You're presented with a capture file which contains encrypted traffic; you need to add the proper certificate using Wireshark and examine the traffic unencrypted.
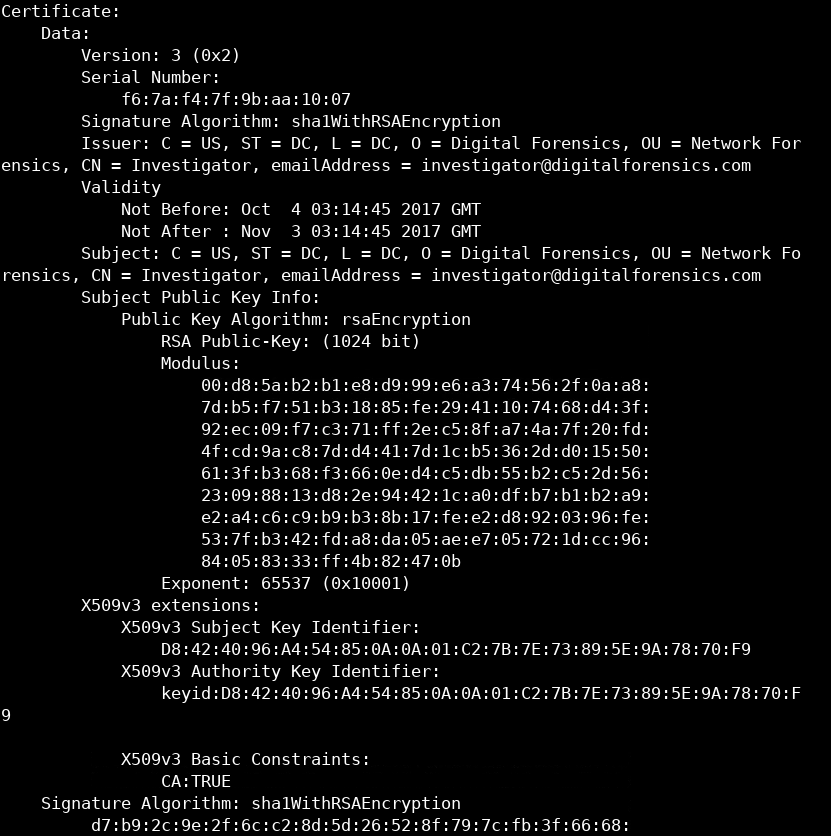
We can examine the certificate with openssl using the following command:
openssl x509 -in certname.pem -text -noout
The Certificate serial number is f6:7a:f4:7f:9b:aa:10:07. The signature algorithm is SHA1. The certificate country is the US, and the organization name is Digital Forensics and issued to Investigator. The public key of the RSA algorithm is 1024 bit long.
First, we need to filter unwanted packets so that we can examine the SSL traffic. We can do that by examining the traffic going to and from TCP port 443 since it is the default port for SSL. Using filter tcp.port==443.
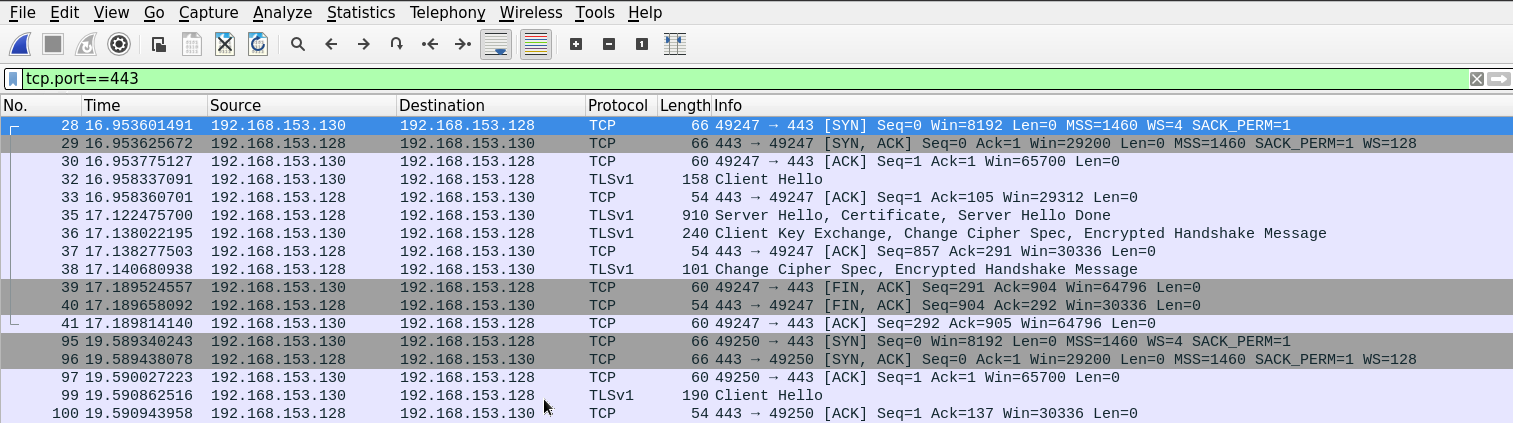
Since the filter we're using displays everything going through 443, Wireshark will also display the three-way-handshake and other TCP segments.
We can use another way to filter out TCP segments by using the SSL filter to display only relevant packets.
 The SSL client hello message can usually be found right after the three-way handshake.
The SSL client hello message can usually be found right after the three-way handshake.
Before we examine the client hello message, we should notice from the picture above; we can see that there were many attempts to start the SSL session.
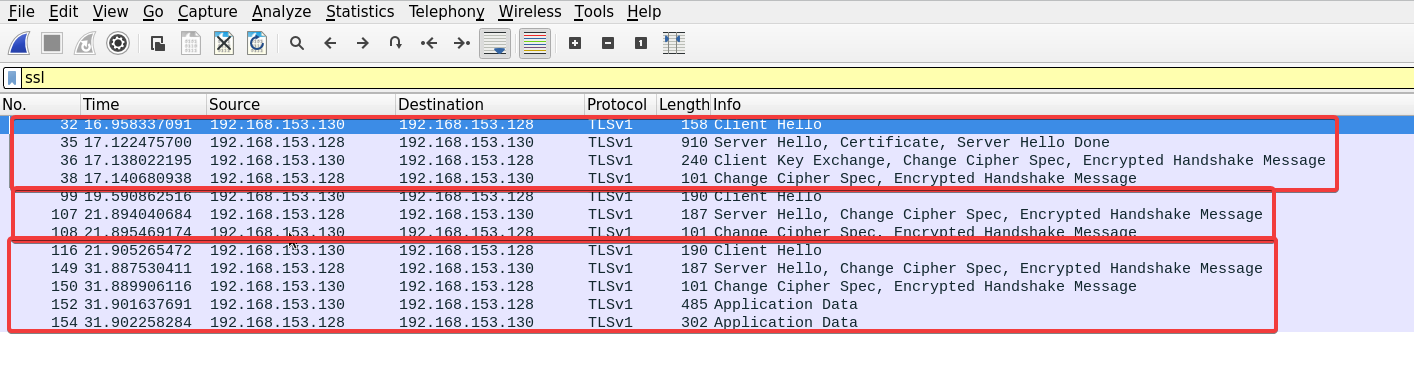
Only one of those attempts is followed by data exchange.
After examining the client hello message of the third connection, we can see the full list of ciphers sent by the clients to the server. Under the Transport Layer Security dropdown.
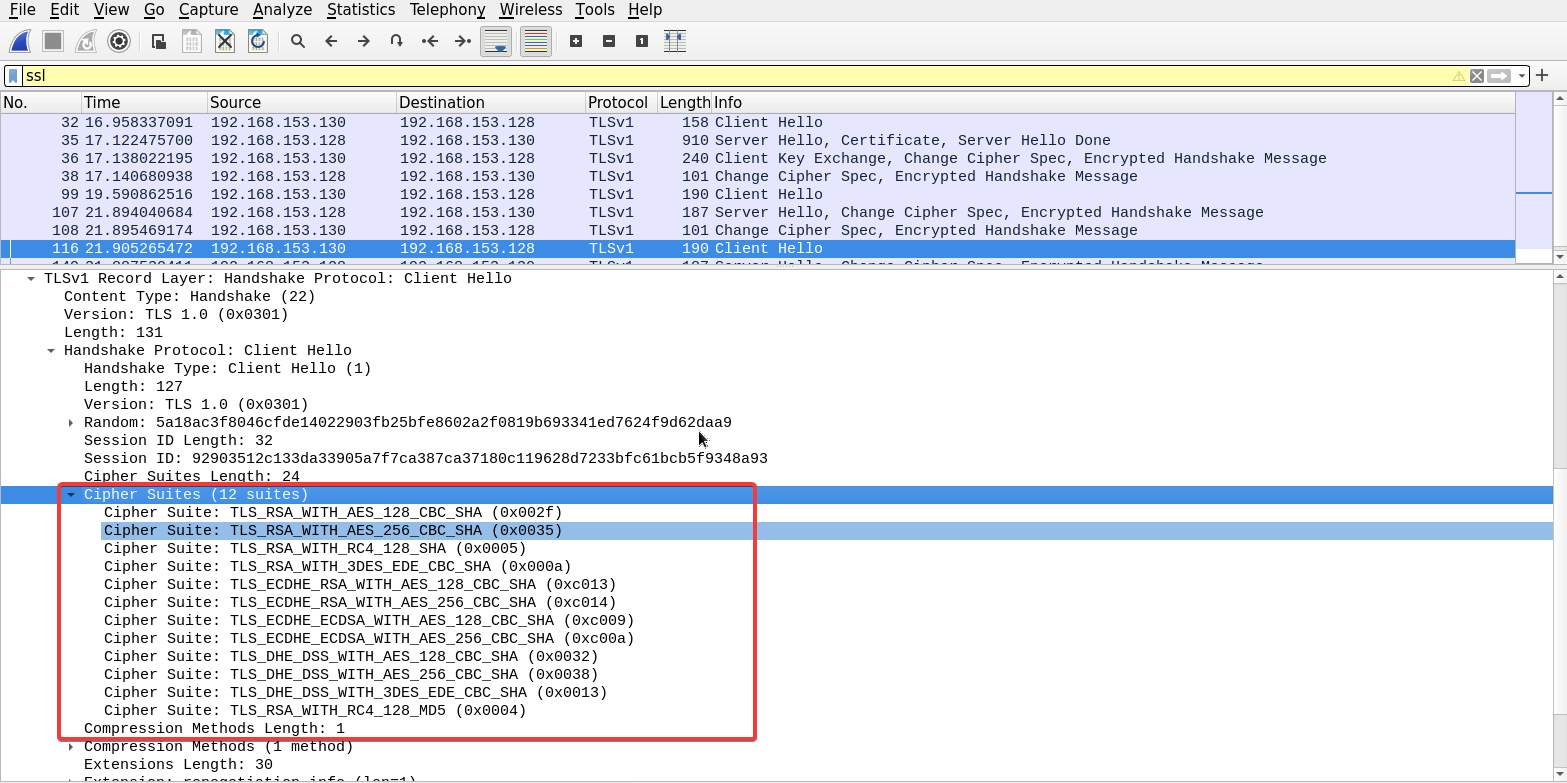
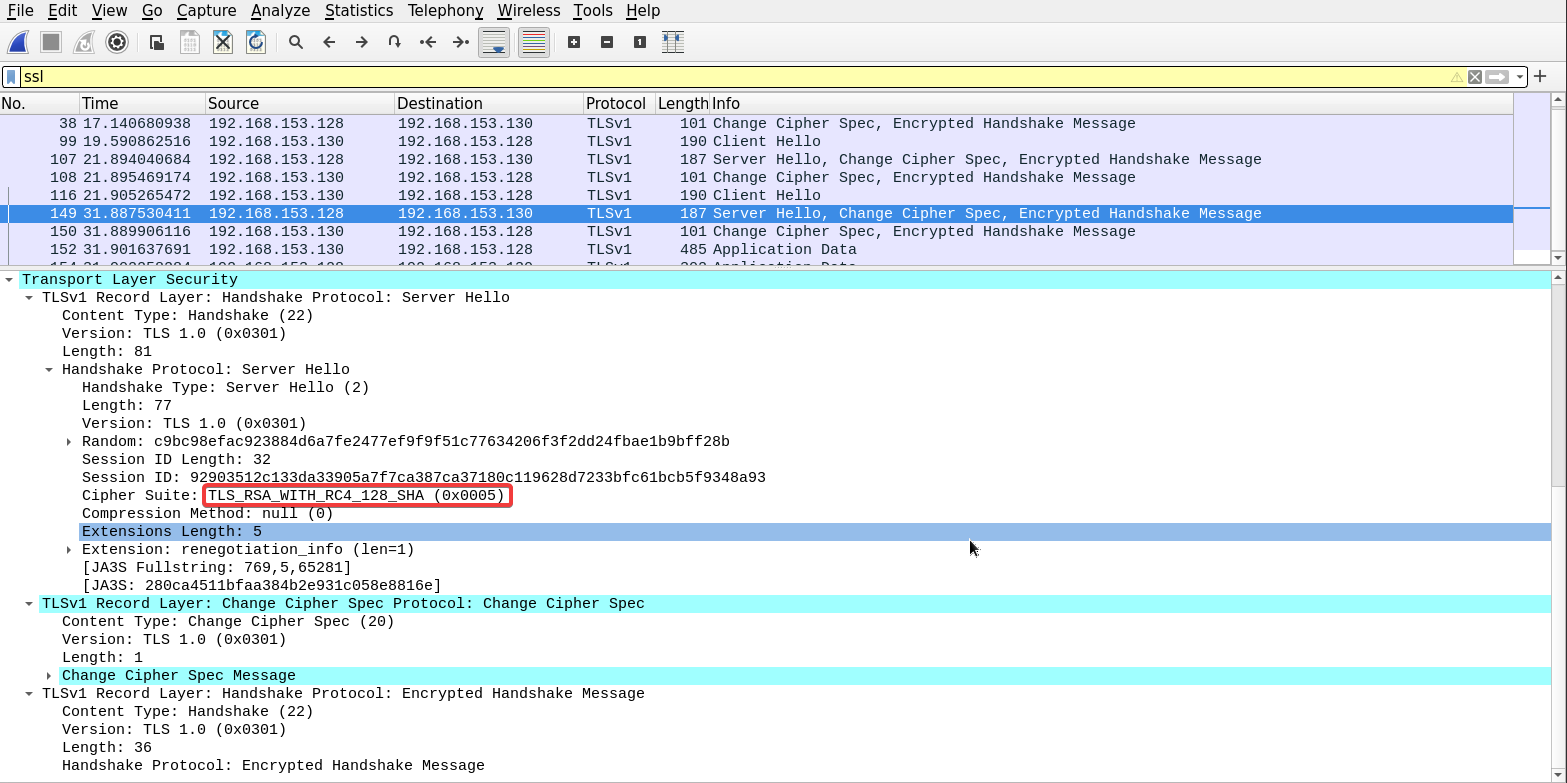
Using the same method, we can examine the Server hello message to find out which algorithm did the server choose to use to secure the connection.
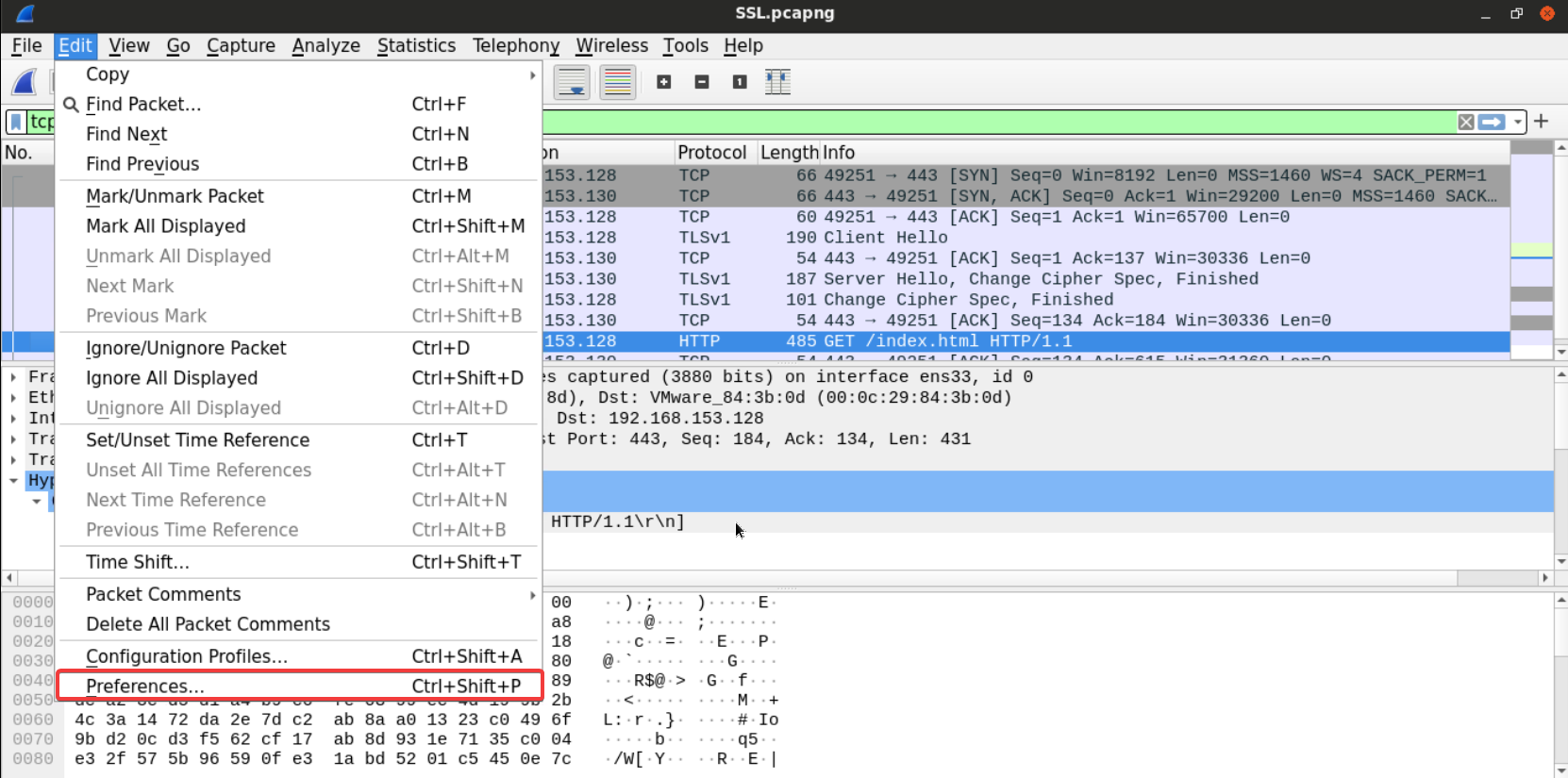
From the preference option under the edit tab...
Select the TLS option under the protocols.
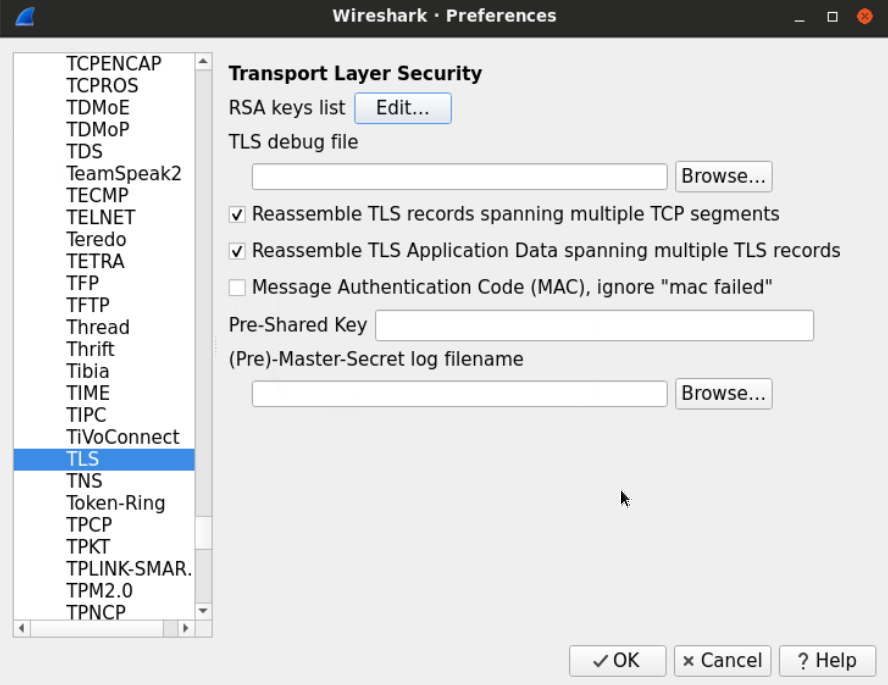
Edit the RSA keys list, and add the private key file named testkey2.pem, which can be found at Desktop/Module7/Lab24/testkey2.pem.
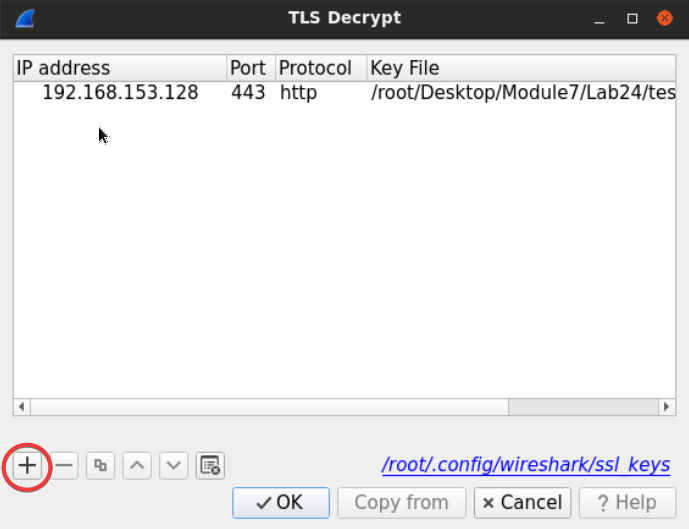
Add the IP Address of the server, port (443), the protocol we're tunneling (which is HTTP) and the file of the key.
[Note:] sometimes you will have to restart Wireshark for this to be effective!
We can follow the traffic of any TLS connection to make sure the key is working.
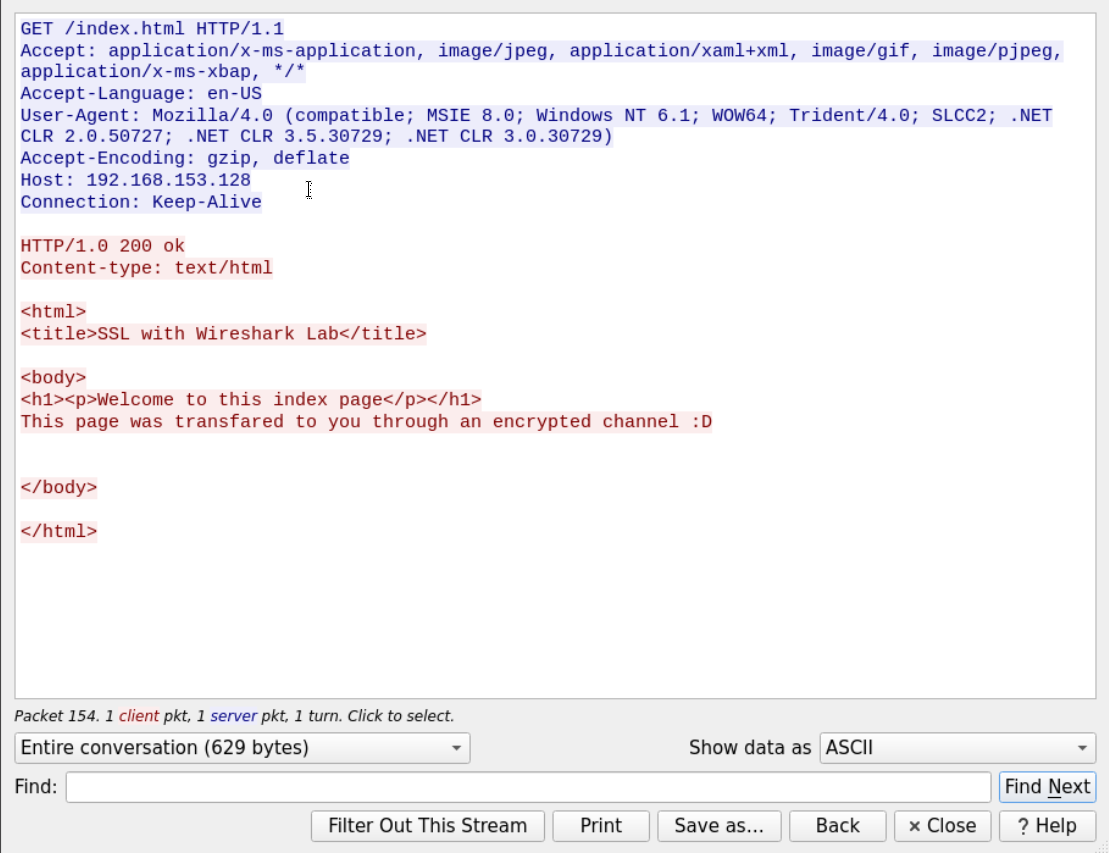
After adding the RSA key, you'll notice that some packets have changed from unknown SSL packets to some known protocol since the data got decrypted.
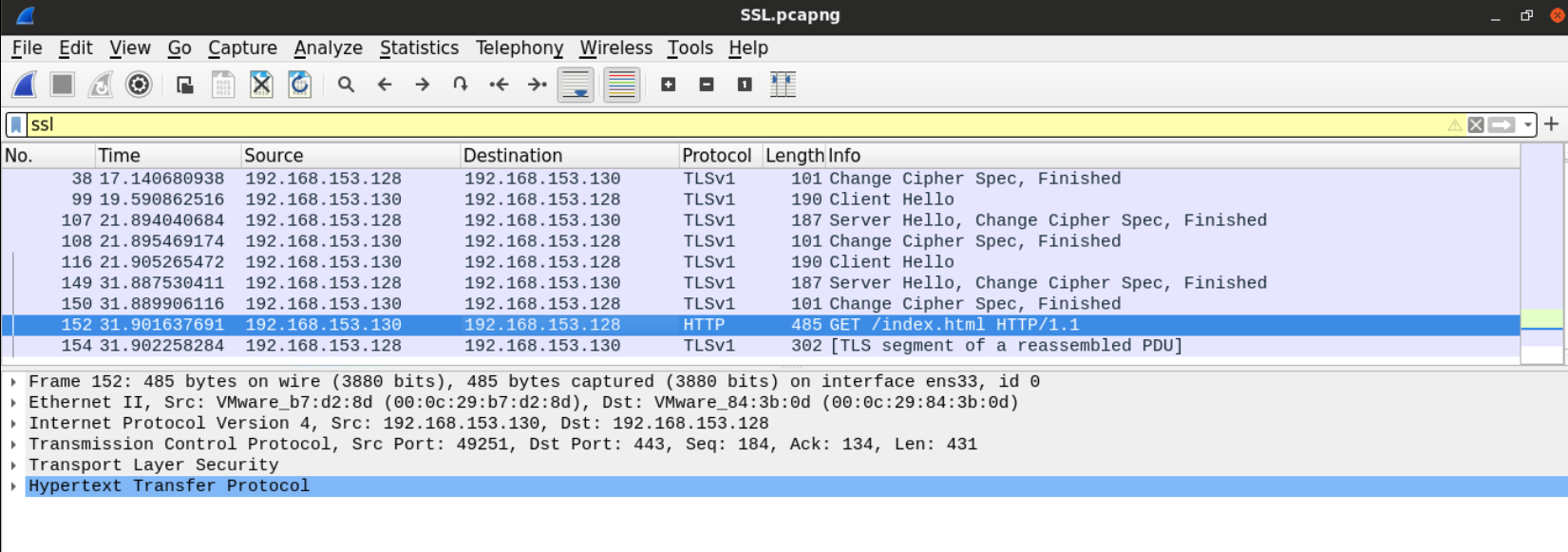
Now that we've decrypted the traffic, we can follow the SSL traffic and see that the client was requesting the serve default index page.