Company XYZ's IT department got a tip regarding employee misconduct. One of the users might have violated the company's policy by installing different illegal applications and wasting official working hours by doing personal communication (chatting) and other stuff. The IR team managed to respond immediately and take a full forensic image of the user's system.
You have been called to perform a series of forensic analysis and investigation, in order to either prove that the tip was true, and the user was really behaving in an improper or unprofessional manner; or prove that the tip was just an accusation with no solid evidence.
[Note:]
This case will not end with analyzing the Windows Registry only! In this lab, you will be profiling the user's activity based on the information found in Windows registry only, but further user profiling will be done in other labs to cover topics such as Shell Bags and LNK files.
Evidence given are:
| File | Hash |
|---|---|
| NTUSER.DAT | c70ee7615b5c27ab9fee91681da8f4e2 |
| SAM | 190697abebc5496f9b4eb6adc66d2834 |
| SOFTWARE | 5b6a904d2e37fe3de2ab98cdc3c46291 |
| SYSTEM | e4571e43d4d4b62db9c4dc4f96ab629a |
HunterProfileImage folder includes:
Hunter-ProfileImage.ad1 which is the user hunter's whole home directory
Hunter-ProfileImage.ad1.csv
Hunter-ProfileImage.ad1.txt
| File | Hash |
|---|---|
| Hunter-ProfileImage.ad1 | a9a6a075b9deb8d70dca1ddf313fe055 |
| Hunter-ProfileImage.ad1.csv | c02392553aab92362ec9f7f0b05e21cb |
| Hunter-ProfileImage.ad1.txt | 23a057157f5d69bed322390ab131aff4 |
Use different registry analysis tools to perform Windows Registry investigations
Analyze user activity from the registry
Check system configurations found in the registry
Analyze system time zone information
Analyze recently used documents, applications, mounted devices, etc.
Gain the ability to analyze the Windows SAM file
Gain the ability to analyze UserAssist keys
How to use Windows Registry Explorer and RegRipper to Analyze Windows Registry files
How to search and locate different artifacts in the Windows Registry
How to analyze time zone information and understand the true timezone being used
How to analyze network IP Address configurations used by the system
How to check for firewall settings and RDP related configurations
How to analyze the Windows SAM file to locate users, their SIDs and RID also groups and other configurations related to user and group management
Locate and analyze UserAssist keys to understand what applications and files were used by the user
Windows Registry Explorer
DCode
Regripper
Notepad++
Before we start answering the questions, one of the important things to do, if you recall the Windows Registry part of the course, is check the ControlSet. So, in order to analyze the Windows registry correctly, our first check should be to identify what was the active ControlSet.
To do that, let us first open Windows Registry Explorer, which is the tool that we will use to solve this task. You can find it inside "C:\DFP\Tools\Windows\RegistryExplorer_RECmd", and then double-click on "RegistryExplorer.exe." After doing that, I assume you got the following:

Now, since we need to know the ControlSet, this key can be found within the Windows SYSTEM registry hive, so we need to load it. Do that by going to File -> Load offline hive and navigate to the location of the SYSTEM hive (C:\DFP\Labs\Module6\Lab14\WindowsRegistry) and press the Open button.
After doing that, you will get something like the following:
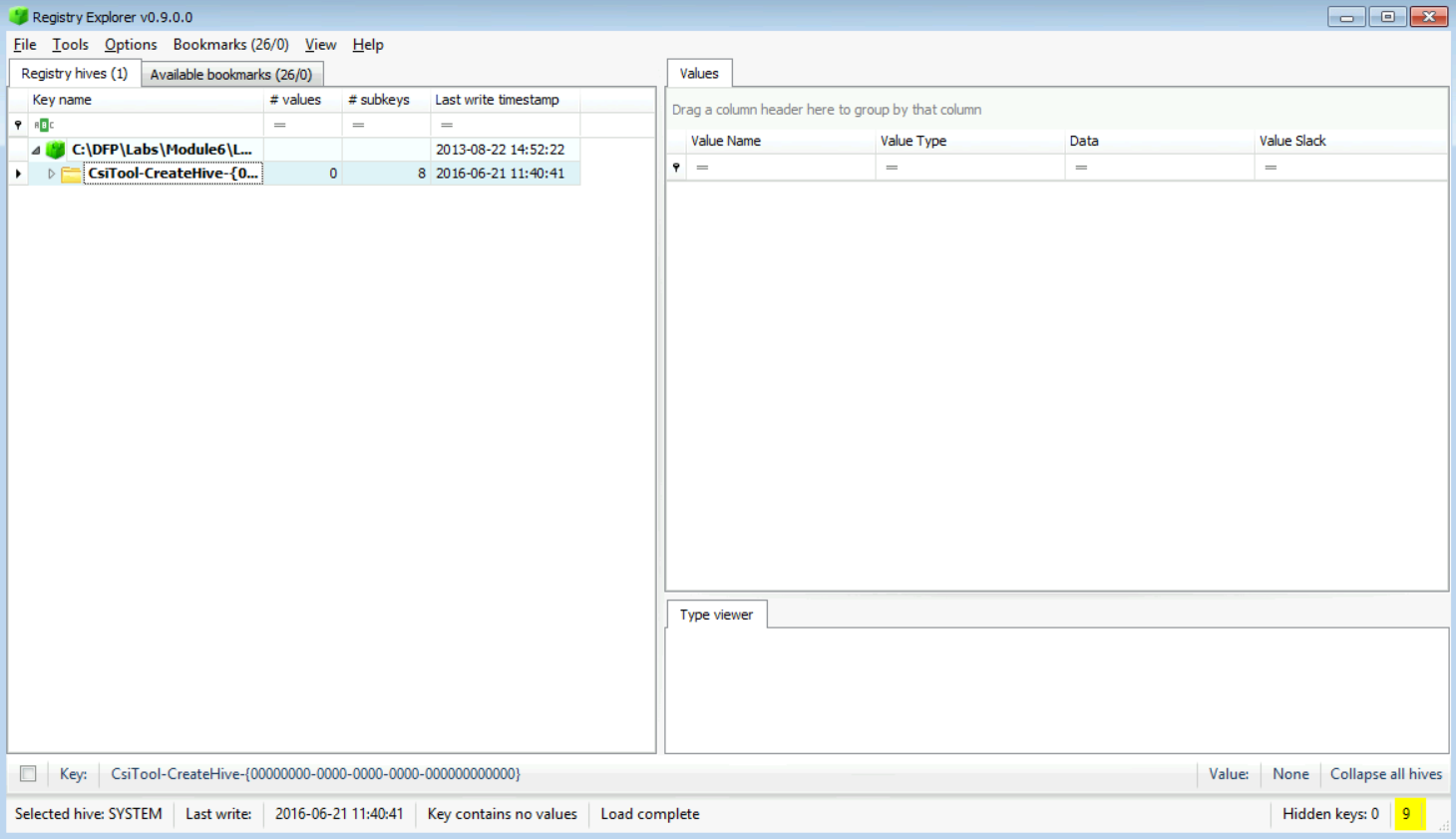
Now you need to expand the first row, and then you need to navigate all the way through SYSTEM until you reach the "Select" key, as seen in the snapshot below.
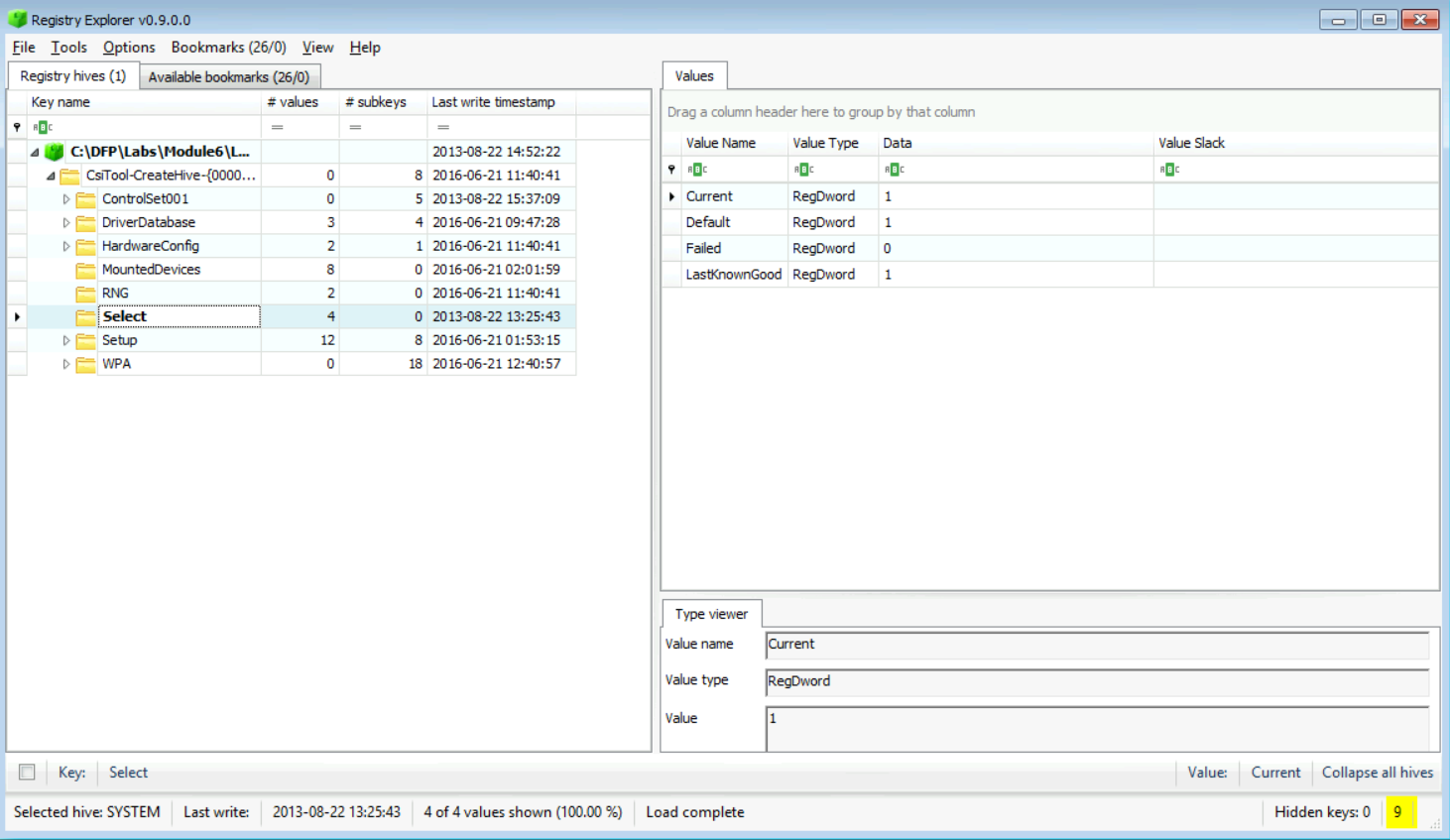
Now if we** check the content of the **Current value, we see it holding the value 1. Now, since we have the ControlSet, we know which direction to steer our investigation wheel inside the SYSTEM keys. Let's move on and start answering some questions.
[Important note:] Since we only have one here it's easy, but you if you have more than one, this is a really important step to check before proceeding.
[Answer:]
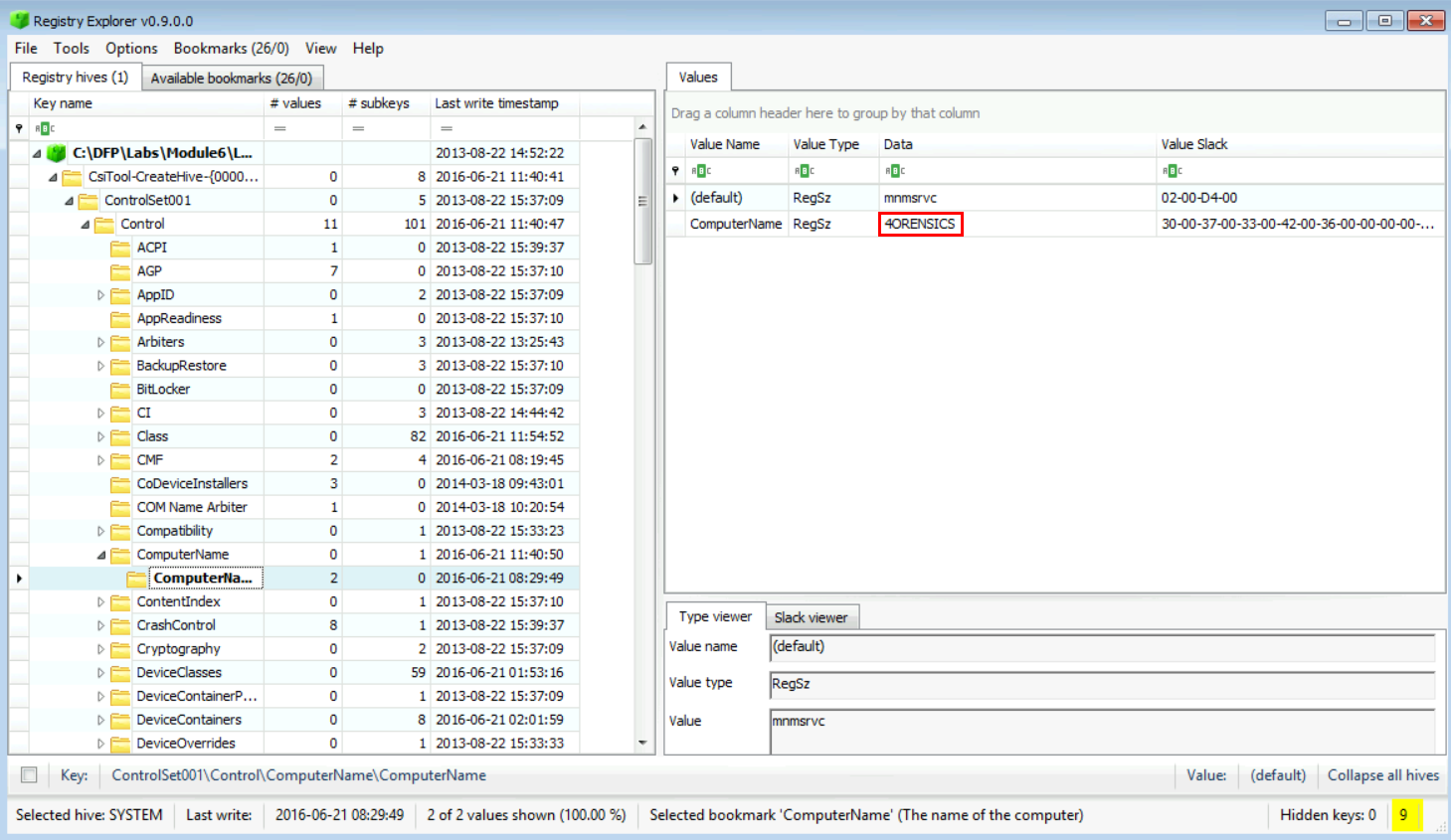
Now, in order to answer that, we need to check for the ComputerName value to find the answer. This is easily done by going to Bookmarks -> Common -> ComputerName. If you check the right pane as seen in the snapshot below, you will notice that it is "4ORENSICS".
[Answer:] This information is very important for us to continue our investigation. Let us check the Operating system version used and other important information. Before we can find this answer, I need you to add the Windows SOFTWARE registry to Windows Registry Explorer. After doing that, I need you to navigate to:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
The table below could help you:
| Operating System | Version number |
|---|---|
| Windows 10 and Windows Server 2016 | 10.0 |
| Windows 8.1 and Windows Server 2012 R2 | 6.3 |
| Windows 8 and Windows Server 2012 | 6.2 |
| Windows 7 and Windows Server 2008 R2 | 6.1 |
| Windows Server 2008 and Windows Vista | 6.0 |
Now from the CurrentVersion value found and based on the table above, we can say that the system we are investigating is a Windows 8.1 or Windows Server 2012 R2, but if you check the value ProductName, you will find that we are dealing with a Windows 8.1 Enterprise. All this can be seen in the snapshot below:
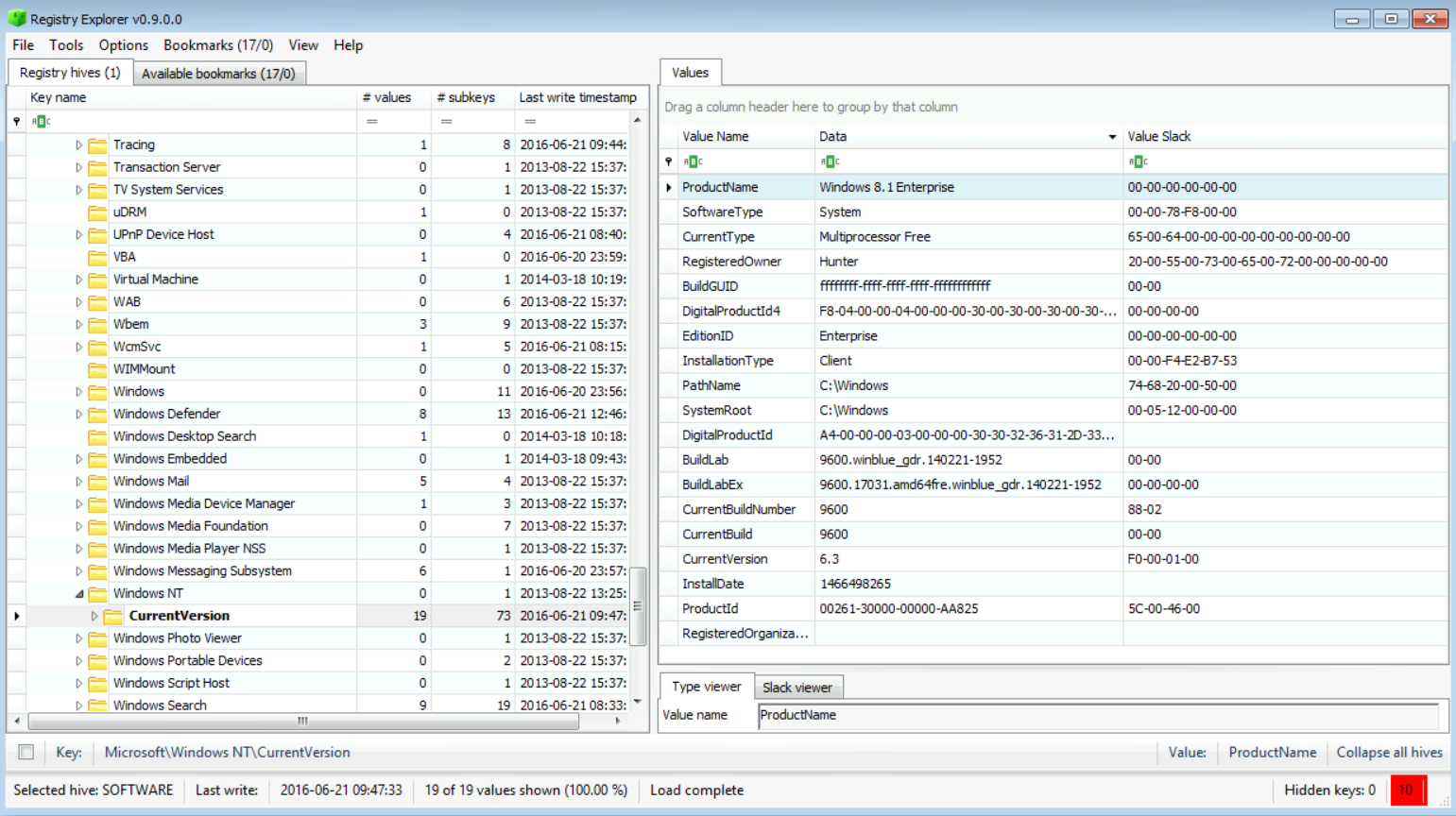
[Note:] I have removed one of the "Value Type" column from the output to make it easier to understand.
[Answer:] Now, you need to pay attention to what will be done. First, the time zone information could be found by navigating to the location below:
SYSTEM\ControlSet###\Control\TimeZoneInfromation
And since our ControlSet is 1, then the exact location would be:
SYSTEM\ControlSet001\Control\TimeZoneInfromation
The results we found were the following:
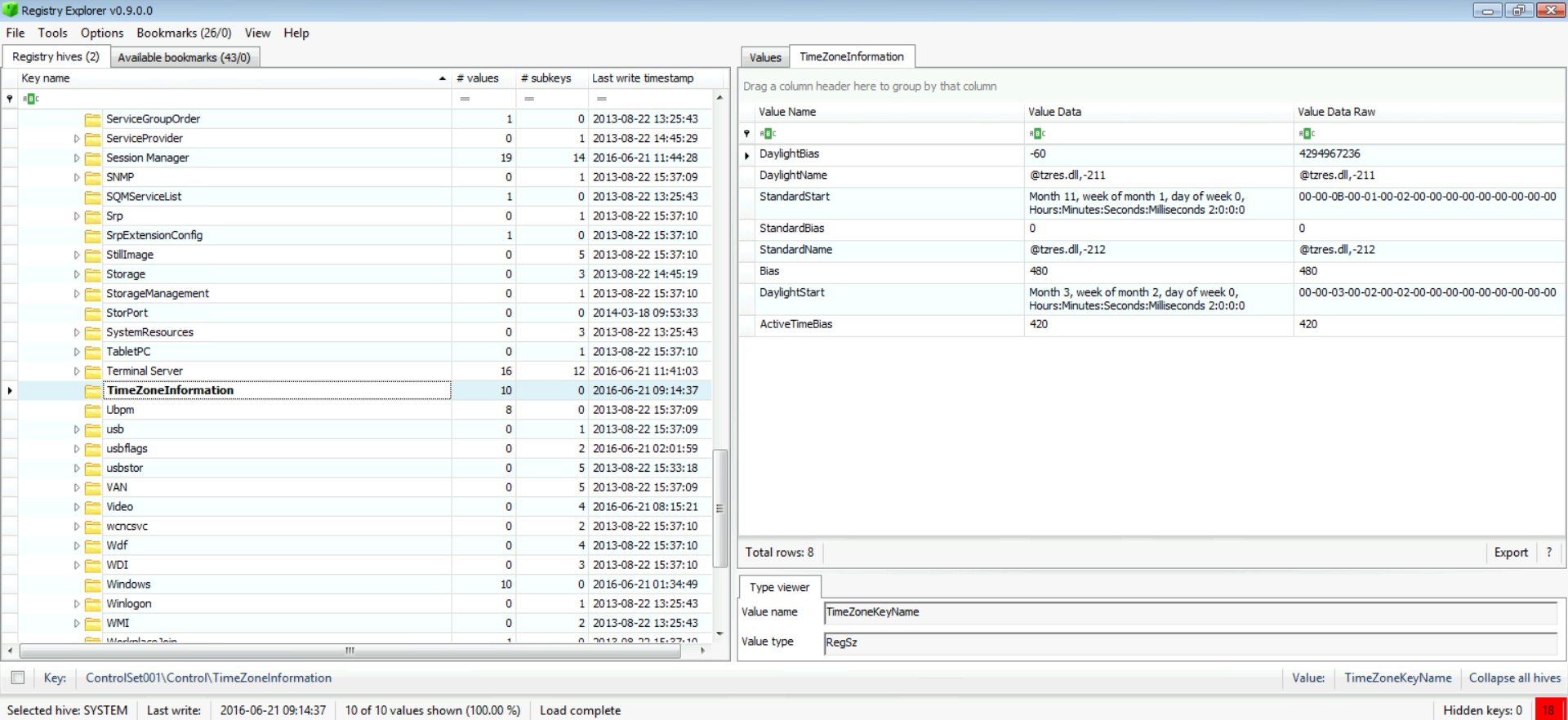
This is the most important value to be used to establish time-related to UTC, and it is the one you need to use to determine whether daylight saving is active or not. Check this reference: http://kb.digital-detective.net/display/BF/Identification+of+Time+Zone+Settings+on+Suspect+Computer
So, based on the ActiveTimeBias value found (420) and the StandardName value (@tzres.dll,-211), we can determine we have a PST8PDT or Pacific Daylight Time or just PDT time zone. If you're wondering where I managed to resolve @tzres.dll,-211 to PDT, then check this:
https://github.com/log2timeline/plaso/blob/master/plaso/winnt/time_zones.py
Or
http://www.nirsoft.net/dll_information/windows8/tzres_dll.html
Now, is DST active or not? Well, it sure is, and that's because ActiveTimeBias is 420 which when divided by 60 leads to 7 hours. And this means we have a UTC-7.
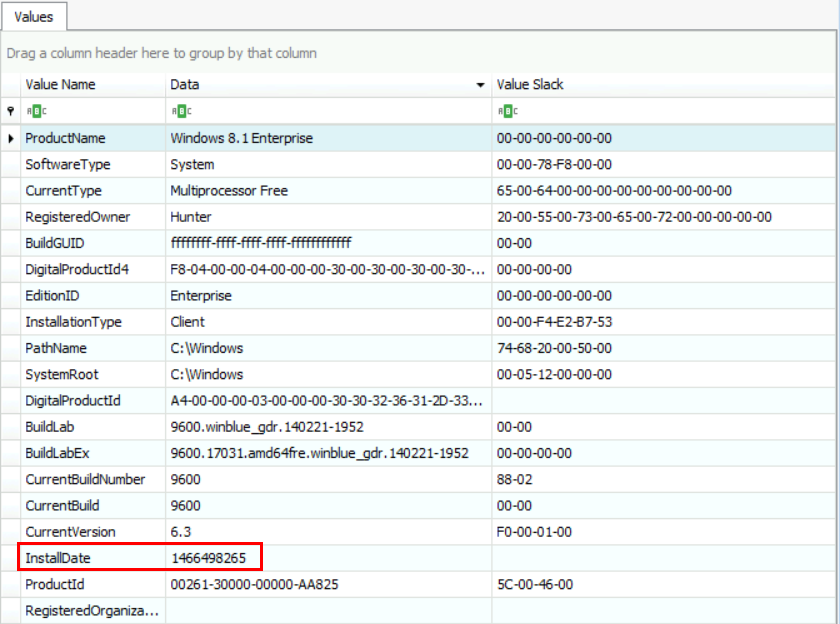
So, we have the value 1466498265!
Easy; we can use the DCode.exe tool here present at [C:\DFP\Tools\Time] to convert this number into a timestamp. You can find the tool inside the tools directory. BUT wait a minute! We need to adjust the time using the time zone we just found. So, make sure in the "Add Bias" field you select UTC-7 because this is the time zone this computer was working in. Before pressing the Decode button, please keep in mind that Windows uses Unix 32 bit here for the InstallDate value, so make sure you select the "Unix: Numeric Value." Finally, enter the value we want to decode, and with that done, we have the following after pressing Decode:
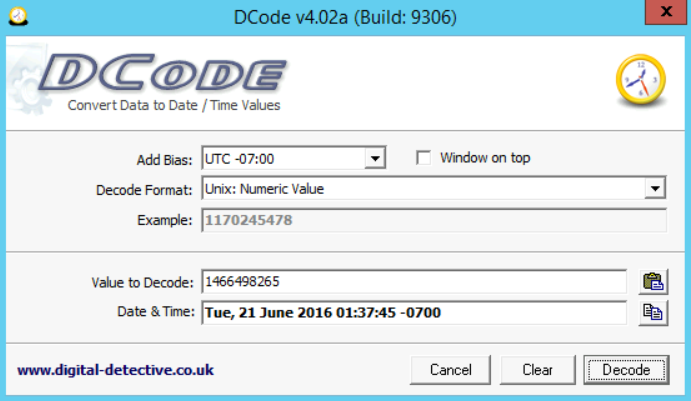
The answer is:
Tue, 21 June 2016 01:37:45 -07:00
That was easy, right?
[Answer:] This system was registered to a person named "Hunter," and the system root directory is C:\Windows which could be found from the path below:
Microsoft\Windows NT\CurrentVersion
Check the snapshot below:

Shutdown time is found in: SYSTEM\ControlSet001\Control\Windows\ShutdownTime
It is a Windows FILETIME (64 bit)
Answer = 2016-06-21 01:34:49 (UTC)
Answer = Tue Jun 21 01:34:49 2016 (UTC)
Answer = Tue Jun 21 08:34:49 2016 (UTC-7/Local Time)
Extra: To find the Installation date, we need to check the following: SAM\Domains\Account\F
Offset 8-15 holds value
It is using Windows FILETIME (64 bit)
Answer = 2013-08-22 14:45:11 (UTC)
Note: The InstallDate or other registry keys no longer are valid to use as an Installation date, since they only reflect the time of updates/upgrades/etc/long story short
SYSTEM\ControlSet###\Services\SharedAccess\Parameters\FirewallPolicy
SYSTEM\ControlSet###\Control\TerminalServer
And since we are working under ControlSet001, then we need to go here:
SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy
SYSTEM\ControlSet001\Control\TerminalServer
Make sure you check the firewall for both profiles (domain and public). If you don't know how to reach that, then we could go to Tools -> Find and then write the keyword you are looking for. You can see that in the snapshot below.
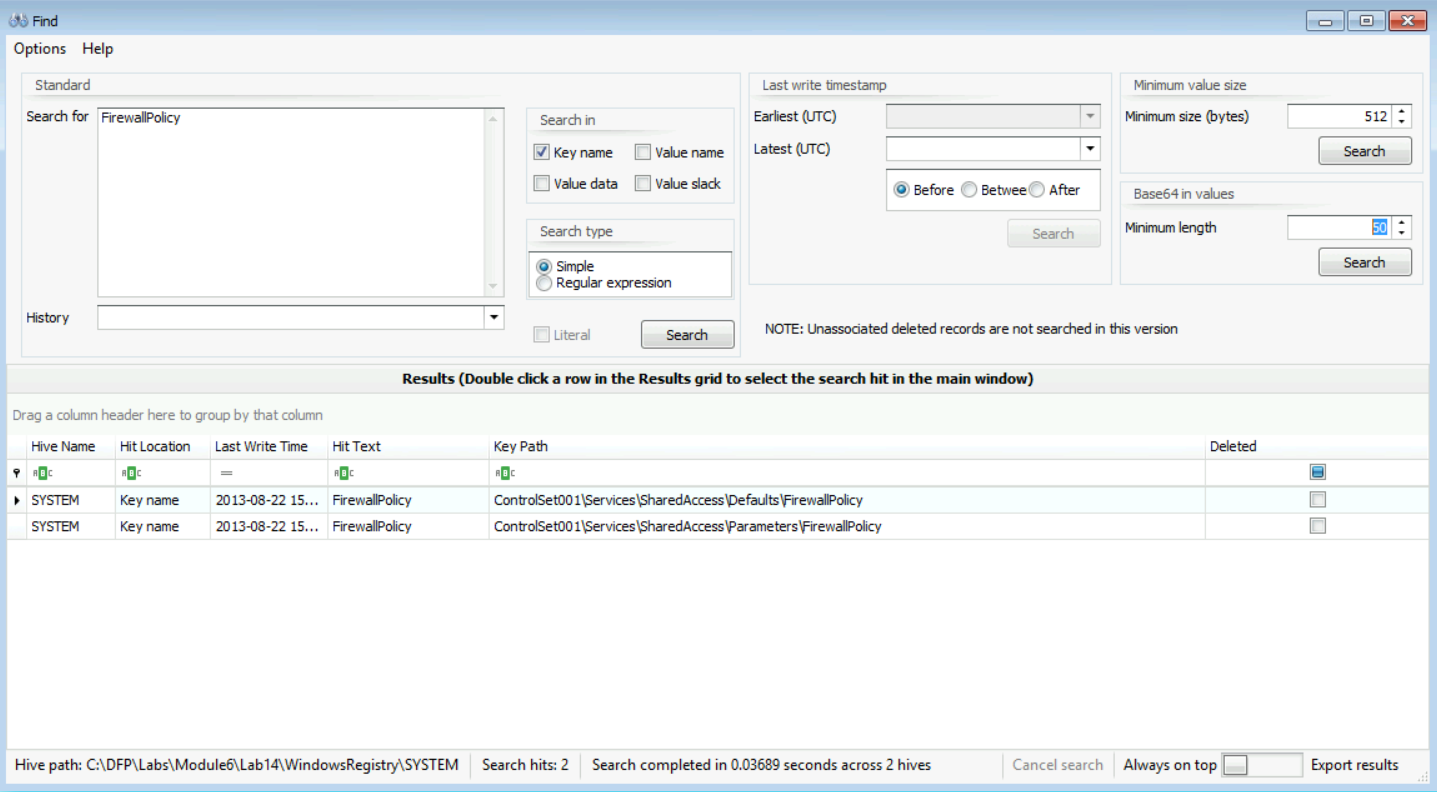
After that, all you need to do is double-click on the result you want to display under Windows Registry Explorer. Now from the left-hand pane, we can see after expanding the tree and selecting DomainProfile, that we found the following:
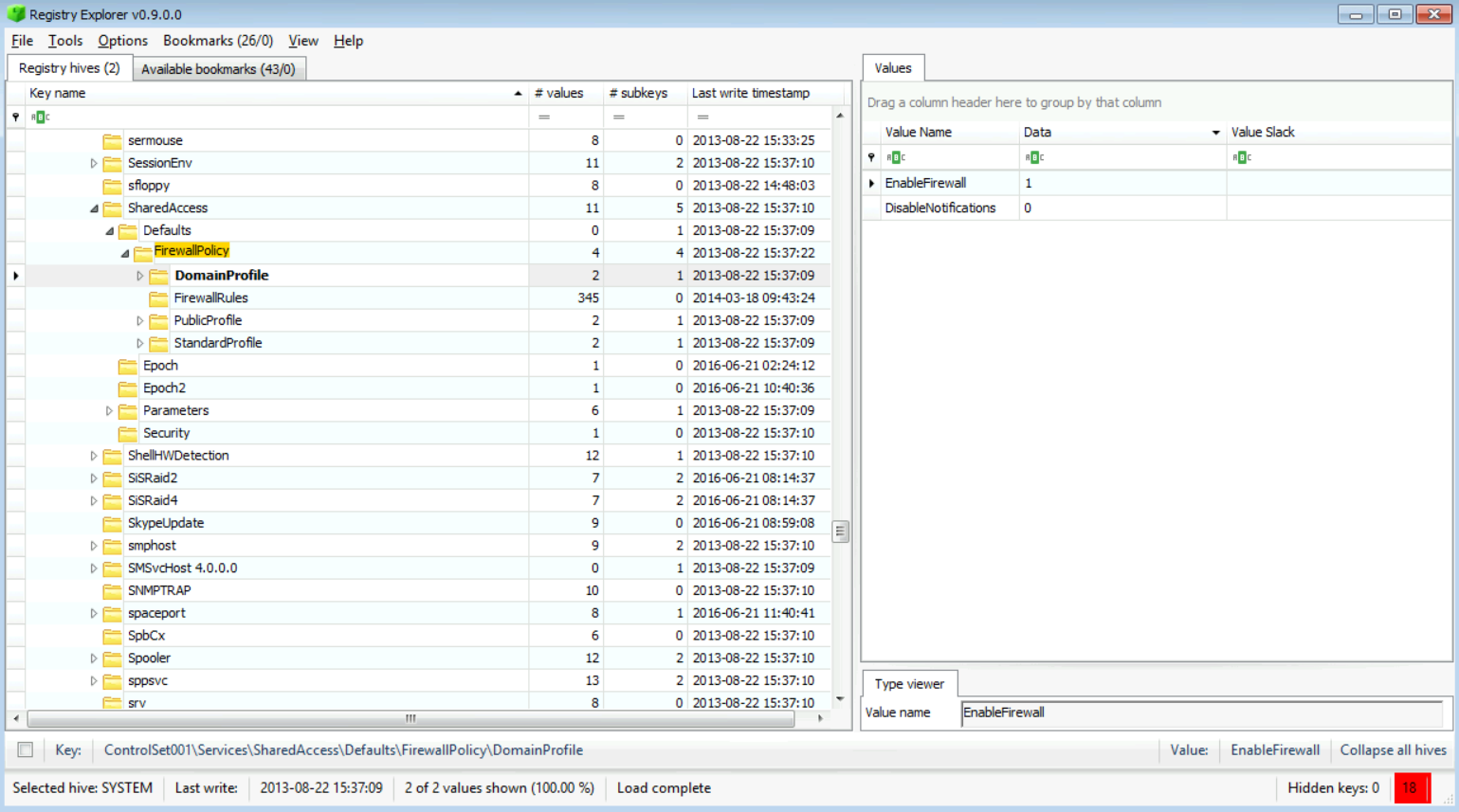
This clearly says that the firewall is enabled. By checking the PublicProfile, we get this:
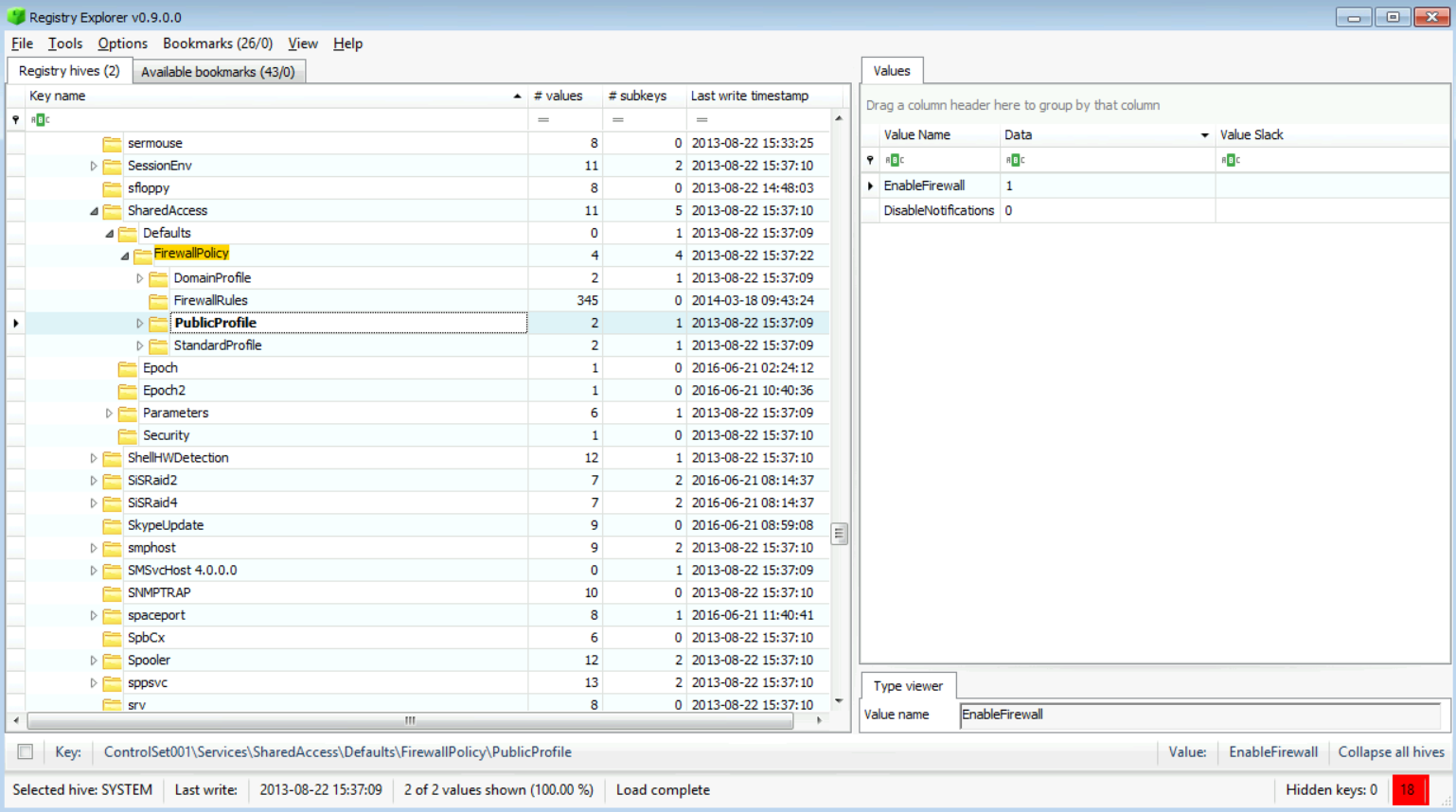
And again, this means that the firewall is enabled (value 1 here represents true which means it is enabled).
Now, by going to the "SYSTEM\ControlSet001\Control\TerminalServer" location and checking the fDenyTSConnection value, we can determine if RDP is enabled or not. From the value found, we can say that it is true, the RDP is not allowed.
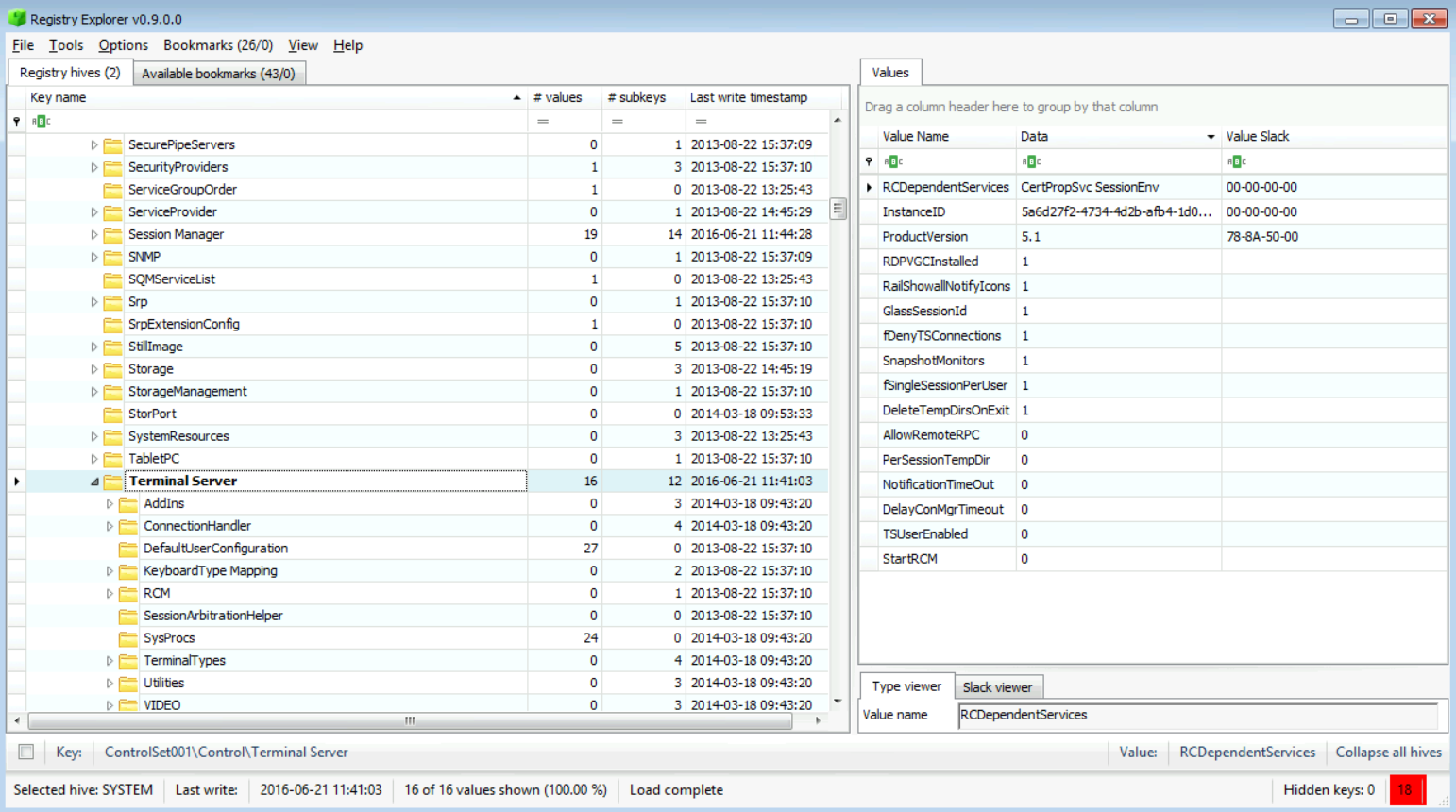
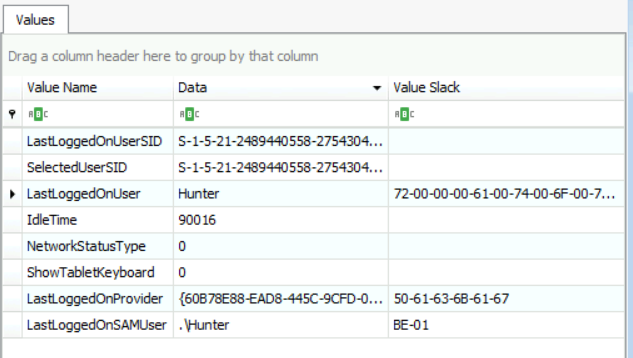
So, the last user who logged into the system was "Hunter," and we could even see his SID (S-1-5-21-2489440558-2754304563-710705792-1001).
Now, we need to start answering the questions related to networking stuff, so let's get that done too.
[Answer:] To answer this, I need you to navigate to the following location: SYSTEM\ControlSet###\Services\Tcpip\Parameters\Interfaces\{GUID}\
Which means, in our case: *SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces\{GUID}\ *
As we can see from the snapshot below, the GUID for the active interface is: 8CB9FBF6-AE23-4E1C-AA0A-EE23CB4FE736. Which means the full path is: ControlSet001\Services\Tcpip\Parameters\Interfaces\{8CB9FBF6-AE23-4E1C-AA0A-EE23CB4FE736}
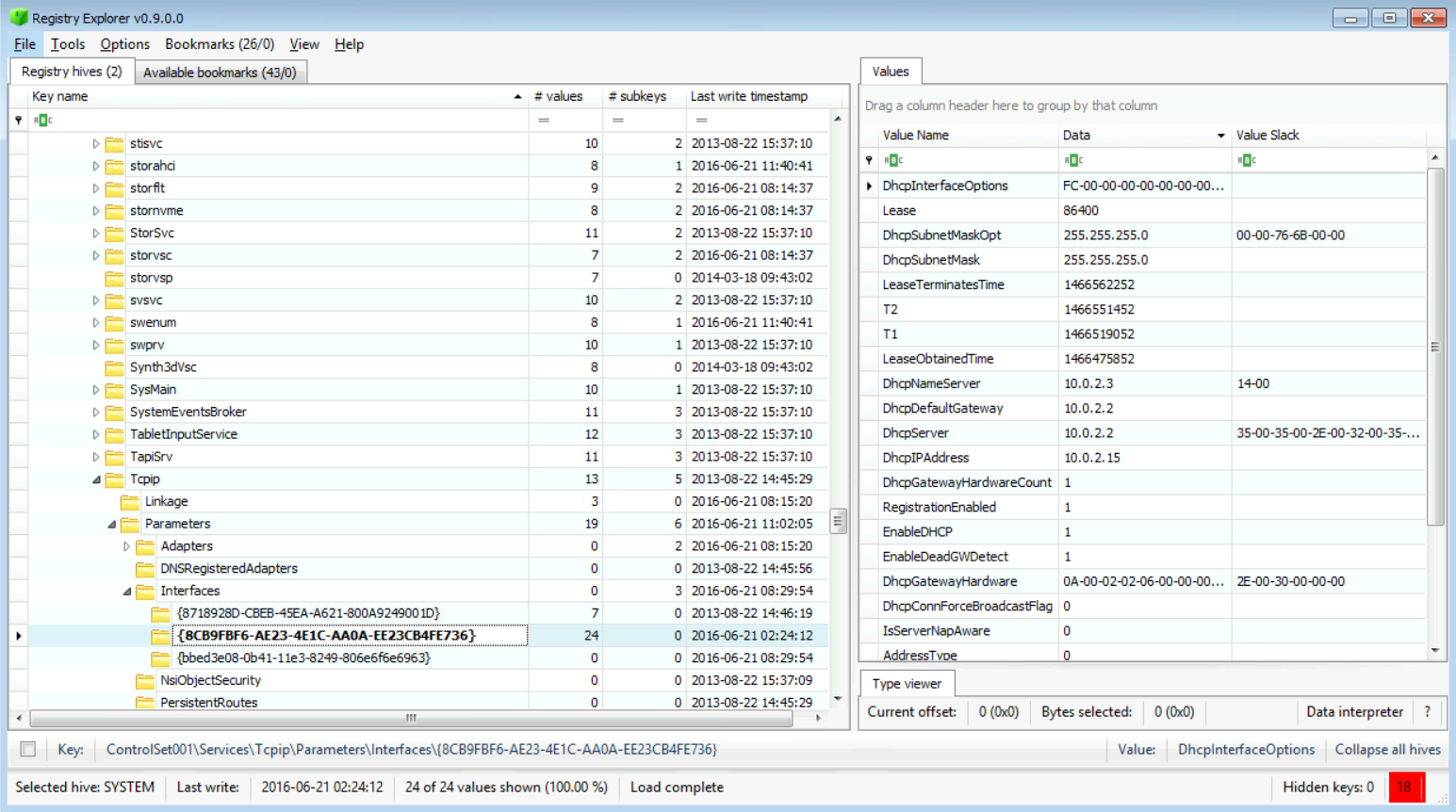
Now, if you check the values found within that key, you can find that the computer was given an IP Address which was 10.0.2.15 from the DHCP Server which had the IP Address 10.0.2.2, as seen in the figure above.
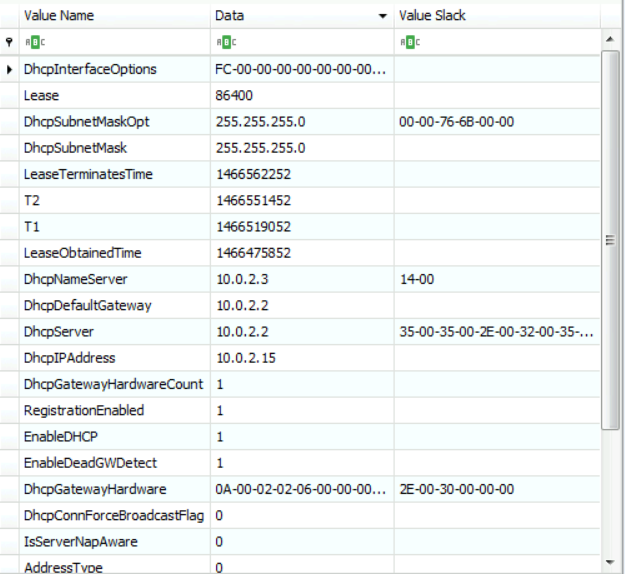
[Answer:] We answered the DHCP server part in the previous question. Now for the default gateway, we can find it be going down a little in the same page under the value named "DhcpDefaultGateway." The result is also 10.0.2.2 as seen in the figure below:
When was the leased time obtained, and when will it end? [Answer:] Now to check this we need you to be focused a little bit more. We need to check the following values:
LeaseObtainedTime
Lease
LeaseTerminatesTime
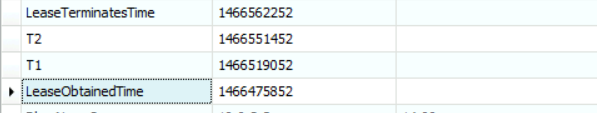
The first value gives us an answer about what was the leased time for this interface. It shows 1466475852. To convert it using epoch time, we can use the following website:
https://www.epochconverter.com/
Go to the first option "Convert epoch to human readable date and vice versa," add the value in the field and click "Timestamp to Human date." Now, since we found that this computer has a UTC-7 timestamp or PDT, make sure you click on the GMT URL found at the end of the line saying, "Your time zone:" to adjust the used timestamp. It will take you to another page, just search for the -07:00 or PDT to get the following final result: Jun 20 2016 19:24:12
Or you can go to this page directly: https://www.epochconverter.com/timezones?q=1466475852&tz=UTC
So, based on that, the lease was obtained at "Jun 20 2016 19:24:12".
To check when does this lease terminate, we can either use the value in LeaseTerminatesTime and follow the same procedure we did for the lease obtained, or just add the value in Lease to LeaseObtainedTime. Another way is to divide that number you found in the Lease which is 86400 by 1440 (seconds per day), and that gives us one day. To conclude, the answer is 1-day.
[Note:] you can also check that on the epochconverter website.
Let's get this task done quickly as it is very easy thanks to Windows Registry Explorer. In order to export the registry hives into other formats for referencing or analysis using another tool, all you need to do is go to File -> Export "Registry hives" and then choose the file format you want. That's it!
Now, in order to create a bookmark, follow the steps below:
To add a bookmark, all you need to do is right-click on the key of interest, and then select "Add bookmark" or press F4 on your keyboard.
A menu like the one seen in the figure below will pop-up.
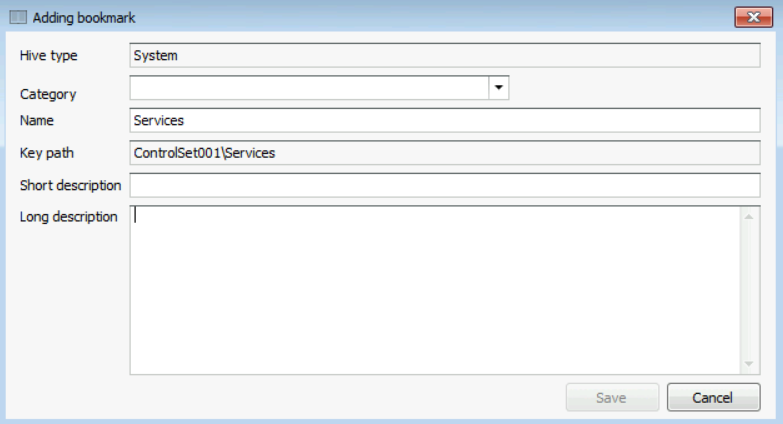
Fill in the fields:
a. Category: to what category does this registry entry belong to.
b. Name: the name of the registry key.
c. Key path: the full path to this registry key.
d. Short description: give this bookmark a short description.
e. Long description: write full details of this bookmark. For example; what it does, why it is important and stuff like that. Anything that will help an analyst understand its benefit.
When you finish, press the "Save" button.
Now, to use your new bookmark, all you need to do is select the exact hive that this bookmark belongs to (assuming you closed Registry Explorer, or you navigated to another location), then go to Bookmarks -> User created and finally select the one you want.
We will be solving this task using another tool named RegRipper present at [C:\DFP\Tools\Others\RegRipper2.8-master], so that you know that there are different options to be used out there. So, let us start analyzing the Windows SAM file, to extract user information from there. This will help us with checking different stuff based on his/her SID. I assume you already know how to extract the Windows SAM file from a system, as it is given to us this time, so let us proceed with answering the questions.
To use RegRipper, all we need to do is load the SAM file, specify a location to store the generated report, and then select the profile required, which is sam here. After that, all you need to do is press the Rip it button. This could be seen in the snapshot below:
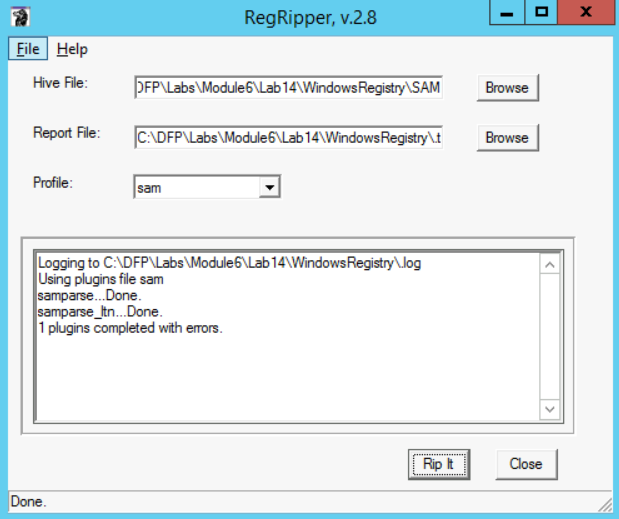
I have attached the generated report to the Appendix of this document, so please check it if you didn't manage to generate one for some reason. Now we can move on and start answering the questions.
[Answer:] We have the following:
a. Administrator
b. Guest
c. Hunter
But, please note that the account is disabled for both Administrator and Guest
[Answer:] Since both Administrator and Guest are disabled accounts, and since we know our suspect is using the user account named "Hunter," the SID is "S-1-5-21-2489440558-2754304563-710705792-1001". This means that his/her RID is "1001".
[Answer:] It was created on Tue Jun 21 08:37:43 2016.
[Answer:] This user is a member of the Administrators group, which means he has administrative privileges. Additionally, the Administrators group last update was "Tue Jun 21 08:37:43 2016", which is the exact same time the user account was created and added to that group.
[Answer:] The last login that for this user was "Tue Jun 21 01:42:40 2016".
[Answer:] From the Login count, we can see that he/she logged into the system 3 times.
[Answer:] We can find it from the "Password Hint" settings, and it was "What do you do?".
We have a good base of information about the user of interest, so in this task, we will be chasing other Windows artifacts that could be found in different Windows registry files, especially as we said in the NTUSER.DAT file, which is the file that holds most of the user account's configurations and settings.
In this task, I am going back to using Eric Zimmerman's Windows Registry Explorer, feel free to use whatever Windows Registry tool you want.
Let us begin answering the questions we have:
[Answer:] To answer that question, we could check the following location: SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths
After navigating there, I assume you found a lot of keys there, as seen in the snapshot below:
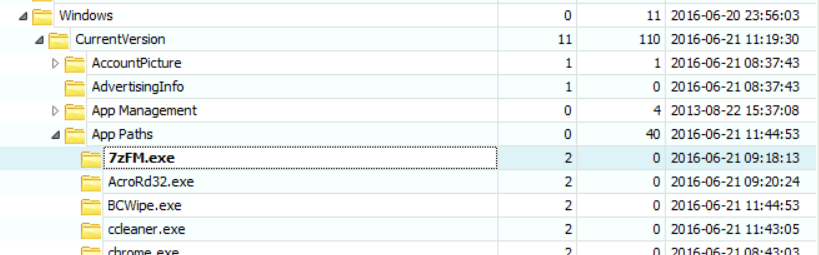
So, to form a list we will just need to go through them. I'm going to cheat a little here and use RegRipper and then get the list from there (the results of ripping SOFTWARE using RegRipper is attached as an Appendix to the end of this lab manual).
I assume you found a lot of applications; so I am just going to mention those that are suspicious and leave out the applications that are from Microsoft and others like Java, Python, Adobe Acrobat Reader, Notepad++, 7zip, Google Chrome, etc.
Those that look suspicious are:
a. BCWipe.exe - C:\Program Files (x86)\Jetico\BCWipe\BCWipe.exe
b. ccleaner.exe - C:\Program Files\CCleaner\CCleaner64.exe
c. Wireshark.exe - C:\Program Files\Wireshark\Wireshark.exe
An investigator must not rely on the "App Paths" subkeys only. There are lots of applications that won't be listed there! That means further investigation is always vital! For this task, we won't do that, as the aim is just to work with the artifacts in the Windows Registry.
[Answer:] You have to build a list of tools that could be used to remotely administer a system, so what came in mind here was two things: VNC and TeamViewer. If we add the NTUSER.DAT file to Windows Registry Explorer and search around, we will find the following:
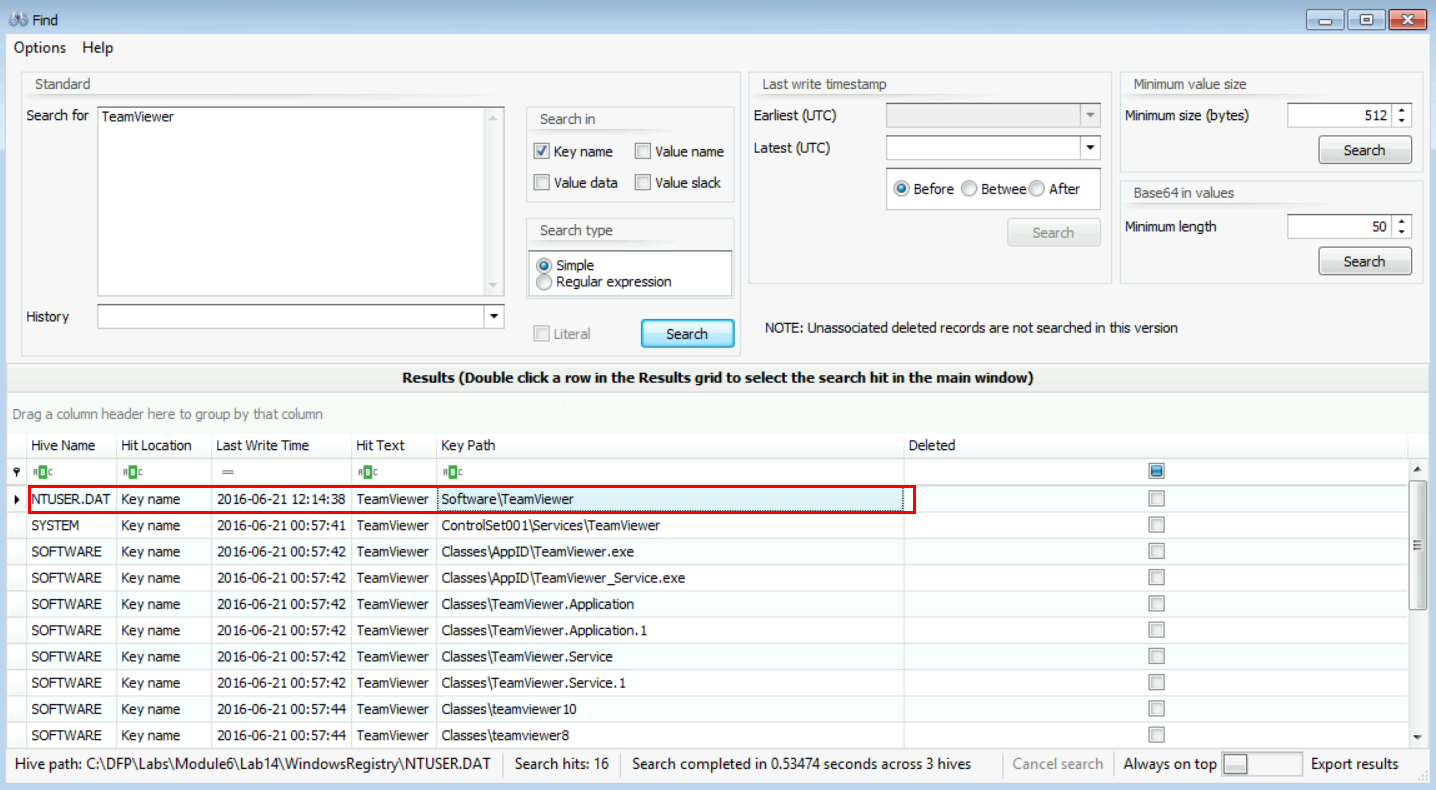
And if we double click on the first entry (highlighted in red in the previous snapshot), we will get the following:
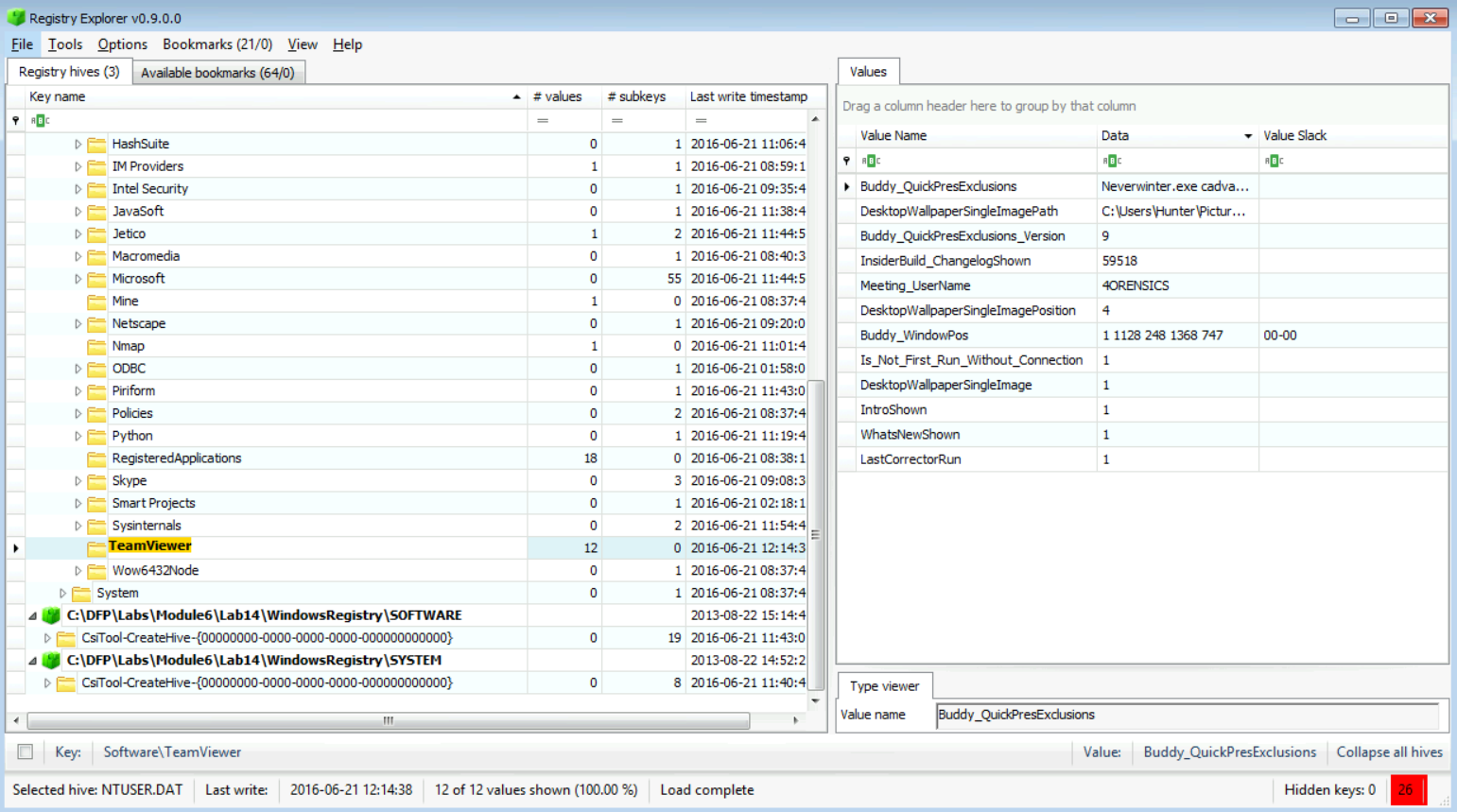
So, it is clear that the user has used TeamViewer, and maybe this was the RAT tool mentioned to us. Anyway, let's wait a little, we should not stop at this point, as we said; the more evidence, the more bricks we have to build a solid case. We do not have enough information yet. So, let us move on and answer other questions.
[Answer:] You can easily answer that by pressing ctrl+F to bring up the search screen, and then use both keywords to search for results, as follows.
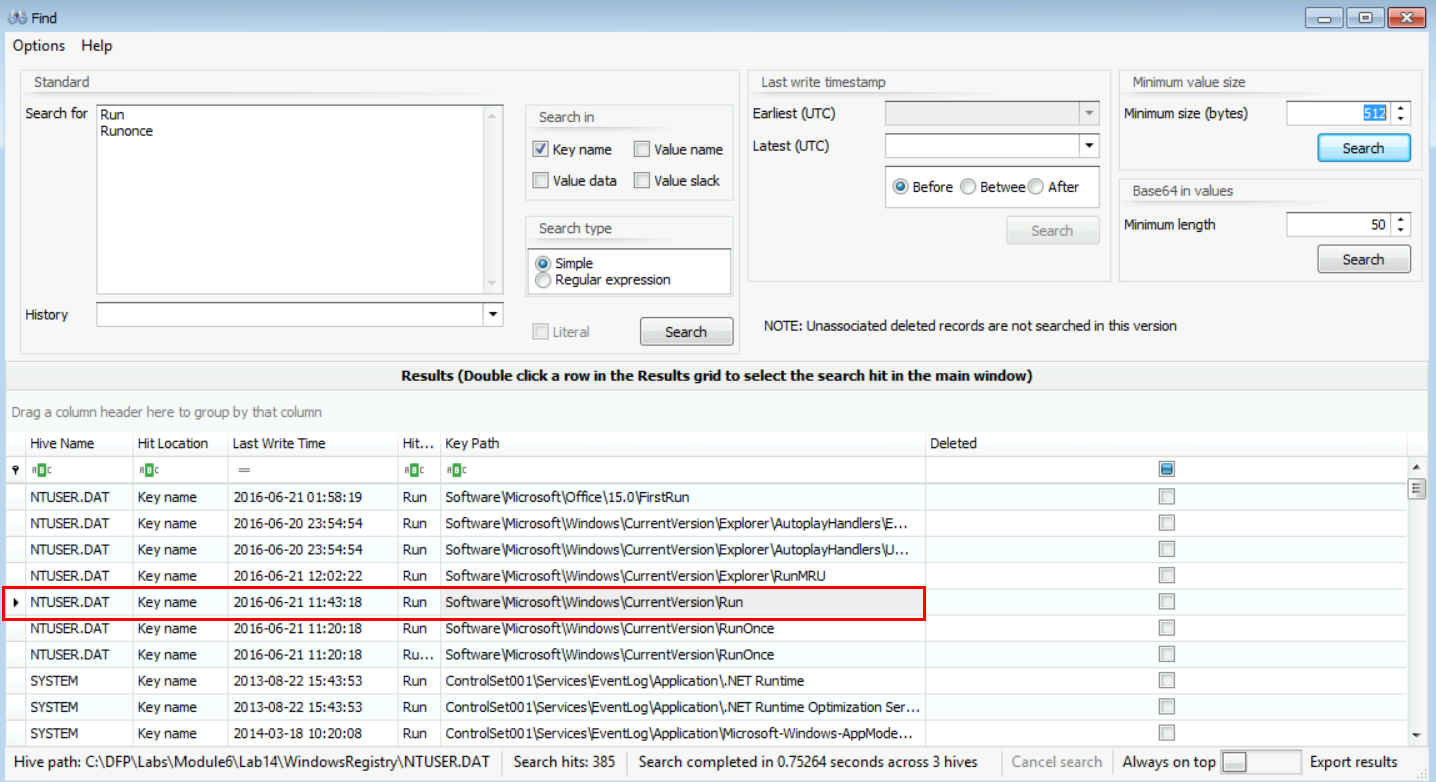
I double clicked on each of the entries starting from the first, especially since we do not know what exact value we could find the results in. Windows Registry Explorer comes really handy with its search capabilities in such cases.
Now, double-click on the entry that I've highlighted in the snapshot above in red, and proceed to the next step.
As you see in the snapshot below, we found Skype, GoogleDrive, and CCleaner!
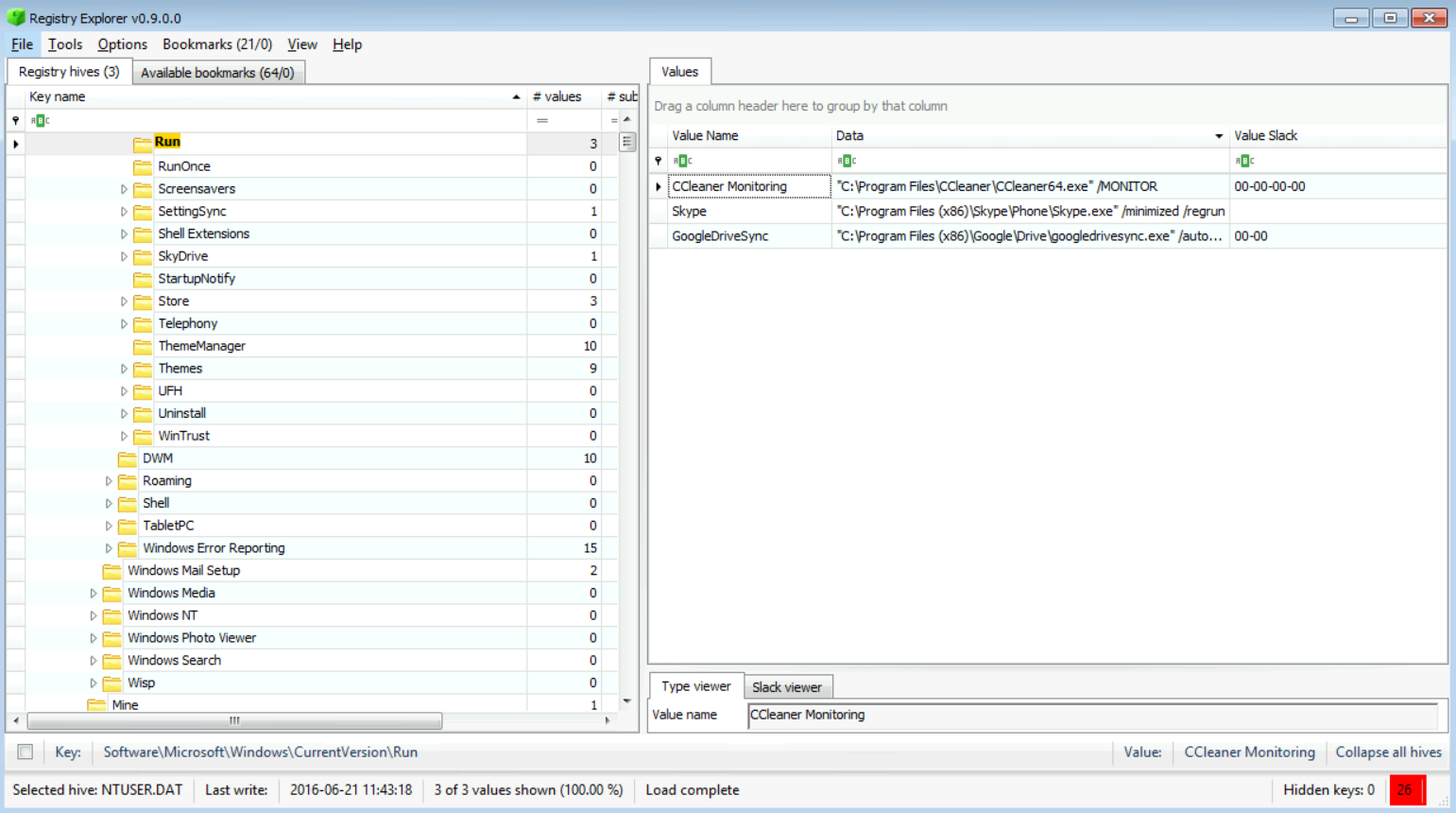
So, to answer the question, we found three, and they were: Skype, GoogleDrive, and CCleaner.
[Answer:] If the company's policy allows Skype, which lots of business environments today do, then, that Skype is okay. The same goes for GoogleDrive. But, for CCleaner? Why would you need that? It could be okay, and it could not be okay. So, I'm going with the hypothesis that CCLeaner isn't okay here.
Check both LastVisitedPidlMRU and OpenSavePidlMRU to understand some of the user's activity related to applications and files. These Keys could be found in the NTUSER.DAT hive file. Then, answer the questions below. So, navigate inside NTUDER.DAT until you reach:
\SOFTWARE\Mircosoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU
[Answer:] I found two, one .docx file and one .jpg file, as seen in the snapshot below:
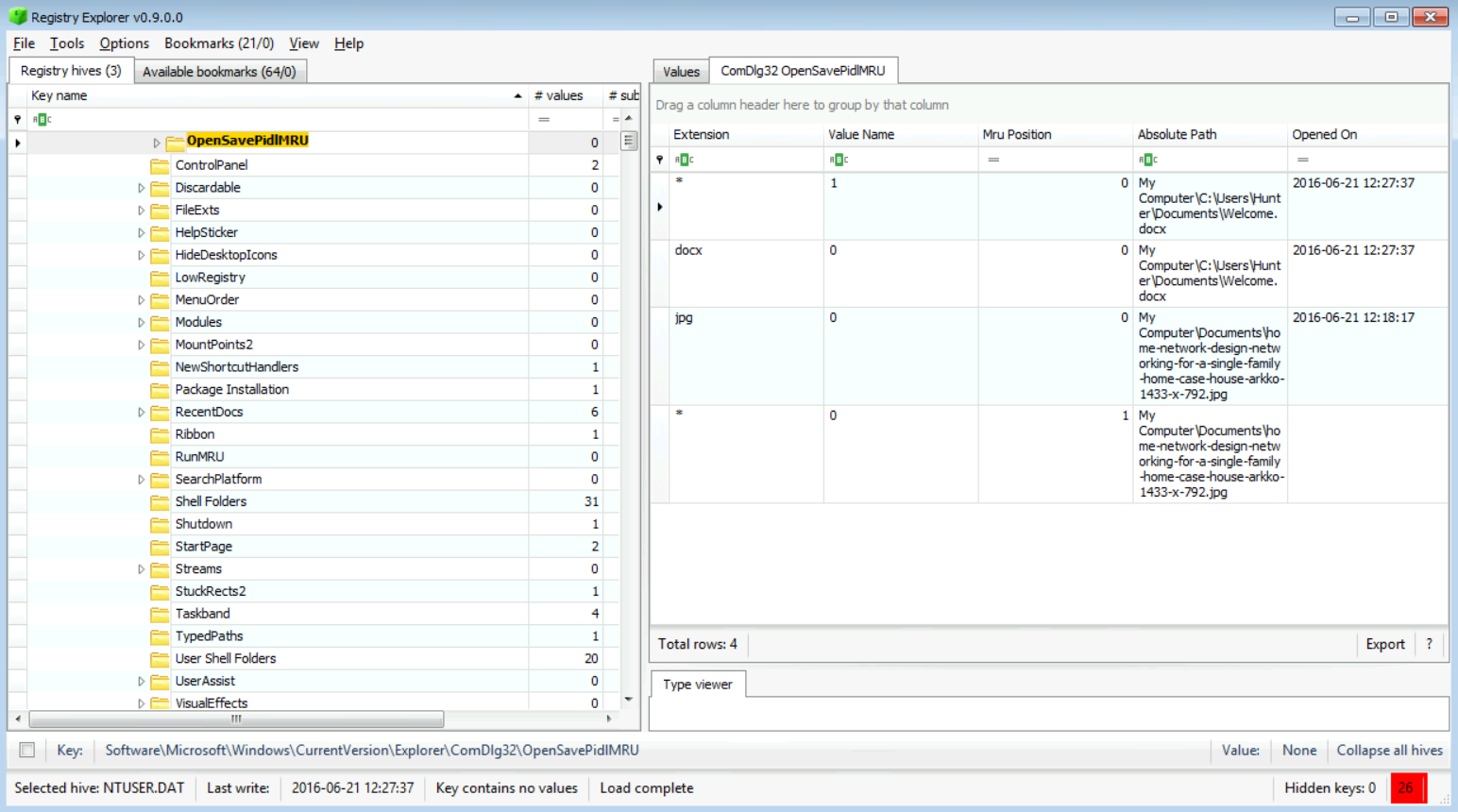
[Answer:] Yes, they are:
My Computer\C:\Users\Hunter\Documets\Welcome.docx
My Computer\Documets\home-network-design-networking-for-a-single-family-home-case-house-arkko-1433-x-792.jpg
Can you check their content, and is there anything suspicious about them?
[Answer:] If we were working on the whole forensic image, then we would have to locate them and then check whether they are suspicious or not. Since we are not working on the whole forensic image in this case and we only have some/parts of it to analyze, we will assume they are suspicious and move on with our investigation.
[Answer:] The last opened file was the "Welcome.docx" file. And the proof is from the "Opened on" date, which was "2016-06-21 12:27:37".
[Answer:] We see only one, which was chrome.exe.
[Answer:] To solve this, we need to go to the following location:
*NTUSER.DAT \Software \Microsoft \Windows \CurrentVersion \Explorer\RecentDocs\ *
This is another great location to check for recently used documents and files that is stored within the registry as a subkey. The values inside these subkeys are LNK files that we haven't analyzed yet (you will do so later in the course). For now, just let's just check what we found here, which was:
Welcome.docx
home-network-design-networking-for-a-single-family-home-case-house-arkko-1433-x-792.jpg
Exfil (this was a directory)
Exfiltration_Diagram.png
dns-exfiltration-using-sqlmap-18-728.jpg
There seems to be a lot going on this computer!!!
Now we need to move on to other questions related to the drives this user accessed or network shares etc. So, let us check what drives have been mounted on the system. Currently, we are only interested in listing the mounted devices; we will be doing further analysis later on when we get to the USB forensics lab
Let's navigate to SYSTEM\MountedDevices as seen below:
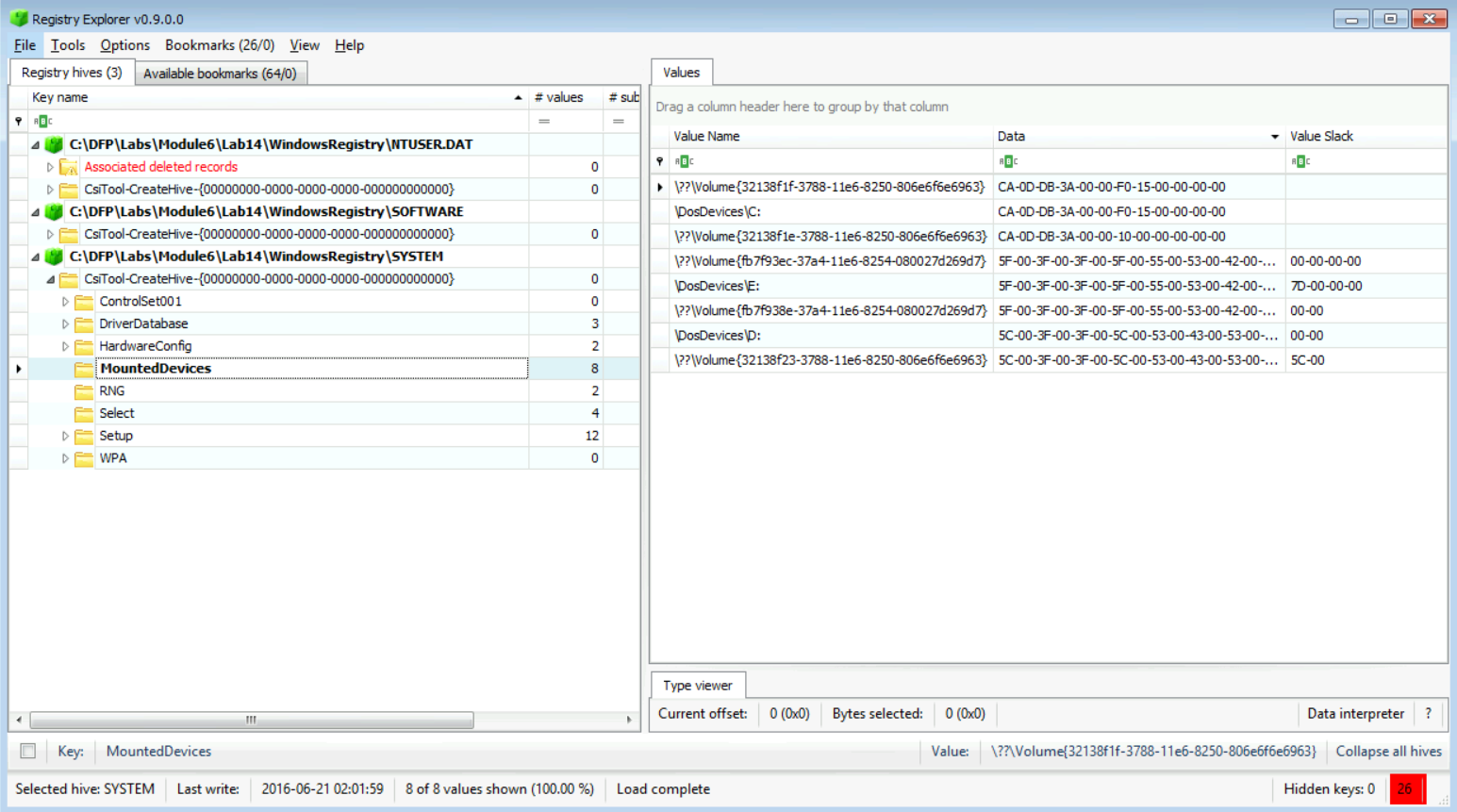
[Answer:] We actually found four volumes, which are: \??\Volume{32138f1e-3788-11e6-8250-806e6f6e6963} \??\Volume{32138f1f-3788-11e6-8250-806e6f6e6963} \??\Volume{fb7f938e-37a4-11e6-8254-080027d269d7} \??\Volume{fb7f93ec-37a4-11e6-8254-080027d269d7}
We can't say much here, because we need to do further USB forensics, but what I can say, is there is a C: which is usually used for the operating system, a D: which is used to mount DVD drives, and the E: which could most probably be used to mount USB devices to it.
[Answer:] Yes, they are C:, D:, and E:.
Our final step in this task will be to check the UserAssist keys and answer the questions given.
Let's start by navigating to the UserAssist location found within the NTUSER.DAT file:
NTUSER.DAT\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
The results could be seen below:
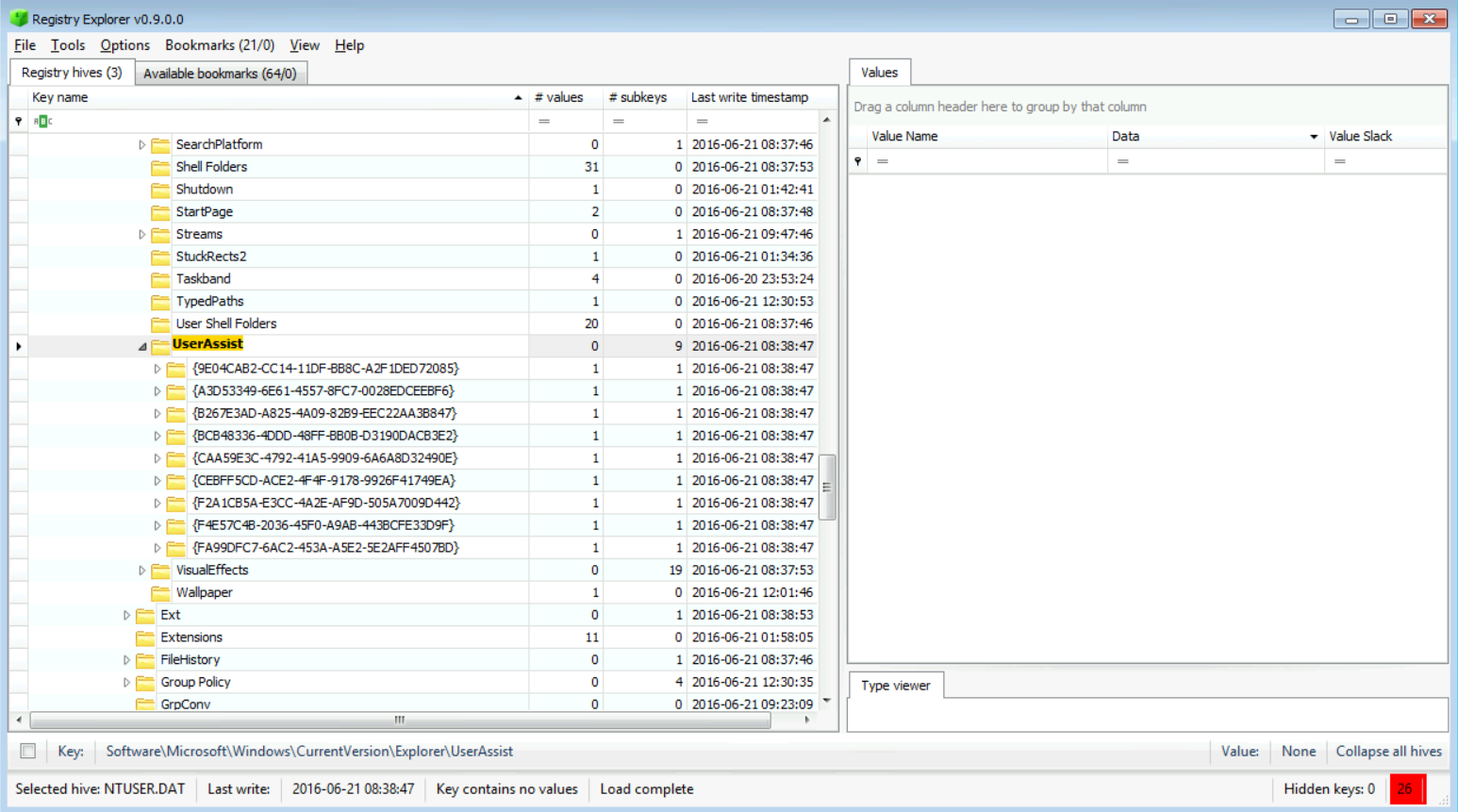
[Answer:] We found a total of 68 rows.
[Answer:] One sample is "7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Aznc\mraznc.rkr" which is actually the "Program Name{Program Files}\Nmap\zenmap.exe" value. Thanks to Windows Registry Explorer, it converts it back automatically for you.
This isn't encryption, it is only ROT13. More about ROT13 can be found here: https://en.wikipedia.org/wiki/ROT13
[Answer:] If we filter based on the "Run Counter" we find that Adobe Acrobat Reader was run 5 times. Anyway, we won't depend on this only, as we could check Prefetch files that we will analyze in the next upcoming labs.
[Answer:] From the entries, we can see that the user was using a couple of different tools. Zenmap|Nmap for network scanning, Putty for remote administration, Dropbox, and GoogleDrive for maybe sharing files, Readers and Cleaners like CCleaner, and finally even Wiping tools. So, there is a lot, but all depends on the policy at the company and what is allowed and what isn't.
[Answer:] It was run 3 times, as you can see in the snapshot below:
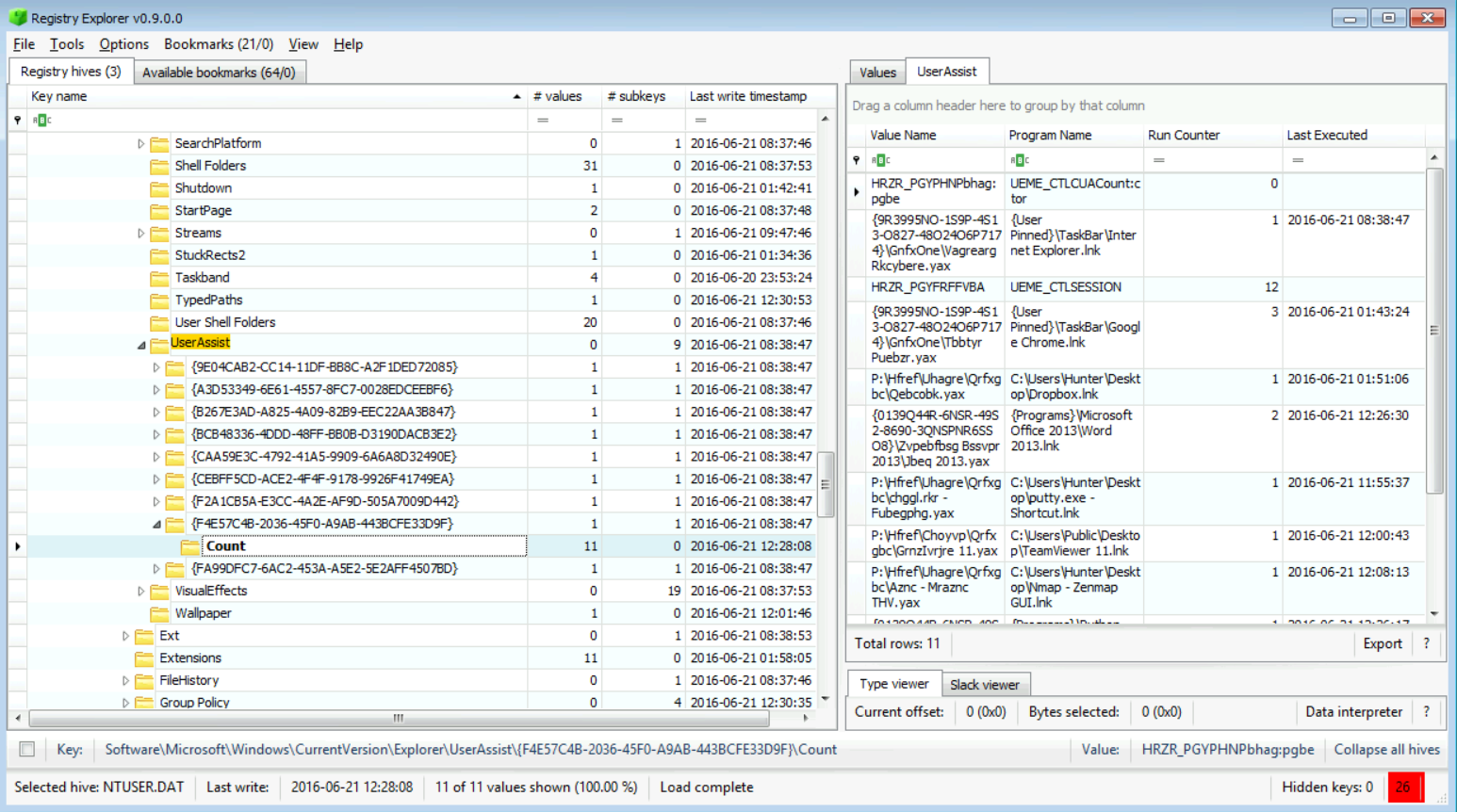
[Answer:] It was last executed on 2016-06-21 01:43:24, but I highly recommend that you also check the prefetch files (we will show you how later on in the course).
samparse v.20160203
(SAM) Parse SAM file for user & group mbrshp info
User Information
Username : Administrator [500]
Full Name :
User Comment : Built-in account for administering the computer/domain
Account Type : Default Admin User
Account Created : Tue Jun 21 08:19:47 2016 Z
Name :
Last Login Date : Tue Mar 18 10:20:36 2014 Z
Pwd Reset Date : Tue Mar 18 10:20:39 2014 Z
Pwd Fail Date : Never
Login Count : 3
--> Password does not expire
--> Account Disabled
--> Normal user account
Username : Guest [501]
Full Name :
User Comment : Built-in account for guest access to the computer/domain
Account Type : Default Guest Acct
Account Created : Tue Jun 21 08:19:47 2016 Z
Name :
Last Login Date : Never
Pwd Reset Date : Never
Pwd Fail Date : Never
Login Count : 0
--> Password does not expire
--> Account Disabled
--> Password not required
--> Normal user account
Username : Hunter [1001]
Full Name :
User Comment :
Account Type : Default Admin User
Account Created : Tue Jun 21 08:37:43 2016 Z
Name :
Password Hint : What do you do?
Last Login Date : Tue Jun 21 01:42:40 2016 Z
Pwd Reset Date : Tue Jun 21 08:37:43 2016 Z
Pwd Fail Date : Tue Jun 21 12:53:04 2016 Z
Login Count : 3
--> Password does not expire
--> Password not required
--> Normal user account
Username : HomeGroupUser$ [1003]
Full Name : HomeGroupUser$
User Comment : Built-in account for homegroup access to the computer
Account Type : Custom Limited Acct
Account Created : Tue Jun 21 08:40:06 2016 Z
Name :
Last Login Date : Never
Pwd Reset Date : Tue Jun 21 08:40:06 2016 Z
Pwd Fail Date : Never
Login Count : 0
--> Password does not expire
--> Normal user account
Group Membership Information
Group Name : Event Log Readers [0]
LastWrite : Thu Aug 22 14:45:11 2013 Z
Group Comment : Members of this group can read event logs from local machine
Users : None
Group Name : Guests [1]
LastWrite : Tue Jun 21 08:14:47 2016 Z
Group Comment : Guests have the same access as members of the Users group by default, except for the Guest account which is further restricted
Users :
S-1-5-21-2489440558-2754304563-710705792-501
Group Name : Network Configuration Operators [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Members in this group can have some administrative privileges to manage configuration of networking features
Users : None
Group Name : Performance Log Users [0]
LastWrite : Thu Aug 22 14:45:11 2013 Z
Group Comment : Members of this group may schedule logging of performance counters, enable trace providers, and collect event traces both locally and via remote access to this computer
Users : None
Group Name : Hyper-V Administrators [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Members of this group have complete and unrestricted access to all features of Hyper-V.
Users : None
Group Name : IIS_IUSRS [1]
LastWrite : Thu Aug 22 14:45:11 2013 Z
Group Comment : Built-in group used by Internet Information Services.
Users :
S-1-5-17
Group Name : Backup Operators [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Backup Operators can override security restrictions for the sole purpose of backing up or restoring files
Users : None
Group Name : Users [2]
LastWrite : Tue Jun 21 08:37:43 2016 Z
Group Comment : Users are prevented from making accidental or intentional system-wide changes and can run most applications
Users :
S-1-5-4
S-1-5-11
Group Name : Access Control Assistance Operators [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Members of this group can remotely query authorization attributes and permissions for resources on this computer.
Users : None
Group Name : Distributed COM Users [0]
LastWrite : Thu Aug 22 14:45:11 2013 Z
Group Comment : Members are allowed to launch, activate and use Distributed COM objects on this machine.
Users : None
Group Name : Administrators [2]
LastWrite : Tue Jun 21 08:37:43 2016 Z
Group Comment : Administrators have complete and unrestricted access to the computer/domain
Users :
S-1-5-21-2489440558-2754304563-710705792-1001
S-1-5-21-2489440558-2754304563-710705792-500
Group Name : Power Users [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Power Users are included for backwards compatibility and possess limited administrative powers
Users : None
Group Name : Cryptographic Operators [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Members are authorized to perform cryptographic operations.
Users : None
Group Name : Remote Management Users [0]
LastWrite : Thu Aug 22 14:45:11 2013 Z
Group Comment : Members of this group can access WMI resources over management protocols (such as WS-Management via the Windows Remote Management service). This applies only to WMI namespaces that grant access to the user.
Users : None
Group Name : Replicator [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Supports file replication in a domain
Users : None
Group Name : Performance Monitor Users [0]
LastWrite : Thu Aug 22 14:45:11 2013 Z
Group Comment : Members of this group can access performance counter data locally and remotely
Users : None
Group Name : Remote Desktop Users [0]
LastWrite : Tue Mar 18 09:52:38 2014 Z
Group Comment : Members in this group are granted the right to logon remotely
Users : None
Analysis Tips:
For well-known SIDs, see http://support.microsoft.com/kb/243330
S-1-5-4 = Interactive
S-1-5-11 = Authenticated Users
Correlate the user SIDs to the output of the ProfileList plugin
Not included due to file size.