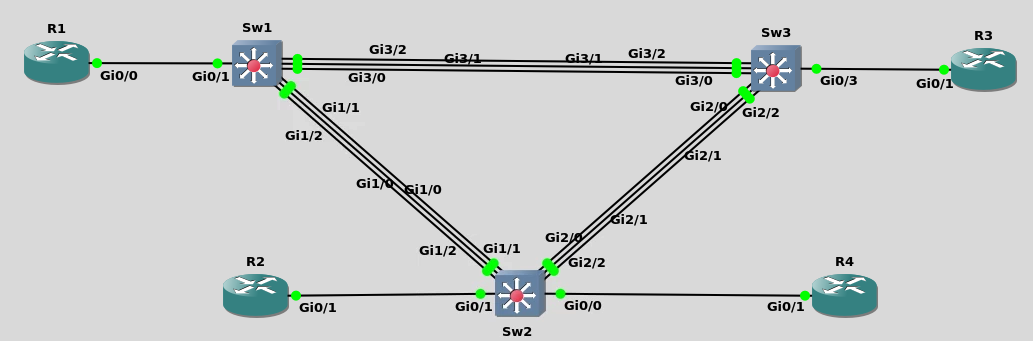

Helpful Hints about INE’s virtual lab environment:
If you ever lose console access to one (or more) of your devices you will need to reboot the Ubuntu Virtual Machine that is hosting your GNS3 lab environment. To do this,
Solutions:
To move from User EXEC to Privileged EXEC mode one issues the "enable" command:
Switch>
Switch>enable
Switch#
To configure a unique hostname within a switch (or router) one must first enter "Global Configuration Mode" by typing "configure terminal" (or "conf t") and then entering the command, "hostname" followed by a space and then your descriptive name for the device. When you are finished entering configuration commands you leave Global Configuration Mode by entering the "end" command.
Switch#configure terminal
Switch(config)#hostname Switch-1
Switch(config)#end
One can apply configuration commands to individual interfaces on a switch or a range of interfaces. In this step it would have been easiest to implement the "interface range" command to allow you to shutdown multiple interfaces at once as follows:
Switch-1#configure terminal
Switch-1(config)#interface range GigabitEthernet1/0 - 2
Switch-1(config-if-range)#shutdown
Switch-1(config-if-range)#end
By default, Cisco switches have VLAN 1 as their management VLAN. We can assign an IP address in the VLAN 1 interface, which can be used to access that particular switch via remote access tools such as Telnet, SSH, etc.
Historically, early Cisco switches were only Layer-2 devices, which (just like a laptop or PC) needed to be configured with a default-gateway using the "ip default-gateway" command to make them accessible from different networks. Unlike a Layer 3 device, a Layer-2 switch cannot route the packets because it only works based on the destination mac address. In today's modern networks most switches are "Multilayer Switches" which means that (like routers) they can run routing protocols and route packets. But for this introductory lab, we'll treat these three switches as if they did not have that capability and were Layer-2 only.
Sw1:
enable
!
configure terminal
!
interface vlan 1
ip address 10.1.1.1 255.255.255.0
no shutdown
end
Sw2:
enable
!
configure terminal
!
interface vlan 1
ip address 10.1.1.2 255.255.255.0
no shutdown
end
Sw3:
enble
!
configure terminal
!
interface vlan 1
ip address 10.1.1.3 255.255.255.0
no shutdown
end
To configure a default-gateway in each switch follow this pattern:
Sw1:
enable
!
configure terminal
!
ip default-gateway 10.1.1.10
end
Now configure Sw1 as the telnet server. Notice the command below of "transport input telnet". Some IOS devices default to allowing incoming sessions of both Telnet and SSH. Other IOS devices have a default behavior of not allowing any kind of incoming session. Because you may not know (from device to device) what its default behavior is, this particular command explicitly tells the device to listen to, and respond to, incoming Telnet requests.
Sw1:
enable
!
configure terminal
!
line vty 0 4
transport input telnet
password cisco
!
enable password cisco
To configure an Enable password (which will display in cleartext in the output of your configuration file) and then save your configuration changes do the following:
Sw1:
enable
!
configure terminal
!
enable password cisco
end
copy running-config startup-config
(One could also use the command, "write mem")
Verification
Initially, we can check for the IP addressing and reachability information between all the switches in this topology. When it is successful, we can check for the telnet session to Sw1 from Sw2 (and even Sw3 if you wish). We can use some kind of output modifier to get clean output, as shown here.
Sw1#show ip interface brief | exclude unassigned
Interface IP-Address OK? Method Status Protocol
Vlan1 10.1.1.1 YES manual up up
Sw1#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/2/8 ms
Sw1#ping 10.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/3/9 ms
Sw2#show ip interface brief | exclude unassigned
Interface IP-Address OK? Method Status Protocol
Vlan1 10.1.1.2 YES manual up up
Sw2#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Sw2#ping 10.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/3/4 ms
Sw3#show ip interface brief | exclude unassigned
Interface IP-Address OK? Method Status Protocol
Vlan1 10.1.1.3 YES manual up up
Sw3#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Sw3#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/4 ms
To validate Telnet simply login to Switch-2 and issue the command, "Telnet 10.1.1.1". This will cause Switch-2 to initiate a TCP session with Switch-1 using a destination TCP port of 23 (for Telnet). Because you enabled the Telnet protocol on Switch-1 you should be prompted for a password (which is "cisco"). Type in that password and the device prompt should now validate that you are within Switch-1's IOS CLI.