
Helpful Hints about INE’s virtual lab environment:
If you ever lose console access to one (or more) of your devices you will need to reboot the Ubuntu Virtual Machine that is hosting your GNS3 lab environment. To do this,
Solutions:
Initial Configuration Solutions:
The following commands would be applied to all devices:
hostname [Device Hostname]
!
enable password cisco
!
no ip domain-lookup
!
interface GigabitEthernetX/Y
no shutdown
!
line con 0
logging synchronous
R1 Telnet commands:
line vty 0 4
password cisco
login
transport input telnet
R2 SSH commands:
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#ip domain-name ine.com
R2(config)#ip ssh version 2
Please create RSA keys to enable SSH (and of at least 768 bits for SSH v2).
R2(config)#crypto key generate rsa
The name for the keys will be: R2.ine.com
Choose the size of the key modulus in the range of 360 to 4096 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non- exportable...
[OK] (elapsed time was 1 seconds)
R2(config)#
*Jul 26 20:14:11.257: %SSH-5-ENABLED: SSH 2.0 has been enabled
R2(config)#username ine privilege 15 password cisco
WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
R2(config)#
*Jul 26 20:14:30.792: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
R2(config)#line vty 0 4
R2(config-line)#transport input ssh
R2(config-line)#login local
R2(config-line)#end
R2#
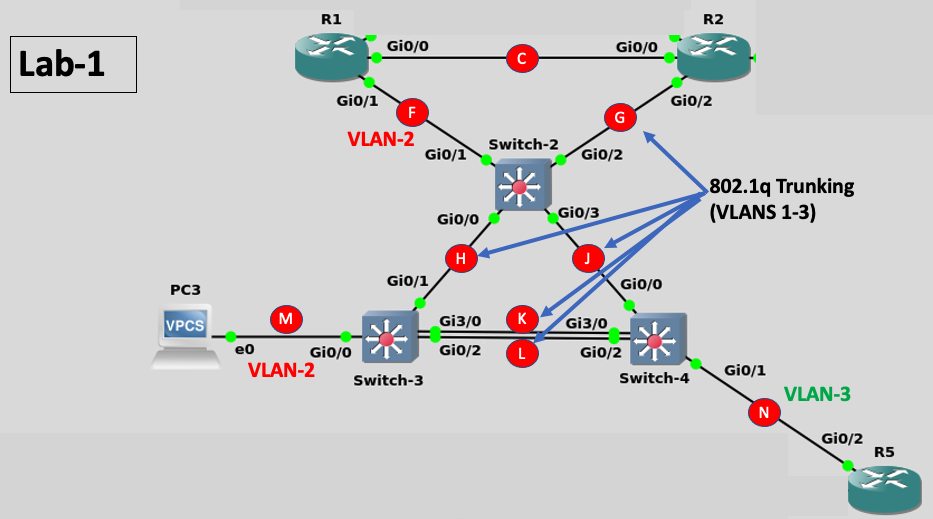
Implementing Basic Switching Solutions:
Only relevant portions of the switch configuration are shown below:
Switch-2#sh run
Building configuration...
!
hostname Switch-2
!
vlan 2-3
!
!
interface GigabitEthernet0/0
switchport trunk encapsulation dot1q
switchport mode dynamic desirable
!
interface GigabitEthernet0/1
switchport access vlan 2
switchport mode access
!
interface GigabitEthernet0/2
switchport trunk encapsulation dot1q
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet0/3
switchport trunk native vlan 2
switchport trunk encapsulation dot1q
switchport mode dynamic desirable
!
!
end
Switch-2#
[Only relevant portions of the configuration are shown below]
Switch-3#sh run
Building configuration...
!
vlan 2-3
!
interface GigabitEthernet0/0
switchport access vlan 2
switchport mode access
!
interface GigabitEthernet0/1
switchport trunk encapsulation dot1q
switchport mode dynamic auto
!
interface GigabitEthernet0/2
switchport trunk encapsulation dot1q
switchport mode dynamic desirable
!
interface GigabitEthernet3/0
switchport trunk encapsulation dot1q
switchport mode dynamic desirable
!
end
Switch-3#
[Only relevant portions of the configuration are displayed]
Switch-4#show run
Building configuration...
!
hostname Switch-4
!
!
vlan 2-3
!
interface GigabitEthernet0/0
switchport trunk native vlan 2
switchport trunk encapsulation dot1q
switchport mode dynamic auto
!
interface GigabitEthernet0/1
switchport access vlan 3
switchport mode access
!
interface GigabitEthernet0/2
switchport trunk encapsulation dot1q
switchport mode dynamic auto
!
interface GigabitEthernet3/0
switchport trunk encapsulation dot1q
switchport mode dynamic auto
!
end
Switch-4#
IP Addressing and Subnetting Solutions:
| Link ID | Qty of Hosts | Subnet Mask | Network/Prefix |
|---|---|---|---|
| M/F/G | 29 | 255.255.255.224 | 10.10.10.0 |
| N/G | 12 | 255.255.255.240 | 10.10.10.32 |
| C | 2 | 255.255.255.252 | 10.10.10.48 |
| Device | Interface | IPv4 Address |
|---|---|---|
| R1 | Gig0/0 | 10.10.10.49 /30 |
| R1 | Gig0/1 | 10.10.10.2 /27 |
| R2 | Gig0/0 | 10.10.10.50 /30 |
| R2 | Gig0/2.2 | 10.10.10.30 /27 |
| R2 | Gig0/2.3 | 10.10.10.46 /28 |
| R5 | Gig0/2 | 10.10.10.33 /28 |
| PC3 | Eth0 | 10.10.10.1 /27 |
R1 IPv4 interface configuration:
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#int gig 0/0
R1(config-if)#ip address 10.10.10.49 255.255.255.252
R1(config-if)#no shutdown
R1(config-if)#exit
R1(config)#
*Jul 28 18:57:52.480: %LINK-3-UPDOWN: Interface GigabitEthernet0/0, changed state to up
*Jul 28 18:57:53.480: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
R1(config)#int gig 0/1
R1(config-if)#ip add 10.10.10.2 255.255.255.224
R1(config-if)#no shutdown
R1(config-if)#end
R1#
R2 IPv4 interface configuration:
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#interface gig0/0
R2(config-if)#ip address 10.10.10.50 255.255.255.252
R2(config-if)#no shutdown
R2(config-if)#exit
*Jul 28 19:00:02.188: %LINK-3-UPDOWN: Interface GigabitEthernet0/0, changed state to up
*Jul 28 19:00:03.188: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
R2(config-if)#exit
R2(config)#interface gig 0/2
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface gig 0/2.2
R2(config-subif)#encapsulation dot1q 2
R2(config-subif)#ip address 10.10.10.30 255.255.255.224
R2(config-subif)#exit
R2(config)#interface gig 0/2.3
R2(config-subif)#encapsulation dot1q 3
R2(config-subif)#ip address 10.10.10.46 255.255.255.240
R2(config-subif)#end
R5 IPv4 interface configuration:
R5#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R5(config)#interface gig0/2
R5(config-if)#ip address 10.10.10.33 255.255.255.240
R5(config-if)#no shutdown
R5(config-if)#end
PC3 IPv4 Addressing Configuration
PC3> ip 10.10.10.1/27 10.10.10.30
Checking for duplicate address...
PC3 : 10.10.10.1 255.255.255.224 gateway 10.10.10.30
Verification of IPv4 Addressing
Pinging various addresses from PC3
PC3> ping 10.10.10.49 -c 2
84 bytes from 10.10.10.49 icmp_seq=1 ttl=255 time=12.907 ms
84 bytes from 10.10.10.49 icmp_seq=2 ttl=255 time=9.861 ms
PC3> ping 10.10.10.2 -c 2
84 bytes from 10.10.10.2 icmp_seq=1 ttl=255 time=6.282 ms
84 bytes from 10.10.10.2 icmp_seq=2 ttl=255 time=6.699 ms
PC3> ping 10.10.10.50 -c 2
84 bytes from 10.10.10.50 icmp_seq=1 ttl=255 time=7.710 ms
84 bytes from 10.10.10.50 icmp_seq=2 ttl=255 time=8.574 ms
PC3> ping 10.10.10.30 -c 2
84 bytes from 10.10.10.30 icmp_seq=1 ttl=255 time=7.186 ms
84 bytes from 10.10.10.30 icmp_seq=2 ttl=255 time=9.011 ms
PC3> ping 10.10.10.46 -c 2
84 bytes from 10.10.10.46 icmp_seq=1 ttl=255 time=7.251 ms
84 bytes from 10.10.10.46 icmp_seq=2 ttl=255 time=9.625 ms
PC3>
Validating that R5 can SSH into R2:
R5#ssh -l ine 10.10.10.46
**************************************************************************
* IOSv is strictly limited to use for evaluation, demonstration and IOS *
* education. IOSv is provided as-is and is not supported by Cisco's *
* Technical Advisory Center. Any use or disclosure, in whole or in part, *
* of the IOSv Software or Documentation to any third party for any *
* purposes is expressly prohibited except as otherwise authorized by *
* Cisco in writing. *
**************************************************************************
Password:
**************************************************************************
* IOSv is strictly limited to use for evaluation, demonstration and IOS *
* education. IOSv is provided as-is and is not supported by Cisco's *
* Technical Advisory Center. Any use or disclosure, in whole or in part, *
* of the IOSv Software or Documentation to any third party for any *
* purposes is expressly prohibited except as otherwise authorized by *
* Cisco in writing. *
**************************************************************************
R2#
Seeing R2's prompt is proof that R5 was successful in SSHing into R2.
Validating that R2 can Telnet into R1:
R2#telnet 10.10.10.49
Trying 10.10.10.49 ... Open
**************************************************************************
* IOSv is strictly limited to use for evaluation, demonstration and IOS *
* education. IOSv is provided as-is and is not supported by Cisco's *
* Technical Advisory Center. Any use or disclosure, in whole or in part, *
* of the IOSv Software or Documentation to any third party for any *
* purposes is expressly prohibited except as otherwise authorized by *
* Cisco in writing. *
**************************************************************************
User Access Verification
Password:
**************************************************************************
* IOSv is strictly limited to use for evaluation, demonstration and IOS *
* education. IOSv is provided as-is and is not supported by Cisco's *
* Technical Advisory Center. Any use or disclosure, in whole or in part, *
* of the IOSv Software or Documentation to any third party for any *
* purposes is expressly prohibited except as otherwise authorized by *
* Cisco in writing. *
**************************************************************************
R1>