You are a forensic examiner in a large firm.
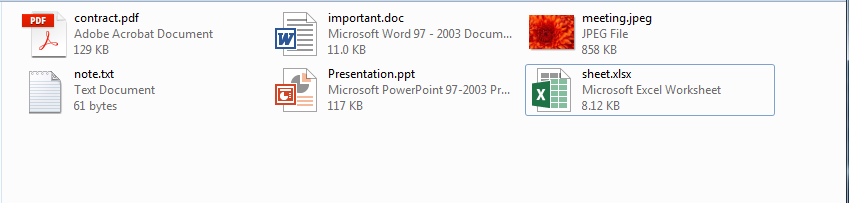
Maria, your colleague from the HR department, has a folder on her computer where she saves important files for work.
A few minutes before her lunch break, she received a resume for a job within the company. Maria opened the document, took a quick look at the resume, checked her important files folder, locked her PC and then went to lunch.

When Maria came back, she was surprised to find the folder of her important files like this.
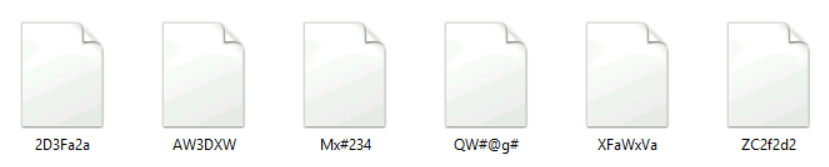
She called you and asked you to help her get her files to their original state.
Those files can be found in the C:\DFP\Labs\Module3\Lab3 directory of the Win10 machine.
Learn and use various tools to analyze and examine various file headers.
Learn the basics of automating tasks using Linux.
Open Hex editor [located on the Desktop] and load the 2D3FA2A file [located in C:\DFP\Labs\Module3\Lab3].
Examining the file's header after opening it with Hex workshop gives us the type of file immediately.
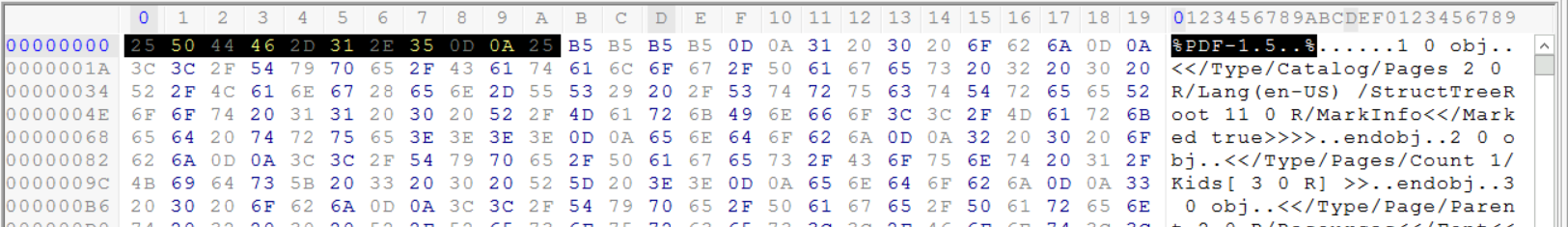
From the (%PDF_1.5 . .%) header and the first few bytes (25 50 44 46 ), which are the PDF files magic number, we can conclude that this file is a PDF file.
The second file's header is less obvious than the first one, as the first line doesn't contain a well-known extension.
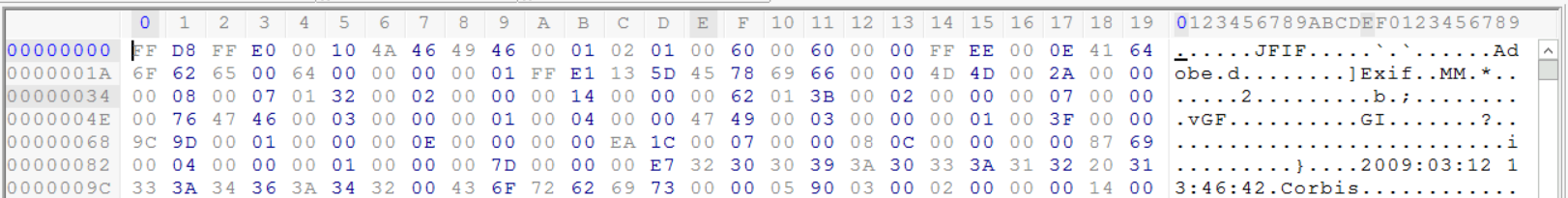
However, we can notice that the file starts with (FF D8) bytes; this is the magic number for JPEG files. We can also notice the JFIF within the file. We can conclude we are analyzing a file having the JPEG format.
The third file is a little more confusing than the other prior examples. We see that the file starts with the values (50 4B 03 04).
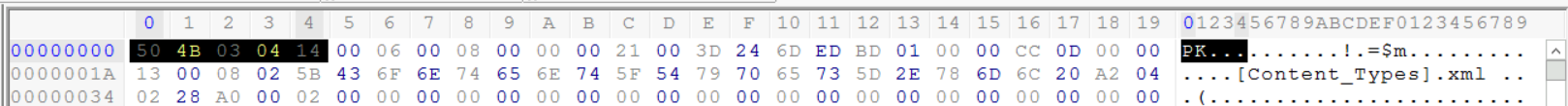
By looking online, we can see that this is the magic number for Microsoft 2010 files.
The problem is that this magic number can't help us differentiate between Word, PowerPoint or Excel files. Since Maria had the three types of files within the infected folder, that means we need to look elsewhere to determine what type of Microsoft Office this file is. In this example, it is the footer of the file that is going to help us, not the header.
Unlike previous examples, by examining the footer of each file, we can see that Microsoft 2010 adds the content type near the end of the file. We can see find many PPT string references written within the footer of the file.
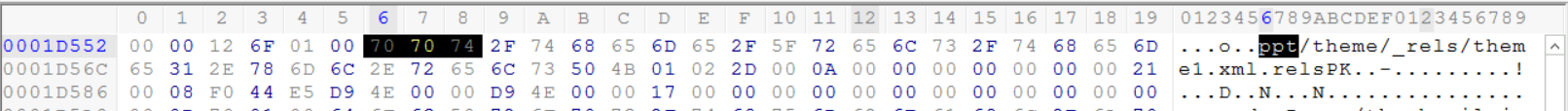
This should help us identify this file as a PowerPoint file.
This file looks much easier than any of the other prior examples we've seen thus far.
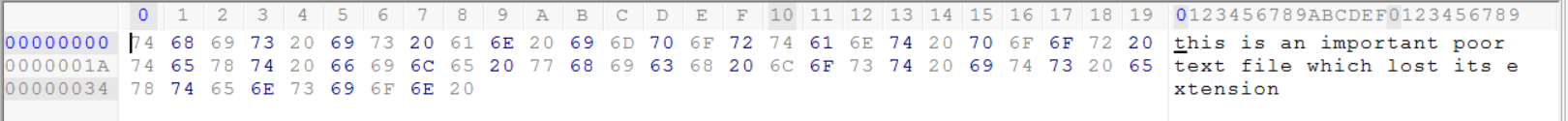
The automatic ASCII mapping function implemented within Hex Workshop is very helpful in this example. The plain ASCII characters written within the file suggests that this is a normal text file which can be opened using Notepad.
As we saw earlier the normal text file which is usually opened using notepad has neither a header or footer. We can simply determine that this is a text file by examining the content and mapping it to ASCII characters
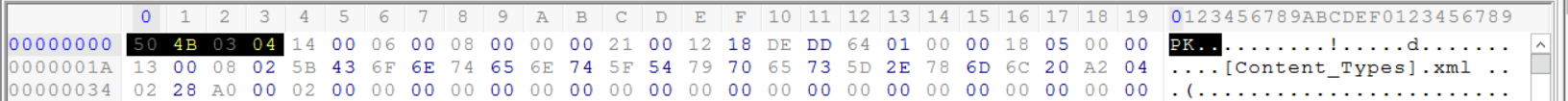
In this example, we also find the Microsoft Office 2010 magic number at the beginning of the file.
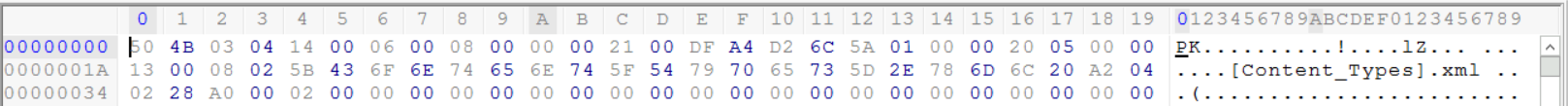
We can use the same methodology we followed earlier by examining the end of the file, to determine what type of file this is. Near the end of the file, we can see the word document reference which suggests that this is probably a Microsoft Office Word document
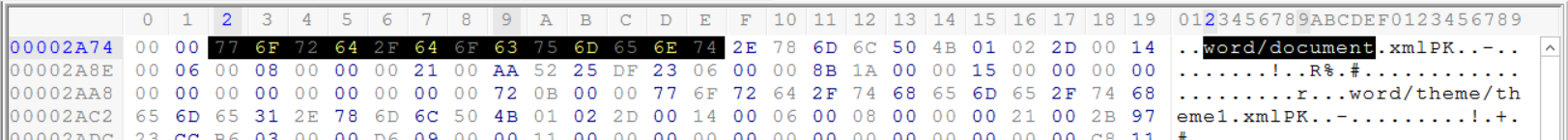
Again we encounter the Microsoft Office 2010 magic number at the header of the file.
Now that we have done it twice before, we know where we need to go and look to determine what kind of Microsoft Office 2010 this file is. At the end of the file, we can find many references such as XL, worksheet, and workbook which point to the fact that this is a Microsoft Office 2010 Excel file.