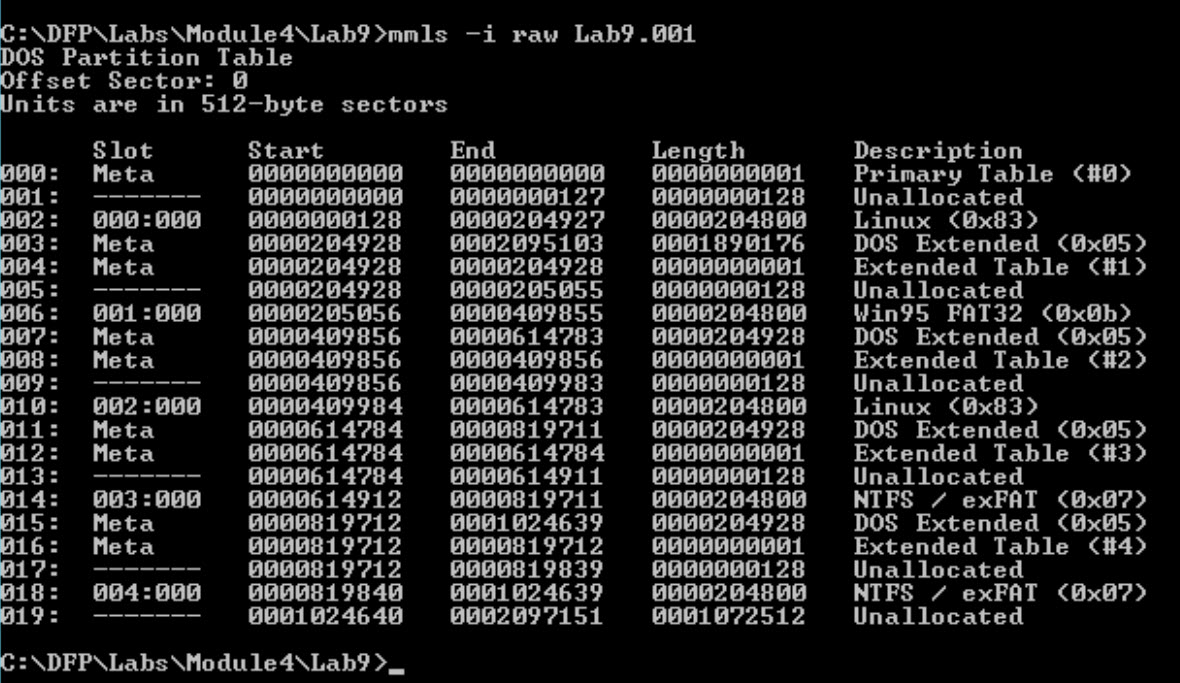
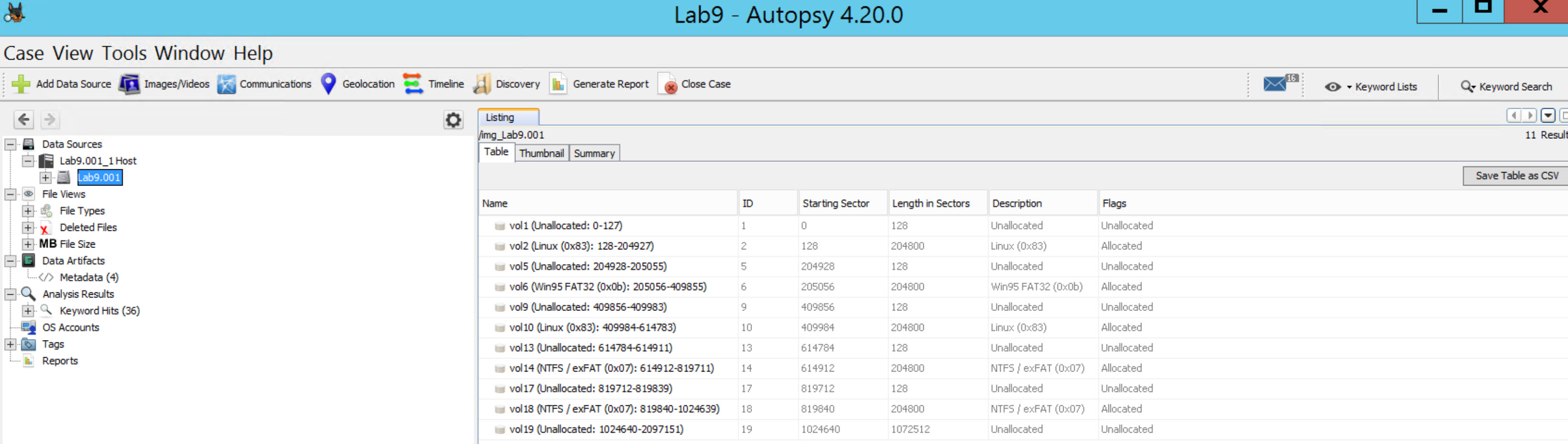
The output should show you a list of partitions, primary and extended. When examiniing a partition structure they are typicaly continous. The sector stop and the sector start for the next partition should be adjacent to each other, with no missing sectors in between. If you see that sectors are not contimous, then you have what is called a partition gap. This is not normal behavior for partition creation, and is generally intentionally created by a human. Typically the threat actor will use a tool such as fdisk, gparted, or diskpart to manually create and delete partitions--custom picking the sector starts and length.
We definitely can observe some gaps.We now need to figure out how this disk is structured and understand where each partition starts and ends.
Manually document the partitions. I recommend creating a table. Start with you first partition and take note of the start sector, end sector, length, partition type, and whether or not there is a gap between the previous partition. Look for allocated vs unallocated partition tables.
NOTE: Before continuing, take the time to study the partition tables generated by your tool and do the analysis yourself.
You should come up with the following partitions
| Partition Number | Start Sector | End Sector | Length | Partition Type | Gap Detected |
|---|---|---|---|---|---|
| 1 | 128 | 204927 | 204800 | Linux (0x83) | No |
| 2 | 205056 | 409855 | 204800 | Win95 FAT32 (0x0b) | YES |
| 3 | 409984 | 614783 | 204800 | Linux (0x83) | YES |
| 4 | 614912 | 819711 | 204800 | NTFS/exFAT (0x07) | YES |
| 5 | 819840 | 1024639 | 204800 | NTFS/exFAT (0x07) | YES |
From this, we know that the first partition is after 128 sectors from the beginning of the disk, and its capacity is 204800 sectors. From the menu and using the go to offset button, use it to move 128 sectors.
This will lead us to the first partition holding a FAT32 file system as seen below:
Now we see that this partition has 204800 sectors
This should lead us to the following:
If we add the values in the sectors preceding partition #1 (128) with the sectors in the partition (204800), we get 204928, which exactly where the next partition starts.
Before we proceed, if you look at the Partition Type Indicator of the second partition, we notice that it is 0x05, which refers to an extended partition. And since it is an extended partition, I just want to remind you that they use the following MBR structure:
Entry Size in Bytes Description 1 446 Zeros 2 16 Describe the first partition 3 16 The location of the next partition 4 32 Zeros 5 2 The end of sector marker 55 AA Total 512
Another important note to remember is the last extended partition table will only have one 16 byte entry, and the rest will be zeros. So, we can understand that this is the last logical partition in the extended structure by checking the second entry of the partition table found. If the entry has values, then this is the location of that partition; if it holds only zeros, then we have reached the last partition as we said.
Continueing on, if we add the size of sectors we found in the previous step, which was 204800 sectors, we will reach the next extended partition, which will also hold an MBR boot structure. This can be seen below:
The beginning of the sector has all zeros as we expected, and then we see that there are also 128 sectors before we reach the first partition. Please remember that this is a relative offset and not one calculated from the beginning of the disk. Also, note the size of the disk is 204800 sectors. So, let us do this again, add 128 sectors to our current position. This would take us to the first partition, and then from there add the size 204800 sectors to go to the next partition.
Note: since the second partition entry is not zero, it means there are still some partitions on this disk.
As we see below, we got a partition holding an NTFS file system:
Adding its size would lead us to the next partition, so let us do that.
As expected, we reached another extended MBR Boot Record.
So the partition is also after 128 sectors and its size is 204800 sectors, plus we still have other partitions to follow, because the second partition table is not empty (zeros). Let's continue. Now we reach another NTFS file system.
Adding the size of it should lead us to another MBR partition.
Now this time notice the first partition is after 128 sectors as we saw in all partitions we went through since the beginning, and the size of it is the same too. But, take a closer look at the second partition entry, it is empty and filled with zeros, which means we reached the end of the partitions on this disk.
Let us create a summary of findings using the table below to answer the questions that were required from us (Report back the starting sector, size and type of each partition found.):
| Partition # | Starting Sector | Size in Bytes | Type ID / Name |
|---|---|---|---|
| 1 | 128 | 104857600 | 83 / Linux |
| 2 | 205056 | 104857600 | 0B / FAT32 |
| 3 | 409984 | 104857600 | 83 / Linux |
| 4 | 614912 | 104857600 | 07 / NTFS |
| 5 | 819840 | 104857600 | 07 / NTFS |
[Note:] if you are asking yourself from where or how did we calculate the starting sector of each partition relative to the beginning of the disk, all you need to do is the following:
A) Partition #1 = Preceding Sectors Value (128)
= 128
B) Partition #2 = Value found in (A) + Preceding Sectors Value (128) + Size (204800)
= 128 + 128 + 204800 = 205056
C) Partition #3 = Value found in (B) + Preceding Sectors Value (128) + Size (204800)
= 205056 + 128 + 204800 = 409984
D) Partition #4 = Value found in (C) + Preceding Sectors Value (128) + Size (204800)
= 409984 + 128 + 204800 = 614912
E) Partition #3 = Value found in (D) + Preceding Sectors Value (128) + Size (204800)
= 614912 + 128 + 204800 = 819840
And that's it; we managed to parse the whole disk, even though it was using a somehow complicated disk structure.
Now if you go back to the partition table in Autopsy in task #1, you can see that we found Linux partition types. If you examine the findings you will see that autopsy identifies the partition as "0x83 Linux". This is from reading the partition table. However, when you click on the partition, it looks like a Windows volume. This is clearly not a linux file system! If you right click and select File System details, autopsy identifies it as a FAT32 partition. If you right click the partition and select "View in a New Window", the hexadecimal data confirms the signature of an FAT32 partition.
In our table partitions, #1 and #3 are reported as Linux, while in the figure above we see that the first is a FAT32 partition, and the third is an NTFS partition. The type of partition is found in the partition entry of each MBR boot record. So, let us locate the entry for the first partition. We already did this in the previous task, so it would be easy to locate the partition entry now by you.
As we can see, the entry shows a 0x83 Linux partition, but when we look at the content of the partition we find that is not true.
So, it seems the employee is modifying this byte, so the Windows system is unable to recognize its existence! If we were to write the byte back to 0x0B which refers to a FAT32 file system, windows would recognize and mount the file system.
Let's check the third partition, which was also identified in its partition table as a Linux partition. Go to the partition itself to check its content. We are supposed to find that it is a linux partition. However, it clearly has the structure of NTFS, which means this is an NTFS partition, and even though the employee changed it from the partition table entry, forensic tools such as Autopsy correctly identify the volume.
Let us verify that by exploring the content as we did previously
As we can see here again, the contents are fully displayed, which means we were right with our hypothesis about what happened here too.
Now, all we would need to do is to, in a hex editor, change the MBR Boot Record for that partition and change the value from 0x83 to 0x0B.
It seems our suspect not only managed to hide some partitions from the IT staff, but he even might have hidden some data on the partition gaps that are created on the disk, usually when the disk was partitioned.
If you look at the figure below, we can see that we have XX partition gaps and two unpartitioned spaces:
Walk through these gaps by selecting each one and then scrolling through them, just to take a look at what is there and if you could identify anything useful. If you don't want to do this, then move on with the lab, we will be doing it by using the tools we have.
Knowing that there are gaps in the partition table and hopefully you have seen suspicious remnants, but we are not quite there yet. We need to process the image for unallocated files.
Use photorec tool located in c:\DFP\Tools to accomplish this. Open the image in photorec:
c:\DFP\Labs\Module4\Lab9>photorec_win.exe c:\DFP\Labs\Module4\Lab9\Lab9.001Once the output is exported review the output for suspicious files.
Congrats; we found a hidden picture.

Let us move on to investigate the rest of the partition gaps.
Next we need to use Eric Zimmerman's Bstrings.exe tool [located at C:\DFP\Tools\Utilities] to search for hidden stuff. After downloading the tool, extract the partition gap by saving it for simplicity to the same location of the tool.
Use the command below to do the following:
bstrings.exe -f Gap4bstrings.exe is the tool we're using, and the "-f" option is to select a file for searching, and the file we used is named Gap4 (I named it that way). Make sure to adjust your commands in order to get something like this:
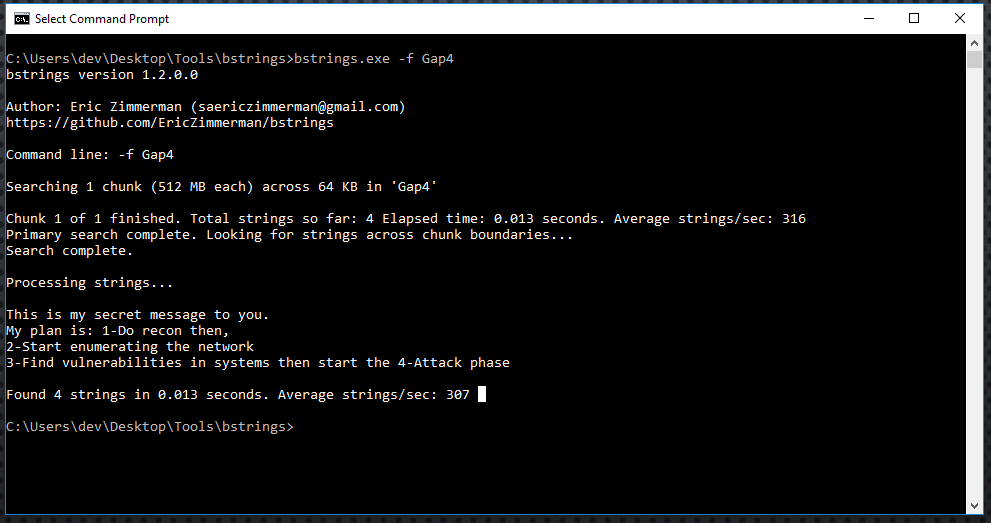
Awesome! We found that he is using these partition gaps to not only hide his maps but even hide his suspicious plans as you can see in the figure above.
Congrats we finished our investigation Successfully!