Scenario
Through the next few tasks, you are required to examine a variety of Windows artifacts that were covered in the course. We have a case where we need to profile a suspect's activity to understand what he has been doing. This is going to be a really long journey, so grab the biggest cup of coffee you can get and let's get started.
You will find the evidence files for each task under a directory located here:
C:\DFP\Labs\Module6\Lab15\
- History -> includes searching cache files for Searches Performed (task #1)
- Recent -> includes LNK files (task #2)
- ShellBags -> includes files for shellbags (task #3)
- Prefetch -> includes files for prefecthes (task #4)
- ThumbCache -> includes files for thumbnails (task #5)
- JumpLists -> includes JumpLists (task #6)
- Libraries -> includes files for user Libraries (task #7)
Goals
- Analyze different Windows artifacts and understand what value each brings to the investigator
- Learn how to use different forensics tools that could help analyze Windows evidence
What you will learn
- You will learn how to analyze user search queries that have been performed on the system
- How to analyze recently used documents and what evidence do they support the investigator with
- Identify the directories a user has been to and what control panel accesses might a user have been doing
- Identify what applications a user has been using and how frequently have they been used
- Analyze thumbnail databases to locate evidence of illegal activity
- Analyze jump lists and libraries which Microsoft added to the system, so it enables better and more enriched user experience
Recommended tools
- Shellbags Explorer
- Notepad++ (any text editor)
- LNK Explorer
- PECmd.exe
- Thumbcache_viewer.exe
- WinPrefetchView.exe
- Jump List Explorer
SOLUTIONS
TASK 1: ANALYZING USER SEARCH QUERIES
Now to answer the questions. Usually, you will start by locating the evidence (already provided for you in this lab). The files for this lab are found at:
C:\DFP\Labs\Module6\Lab15\History
Since the system we are dealing with is Windows 8.1 (profiled in Lab #6.1 using registry keys), this gives us an idea of how and where we will find such evidence. Windows 8.1 stores search queries in the location found below as LNK files:
\%USERPROFILE%\AppData\Local\Microsoft\Windows\ConnectedSearch\History
Now based on the given evidence let us answer the questions.
-
What was the type of the search found?
[Answer:] The two LNK files given were:
txt_1051425824_en-US.lnk
site_1033182864_en-us.lnk
The file that starts with "txt_" means this is related to a keyword that was searched by the user or a term suggested by the system to him/her based on what he/she was searching for. However, the file that starts with "site_" refers to a website that the user searched for.
-
What did the user search for?
[Answer:] we need to analyze the files given to answer that. I will be using LECmd.exe from Eric Zimmerman, but you could use other tools, such as Exiftool if you want. So, now Open a CMD.exe, navigate to C:\DFP\Tools\Windows and then make sure you can access LECmd.exe by typing for example:
# LECmd.exe -h
Now to use the tool for analysis, run the tool against the LNK file like this:
# LECmd.exe -f "file.lnk"
So, now we do the following:
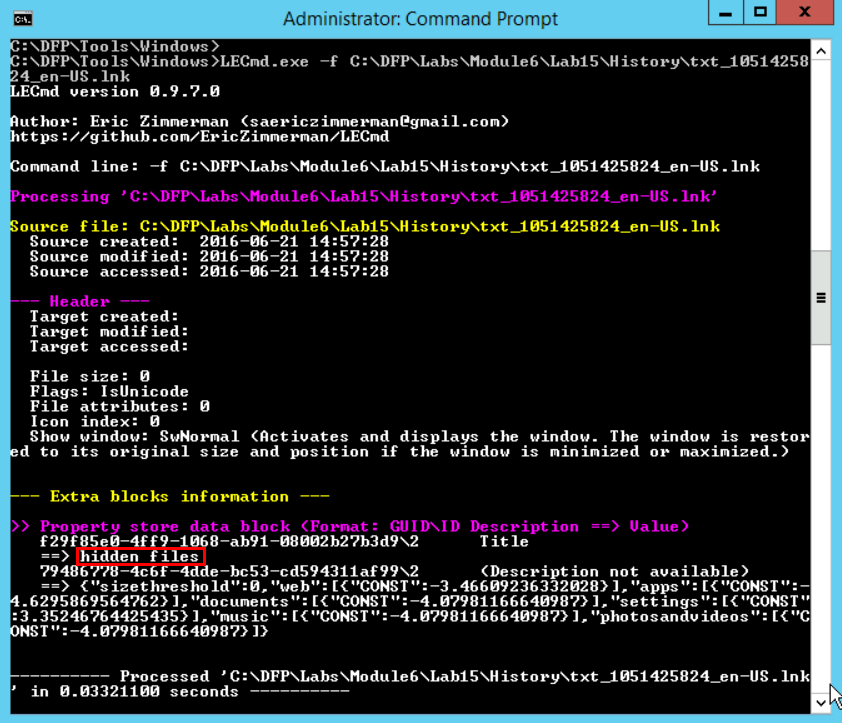
# LECmd.exe -f C:\DFP\Labs\Module6\Lab15\History\txt_1051425824_en-US.lnk
This tells us that the user was searching for the term "hidden files." As you can see in the figure below:
And when applying the following:
# LECmd.exe -f C:\DFP\Labs\Module6\Lab15\History\site_1033182864_en-us.lnk
We find that the user searched for the site: http://www.metasploit.com as seen in the figure below:
-
When was the creation time of the file?
[Answer:]
The file txt_1051425824_en-US.lnk was created on 2016-06-21 > 09:27:27
The file site_1033182864_en-us.lnk was created on 2016-06-21 > 09:27:00
-
When did the user perform this search?
[Answer:] The search was performed on those dates when the LNK files were created.
-
Do you think this is related to the incident responder or to the user himself, and why?
[Answer:] This is tricky, but since the system was not acquired on 06-21-2016, this means that most likely they were searches performed by the user.
[Extra:] A final addition to what we have done, is we could generate a CSV with all the details using LECmd.exe too. We can do that like this:
# LECmd.exe -d "History" --csv Results
We used this time "-d" instead of "-f" where we specified a whole directory here instead of a single file. This will result in a CSV file in the Results directory. Now, even if the Results directory does not exist, it will be created for you.
TASK 2: ANALYZING RECENTLY USED DOCS
If we were to extract the evidence related to RecentDocs, then that could be done by acquiring the LNK files from the location below:
%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\
But since you were already given that, you just need to continue with the files found in the "Recent" directory under Lab15. So the files for this lab are found at:
C:\DFP\Labs\Module6\Lab15\Recent
You can use whatever tool you want; I will continue to use Eric's LECmd.exe. To start, make sure you use the LECmd.exe, and then I will proceed and start answering the questions we have been given:
-
What was the type of the files found (URLs, Files, Executables, etc.)?
[Answer:] I can run the tool with the "-d" option to analyze the whole directory and generating a CSV or XML with all the results. After running the tool and analyzing the directory, it seems there are URLs, Executables, LNKs for pictures, and even LNKs for directories.
-
Which files did you find suspicious?
[Answer:] There were files for hacking activity, porn pics (ex: kittens), photos to network maps, and URLs to hacking tools.
-
Could you use the LNK file to locate the evidence on disk?
[Answer:] Yes, the full path to the file is stored in the LNK file. For example, if we take the "fakeporn.7z.lnk" file, we can find that the full path to the file is:
C:\Users\Hunter\Pictures\fakeporn.7z
You can check the figure below for that:
-
Why is there source and target MAC time stamps and what do they mean?
[Answer:] source is related to the LNK file itself while target relates to the actual file the LNK file is pointing to.
-
There was a LNK for a scan report, what is the name of the file, the timestamps (MAC times), and could you save some results for us?
[Answer:] the name of the file was "nmapscan.xml" which had the "nmapscan.xml.lnk" LNK file created for it. The file had the timestamps found below:
Source created: 2016-06-21 13:05:19
Source modified: 2016-06-21 12:13:57
Source accessed: 2016-06-21 12:13:57
Yes, I could easily save the results of the analysis by either using the JSON, XML, or CSV options provided or maybe just redirect the output to a file.
-
Could you form a hypothesis of what is the type of user activity done? Try to extract the files to support your case with good evidence.
[Answer:] Yes, it seems the user is related in some illegal activity relate to both hacking stuff and porn material.
TASK 3: ANALYZING SHELLBAGS (USRCLASS.DAT)
Now we turn to Shellbags, which are an excellent source for finding evidence of user activity. The first step we need to start our analysis is extracting the UsrClass.dat file which holds most of the directory preferences that we are concerned with to profile the user's activity. The file located in the following location:
%USERPROFILE%\AppData\Local\Microsoft\Windows
For this task, we have already been given the files needed, so let us analyze the given Shellbags using Shellbags Explorer at [C:\DFP\Tools\Windows\ShellBagsExplorer] and answer the questions below. The files for this lab are found at:
C:\DFP\Labs\Module6\Lab15\ShellBags
After loading the file with Shellbags Explorer, I assume you go the following:
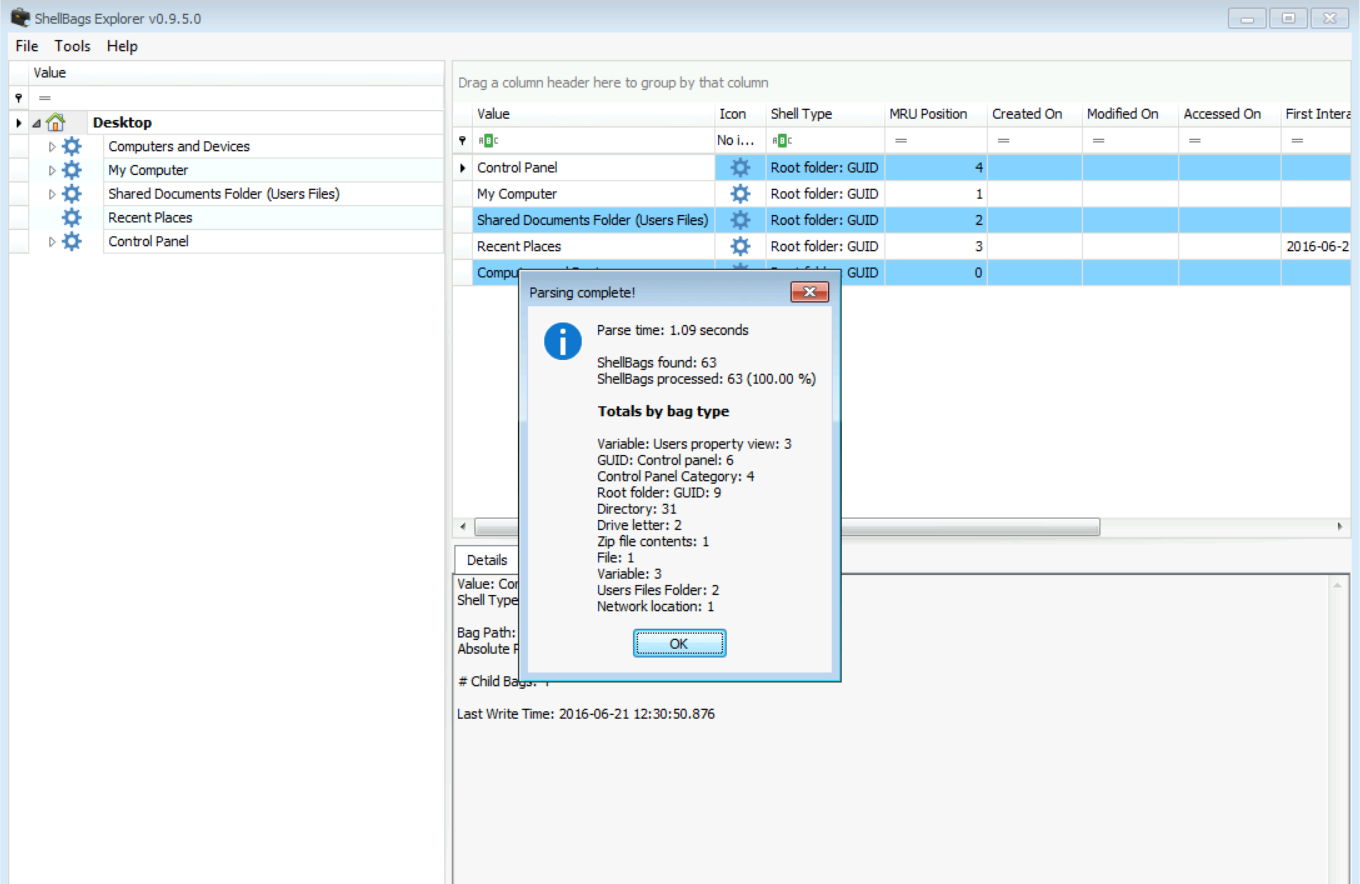
Now let's start using it to answer our questions.
-
If we exclude the Downloads\FTK-Imager entry since it's added there from the Incident Responder's acquisition toolkit, which entries do you find suspicious and why?
[Answer:] after expanding the entries and checking them, there seems to be some activity related to control panel and configurations such as Firewall and Recovery options, plus lots of others in this category. Also, there seems to be some directories related to porn, and finally files related to exfiltration and with Dropbox and GDrive leading to a conclusion that our suspect is maybe exfiltrating information using these two Cloud services, or maybe just one of them.
-
When were the two suspicious directories created and which one of them was accessed only once?
[Answer:] the best way to answer this question is to generate a CSV of all the shellbags and check which one of the suspicious directories have only a first accessed and no last accessed. We can do that using the CLI version of Shellbags Explorer named "SBECmd.exe" at [C:\DFP\Tools\Windows\ShellBagsExplorer]. We need to do the following:
# SBECmd.exe -d "PATH\To\UsrClass\Directory\" --csv Results\
This will generate a CSV file in the Results directory. You need to open it and find the two directories which are: Exfil and Fakeporn
-
Can you identify the file system being used and if 'Yes,' how?
[Answer:] Sure, it is an NTFS because there is an MFT Entry.
-
By checking the "All Control Panel Items," what do you think the user did on his machine?
[Answer:] He might have modified the Firewall settings, modified the applications associated with specific files, and finally modify configurations relate to the system recovery and power options, as seen in the figure below:
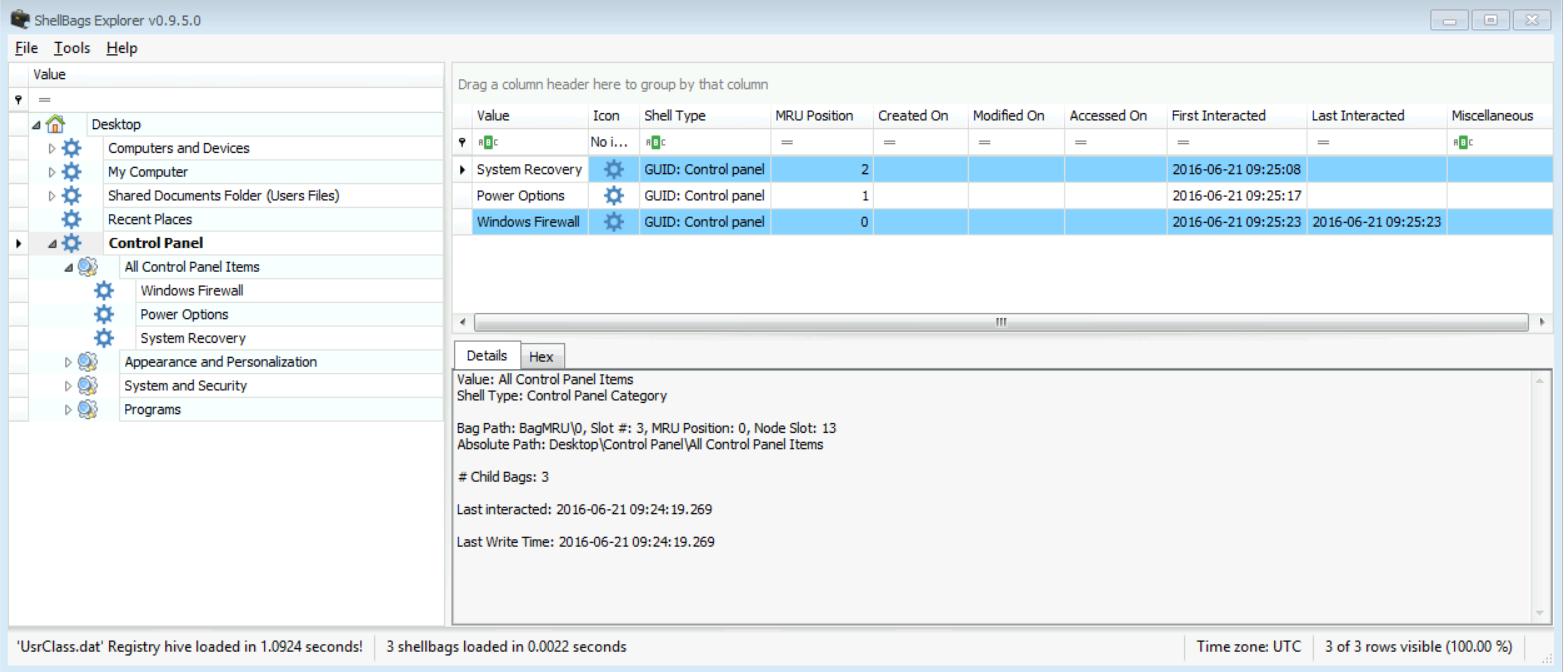
We can't take this as a final answer; we will need to correlate these results with actions that could be found in the Windows Events. There surely will be an Event generated after any of these actions done. So, an answer alone here will not be enough.
-
Which of the directories you found was the Most Recently Accessed Directory? How can you prove your answer?
[Answer:] We can use the CSV file generated to answer that easily. It is the "C:\Users\Hunter\Pictures" directory.
-
I assume you even managed to find archive file names here, right? What did you find?
[Answer:] Yes, it was the file "Hash_Suite_Free_3_4.zip" as you can see in the figure below:
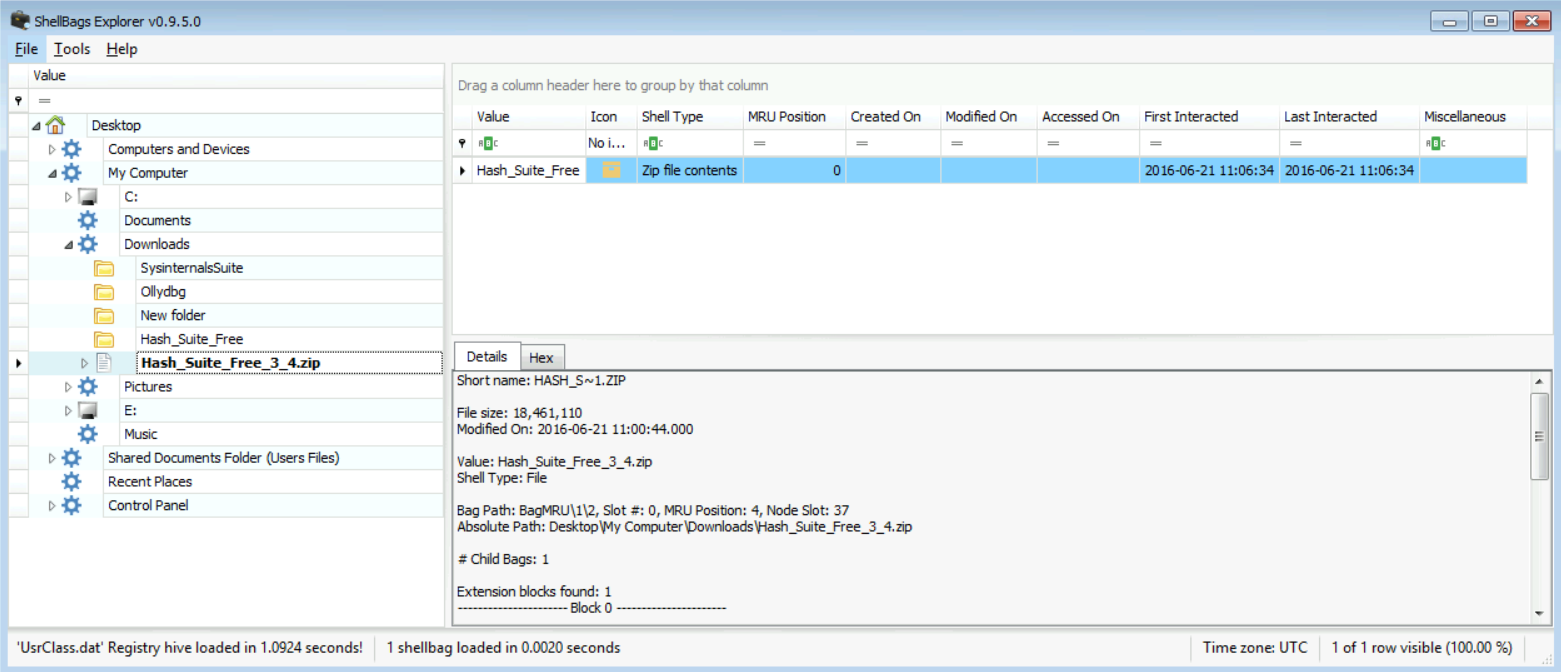
-
The user seems to have created a "New folder" inside the Downloads directory. After the user created this directory, he seemed to have changed its name to something else. From the directories you found, what is the new directory name? Explain your answer with strong and solid evidence.
[Answer:] the answer is the directory "Ollydbg." We can find that answer by checking the MFT number for the "New folder" directory and checking the MFT value for the other directories. The value was 89938, and this is the same value for the "Ollydbg" directory.
TASK 4: ANALYZING PREFETCH FILES
Let us use what we learned from our course to analyze the Prefetch Files given and then answer the questions given. For this section, to analyze the prefetch files that have been found within this given case, I will be using WinPrefetchView from NiroSoft, but please test Eric Zimmerman's PECmd tool too. Remember that all the prefetch files (.pf) are located in the *Prefetch** directory which is at:
%windir%\prefetch
The files for this lab are found at:
C:\DFP\Labs\Module6\Lab15\Prefetch
To make WinPrefetchView.exe analyze the whole prefetch directory at once, go to Options -> Advanced Options and make sure you select the prefetch folder that has our evidence. So, now let's start answering the questions:
-
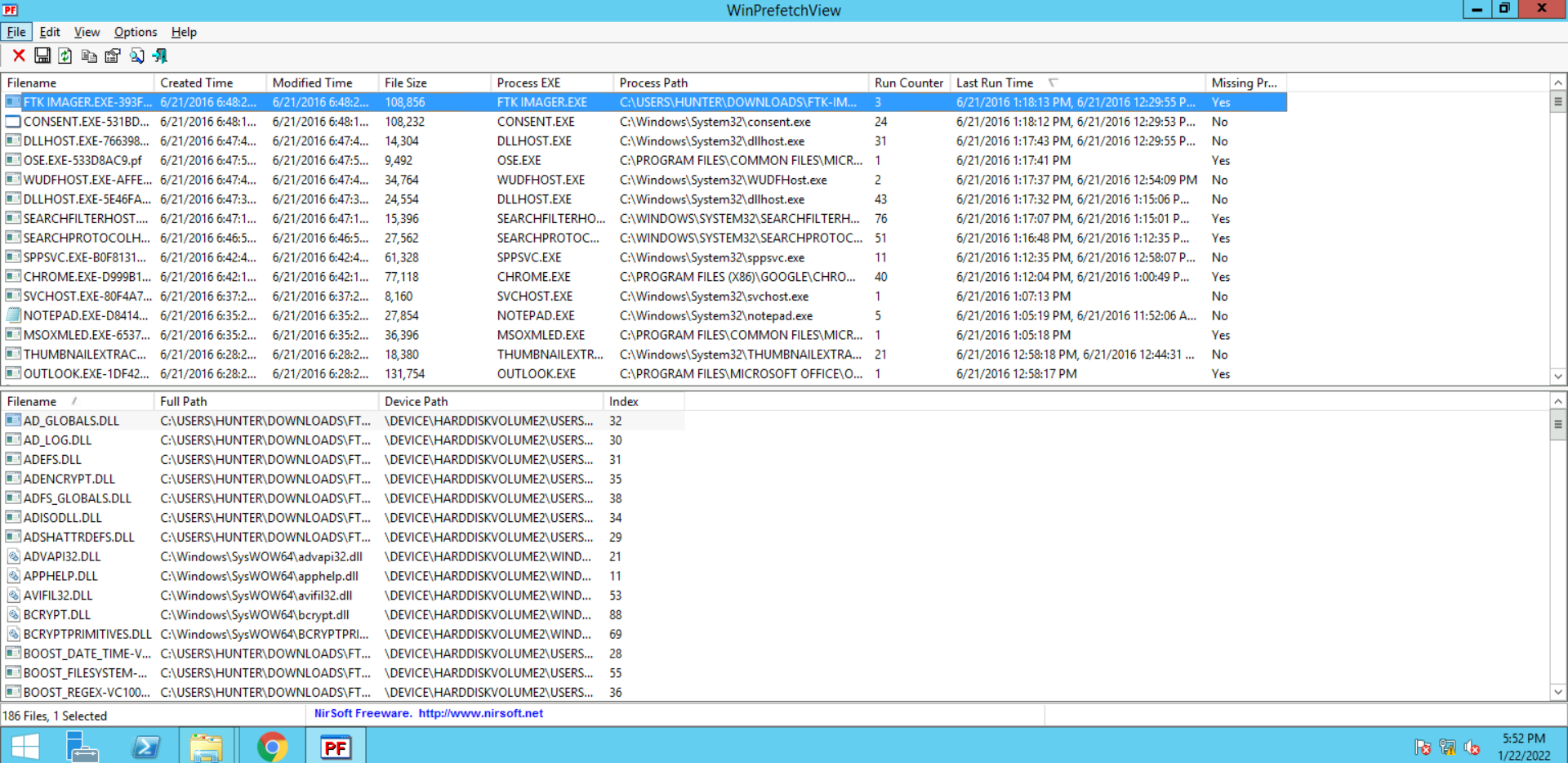
What are the top 5 most frequently run programs on the system and how many times has each one of them been run?
Answer: All we need to do here is sort the prefetch files using the "Run Counter" column in descending order. The result is:
> SEARCHFILTERHOST.EXE-77482212.pf -> run for 76 times
> SEARCHPROTOCOLHOST.EXE-0CB8CADE.pf -> run for 51 times
> CHROME.EXE-D999B1C2.pf -> run for 45
> DLLHOST.EXE-5E46FA0D.pf -> run for 43 times
> CHROME.EXE-D999B1BB.pf -> run for 40 times
2. What are the most 5 recent applications running on the system?
Answer: This time to answer this, we need to sort the prefetch files based on the "Last Run Counter." This will lead to the following:
> FTK IMAGER.EXE-393FFB9B.pf
> CONSENT.EXE-531BD9EA.pf
> DLLHOST.EXE-766398D2.pf
> OSE.EXE-533D8AC9.pf
> WUDFHOST.EXE-AFFEF87C.pf
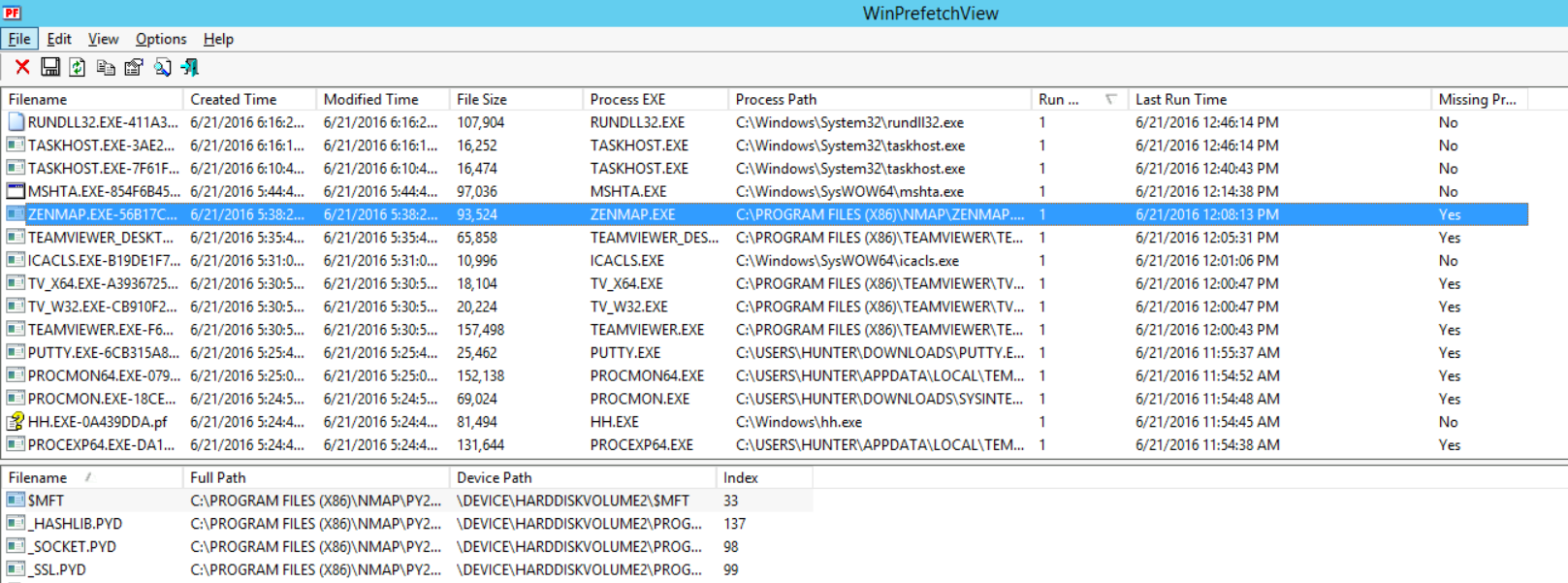
3. Has ZenMap been running on this system?
Answer: Yes, there is a prefetch file for it "ZENMAP.EXE-56B17C4C.pf" as seen in the figure below:
-
How many times has it been running?
Answer: only once, and this proves that he/she used Zenmap on his computer. If he/she isn't part of the team to run port scans, then this could be illegal.
-
When did the last run happen?
Answer: It was last run on "6/21/2016 12:08:13 PM". If this date, for example, is a holiday and no schedule for a scanning is done, then this is suspicious too.
-
What is the Hash value for Zenmap?
Answer: from the prefetch file name, we know that it was "56B17C4C".
[Note:] answers to Q5 and Q6 could also be seen in the figure above.
-
Which processes do you think are suspicious and why? List at least 2 of them, with:
a. Executable name
b. Last run time
c. Run count
d. Hash value
Answer: let us summarize the answer in the following table:
|Item |EXE Name |Last Run Time |Run Counter |Hash Value |
|---|---|---|---|---|
|1 |BCWipe.exe |6/21/2016 12:02:35 PM |5 |36F3F2DF |
|2 |Teamviewer.exe |6/21/2016 12:00:43 PM |1 |F6CE775B |
The reason behind my assumption is:
BCWipe -> this is used to wipe out files or content, which I may assume that he/she wanted to hide something.
Teamviewer -> this is used for remote access, which I may assume here he/she either had outside assistance, he used the machine remotely to do the tasks, etc.
This doesn't mean there aren't others, nor does it mean that whenever you see these executables it means they are bad, it totally depends on the case you are working on.
[Extra:] If you want to use PECmd.exe, then all you need to do to generate a full report using PECmd.exe is the following:
# PECmd.exe --d C:\DFP\Labs\Module6\Lab15\Prefetch --csv C:\DFP\Labs\Module6\Lab15\Prefetch\results
[Note:] those are two dashes "-."
The command above will generate two CSV files. One for the whole analysis, and one for a timeline of executable actions. So, you can open the analyzed CSV with your spreadsheet application and start analyzing it.
TASK 5: ANALYZING THUMBCACHES
Now let us turn our investigation to Thumbcache.db files that we discussed during the course. As we already know, these files serve as a basic database of thumbnails for picture files that are in a directory. Whenever you display the contents of a directory using thumbnail view or filmstrip, a Thumbcache.db with different sizes will be created depending on the user's size preferences.
An [important note] here is that we assume that pictures of kitties are bad!!!
I am going to use an easy to use tool named "thumbcache_viewer.exe". It should be found in the [C:\DFP\Tools\Others\thumbcache_viewer] directory. There is a CMD version of the tool if you like to use it too. Now, just to remind you that, to acquire the .db files from a system, they are located in the following location:
%USERPROFILE%\AppData\Local\Microsoft\Windows\Explorer
Checking this folder for .db files is much better and easier than going through the whole system for .db files as was done before (e.g., Windows XP). All the thumb caches on the system could already be found in the directory mentioned above.
The files for this lab are found at:
C:\DFP\Labs\Module6\Lab15\ThumbCache
For our test, please extract the files below then proceed to the next step:
1. iconcache_256.db
2. iconcache_32.db
3. thumbcache_48.db
4. thumbcache_96.db
Now open the application and start loading the application with each file and checking its content.
Now, let us start answering the questions, so open the tool and then load the given evidence file, then (note: it is not necessary that you get file #13 the same as the one in the figure below because it depends on how you loaded the files to Thumbcache Viewer):
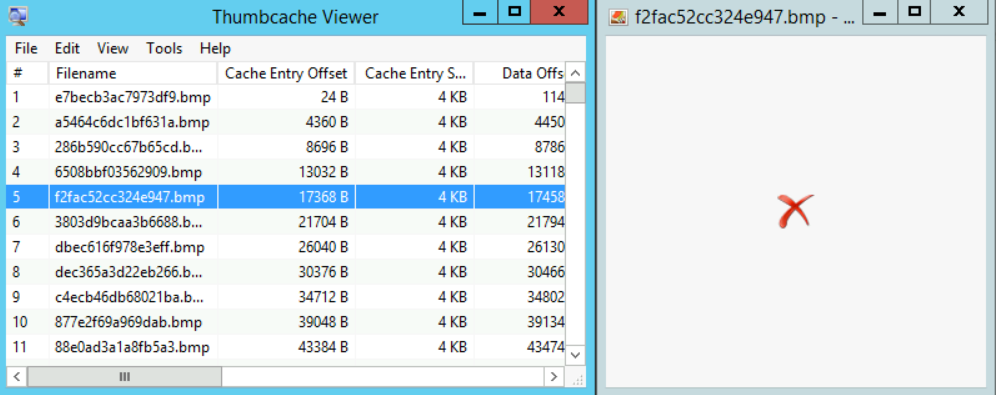
It is easy to use and straightforward:
-
Did you find any thumbnails to any illegal applications like Wireshark or TOR?
[Answer:] Yes, they had the following file names:
d60d6f93c96c9b93.png for Wireshark
and 70cb64a384ee465.png for TOR.
-
In which .db file did you find them?
[Answer:] Actually, I found them in both the "iconcache_48.db" and "iconcache_256.db". But the names I mentioned above in Q1, are from the "iconcache_256.db" file.
-
Could you locate these files on disk, and how will you do that?
[Answer:] We could do that by mapping thumbnails to files, using the Windows.edb file. This file is located in the following location:
C:\ProgramData\Microsoft\Search\Data\Applications\Windows
[Note:] this is for reference only since the full system image has not been given.
TASK 6: ANALYZING JUMP LISTS
We can use Windows Jump Lists to track some of the user's activity. This feature was explained during the course, so I presume you have an idea what we are talking about.
I will be using a tool called JumpList Explorer, also from Eric Zimmerman (he also has a CLI version of it). You can find it within the [C:\DFP\Tools\Others\JumpListExplorer] directory. Just as a reminder, you can find them in the following location:
%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\
The files for this lab are found at:
C:\DFP\Labs\Module6\Lab15\JumpLists
There are lots of things in this directory that we have already seen, but what we are interested here, is the AutomaticDestinations directory only and not the CustomDestinations directory.
First, start JumpList Explorer and then go to File -> Load jump lists or press the Alt+1 keys.
Now, let us start by analyzing the AutomaticDestinations first. So, make sure you load all of them into the application.
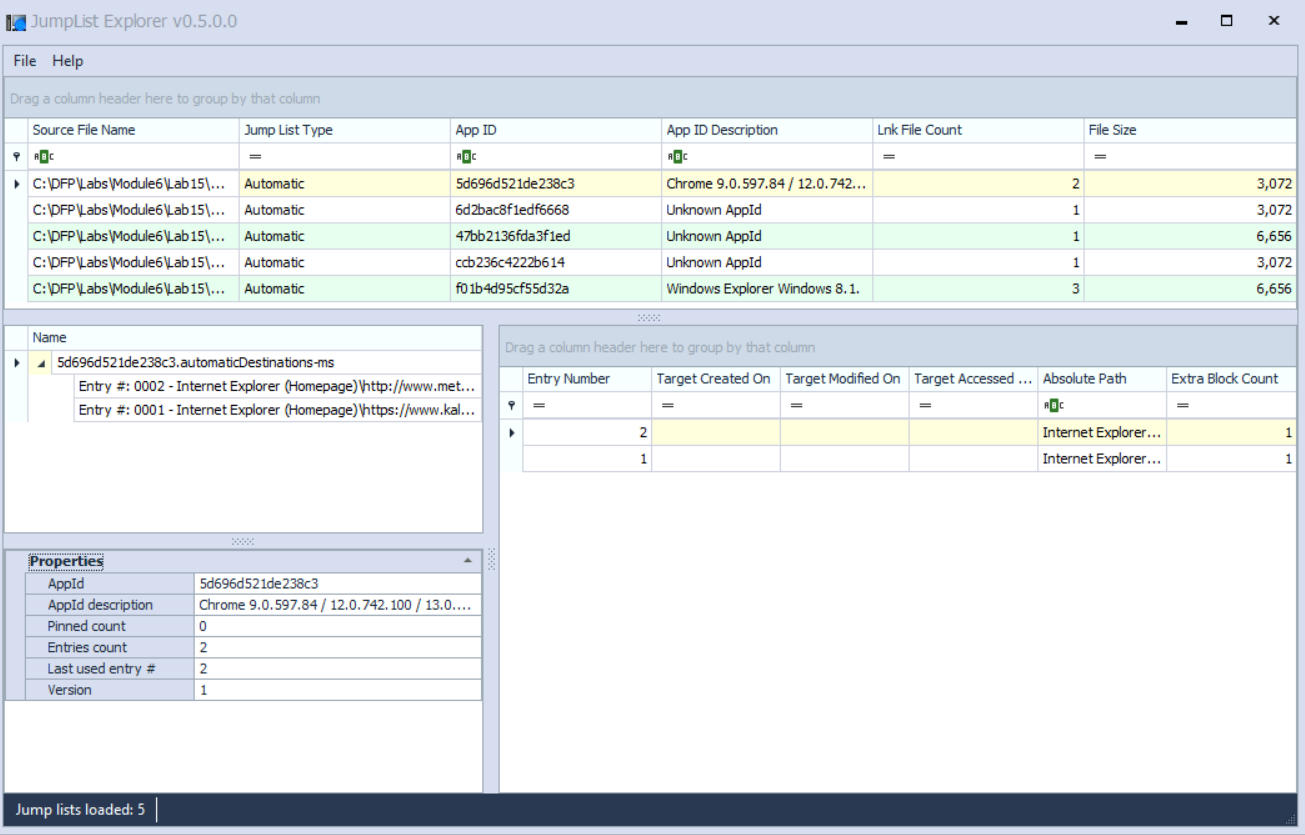
Select the jump list for the AppID that starts with 47bb2 and ends with 3f1ed.
Using the evidence given, let's start answering the questions:
-
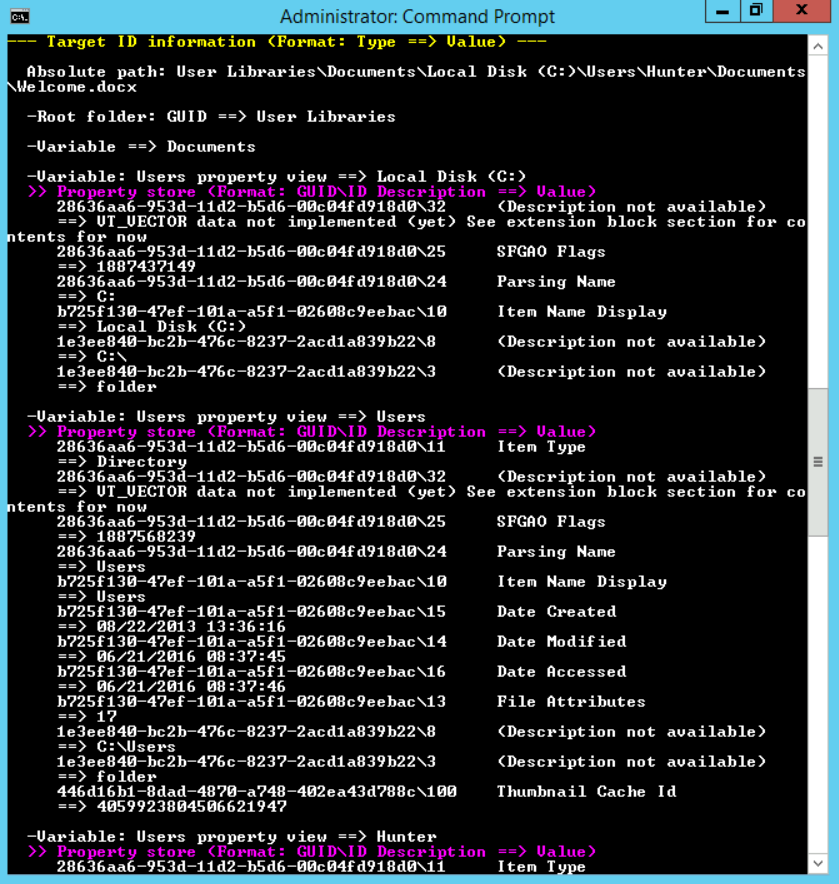
To what file or application does this jump list point to?
[Answer:] it points to the Welcome.docx file.
-
Can you identify the exact location of the target?
[Answer:] yes, it is. C:\Users\Hunter\Documents\Welcome.docx
-
What is the target creation date?
[Answer:] it was created at 2016-06-21 12:27:37, which was found in the TargetCreationDate field.
-
Can we identify the hostname of the system from a Jumplist, if "YES," what is it then?
[Answer:] since it was on the C:\ and we found that the NetworkShareInfo.NetworkShareName property holds \\4ORENSICS\Users; this means the hostname is most probably 4orensics.
-
Is this target pinned to the Windows task bar or not?
[Answer:] I don't think so because the "Pinned count" holds the value 0, not 1.
If you recall the executables that have been executed on this system, the user has run Nmap, which is a port scanner on his system.
-
Locate the jump list that is related to an Nmap activity, and then locate the target.
[Answer:] the jump list "ccb236c4222b614" is the one, as it refers to the nmap scanning report we found.
-
How can we know when was the port scan task performed? Any ideas?
Answer: the jump list for the nmap scan report was created at 2016-06-21 12:13:57, and if we check back the results of the Prefetch files, we will find that Nmap was last executed at 6/21/2016 12:10:51 PM, which leads us to assume this is true since this file is for the nmap results.
-
Does any of the jump lists you loaded contain some important data such as emails, credit card numbers, social security numbers, stuff like that? If you did, what is its AppID and what important stuff did it contain?
[Answer:] yes, I found stuff related to emails. I found a Jump List to an Outlook PST file. The AppID is "5d696d521de238c3".
-
Locate the jump lists that have pointers to folders. There should be three folders in it (Outlook, Desktop, and Exfil). Can you verify their creation dates with the information you retrieved from the UsrClass.dat (Shellbags), and are they identical?
[Answer:] Yes, the Jump List with the AppID "f01b4d95cf55d32a" had them.
The first directory "Exfil" was created on: 2016-06-21 09:37:36
The second directory "Desktop" was created on: 2016-06-21 08:37:46
The third directory "Outlook" was created on 2016-06-21 13:14:25
If we check their creation dates with the results from Shellbags, we get:
Exfil was created on: 2016-06-21 09:37:38.000
Desktop was created on: 2016-06-21 08:37:48.000
Those seem correct since it seems that Shellbags rounds the seconds. However, we couldn't find any direct evidence to Outlook, as it seems that this directory was not visited by the user, so there were no direct details about it. You can check file system level stuff for it though.
-
Did you find any jump list for URLs?
[Answer:] Yes, it contained two URLs.
-
What URLs has the user opened?
Answer: they were http://www.metasploit.com/ and https://www.kali.org/
-
How were they opened?
Answer: they were opened by Internet Explorer. It is clearly mentioned in Name Entry.
-
Is there anything suspicious about the site he visited?
[Answer:] if this user is not part of the security team, well then yes. Other than that, they for sure provide software used for hacking techniques, but that doesn't mean these websites are suspicious. So, it depends on how and from which point of view you're looking at the evidence.
Task 7: Checking for User Libraries
This is the final part of this lab, where we will be analyzing the user libraries that are available on this suspect's machine. Use the evidence given, but if you need a quick reminder, the evidence for libraries could be located here:
%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Libraries
The files for this lab are found at:
C:\DFP\Labs\Module6\Lab15\Libraries
Now on to the answers:
1. What libraries did you find?
Answer: I found four libraries, which are:
- Music
- Pictures
- Videos
- and Documents
2. Did you find anything suspicious?
Answer: No, they are simple XML files. You can open them and go through the text lines there, I didn't find anything suspicious, but it was good to check though.











